Imagining a RADIUS server as a guard at a door gives you a high-level overview of how RADIUS authentication works. But it’s a bit more complicated than that, and there are steps involved in the process depending on the authentication protocol your network supports.
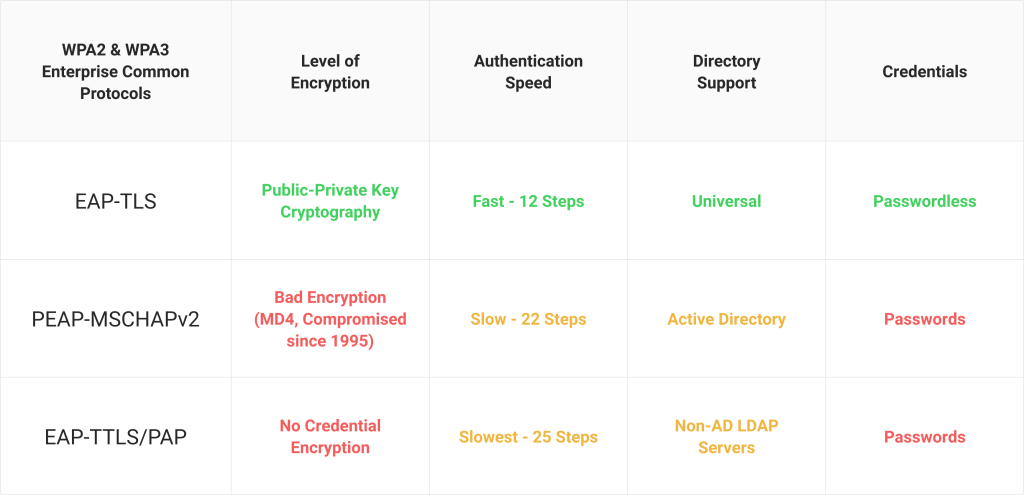
In our experience, three common wireless authentication protocols we see are the following:
- Protected Extensible Authentication Protocol-Microsoft Challenge Handshake Authentication Protocol version 2 (PEAP-MSCHAPv2)
- Extensible Authentication Protocol-Tunneled Transport Layer Security-Password Authentication Protocol (EAP-TTLS/PAP)
- Extensible Authentication Protocol-Transport Layer Security (EAP-TLS)
Each one dictates a different set of standards for the authentication process, including what the user/device provides to verify their identity. You can break down authentication with these protocols into two different categories: authentication via credentials (username/password) and authentication via digital certificates (passwordless).