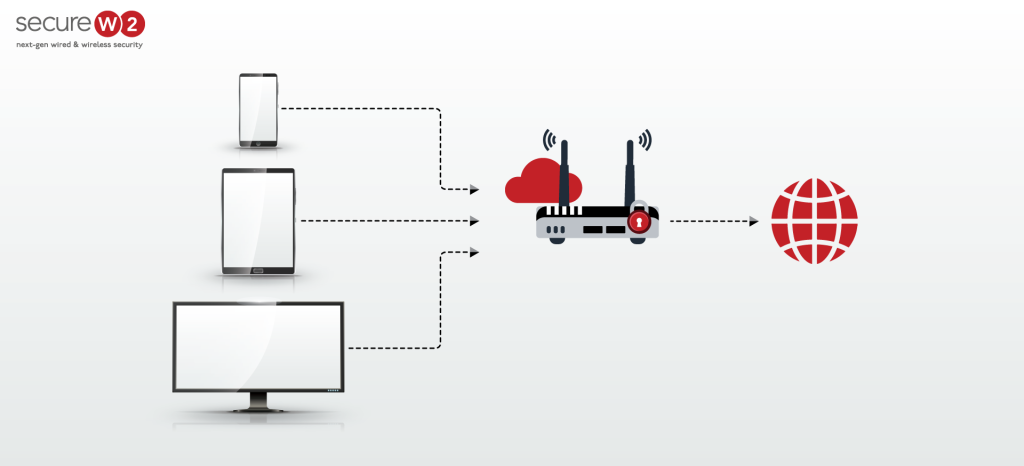
Exploring the Benefits of Cloud 802.1X Security for Modern Enterprises
In modern times, cloud infrastructure is expeditiously superseding on-premise infrastructure as the favoured alternative for numerous enterprises. The myriad benefits of cloud computing are especially evident in the realm of cybersecurity. Due to the escalating need for safeguarded wireless networks, 802.1X authentication has surfaced as the predominant standard for guaranteeing network security. The protocol was […]
Read Story