
WPA2 vs WPA3- The Better Wifi Authentication For You
Wireless network security begins with authentication. The security of a company’s data is ensured when only approved users are able to access the network. Conversely, a network is more vulnerable to attack if improper authentication is used. Different authentication techniques have distinct advantages and disadvantages and a varying range of Wi-Fi security.
The notion of wireless security encompasses the deployment of strategies aimed at thwarting unauthenticated entities from accessing a particular wireless network. The present article aims to provide comprehensive information regarding various types of Wi-Fi authentication and their respective specifications.
Schedule a free consultation call with one of our Wi-Fi security specialists at SecureW2 for a more customized assessment.
Wi-Fi Authentication Types
Pre-shared keys, personal identification numbers, certificate-based authentication, and other methods may be used to limit network access depending on the kind of Wi-Fi connection.
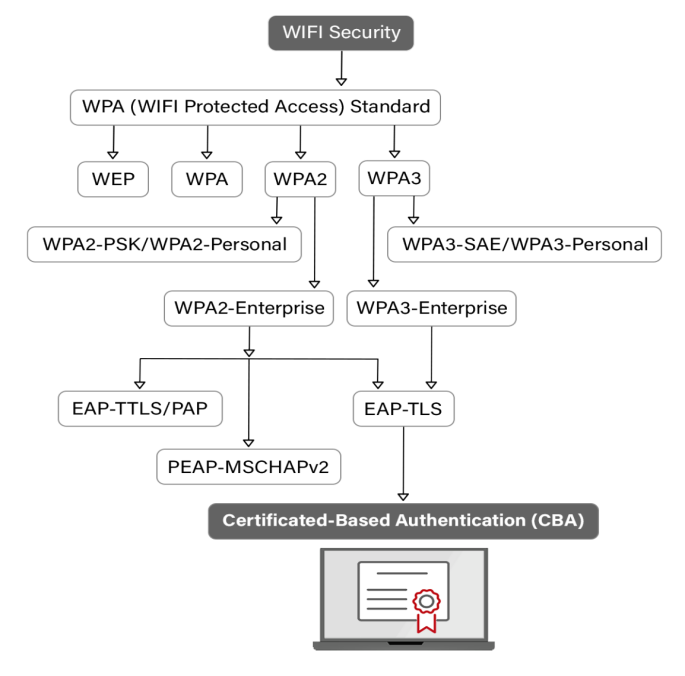
As of today, the below mentioned four wireless security protocols are in operation, each with a different level of strength and usefulness.
- Wired Equivalent Privacy or WEP
- Wi-Fi Protected Access or WPA
- Wi-Fi Protected Access 2 or WPA2
- Wi-Fi Protected Access 3 or WPA3
Wired Equivalent Privacy (WEP)
The WEP protocol was introduced in 1997 as the first security protocol for wireless networking, with an aim to enhance security by encrypting data transmitted over a network. Eventually, WEP was implemented in the 802.11 wireless standards and to encrypt or decrypt data, it used a shared secret key or SSID.
Although, WEP had several security vulnerabilities, however, despite its shortcomings, WEP paved the way for the development of more advanced wireless security protocols known as Wi-Fi Protected Access (WPA) and WPA2.
Wi-Fi Protected Access (WPA)
WPA was developed to supplant WEP in 2003 due to the latter’s vulnerability. The WPA protocol provides enhanced security measures based upon its offering of stronger encryption and authentication mechanisms.
An approach employed to enhance security was the elongation of the encryption key length from 64 bits to 128 bits, thereby rendering the encryption more resilient to malicious attempts at decryption. The enhanced security features of WPA have rendered it the favored option for safeguarding Wi-Fi networks in comparison to WEP.
Wi-Fi Protected Access 2 (WPA2)
The WPA2 security protocol utilizes the RSN (Robust Security Network) and AES (Advanced Encryption Standard) mechanisms as a means of preventing unauthorized access to data. The security protocol presents two discrete modes, specifically WPA2-PSK which employs shared passwords and WPA2-Enterprise that furnishes a more extensive security infrastructure.
In 2004, the TKIP protocol was replaced with a more secure alternative, which has gained popularity as a reliable option for ensuring secure WiFi communication.
WPA2-PSK
WPA2-PSK, or Wi-Fi Protected Access 2 Pre-Shared Key, is a network security protocol that mandates the use of a shared password among all users. The practice of utilizing a single password for Wi-Fi access is generally regarded as a secure measure, subject to the level of trust placed in the users.
In the event that an individual without proper authorization has acquired a password through illicit methods, it is a relatively straightforward process for them to gain access to the network. The perceived lack of security is a commonly cited reason for the perceived unsuitability of WPA2-PSK.
There are just a few scenarios when WPA2-PSK should be implemented:
- A few trustworthy devices on the network, for instance, devices at home or in a small office.
- Devices that are not 802.1X-compliant.
WPA2-ENTERPRISE
The deployment of WPA2-ENT needs a RADIUS server, which authenticates network user access. The authentication method is based on the 802.1x policy and is available in several EAP-labeled systems. A private, encrypted tunnel connects each device to the network post-authentication.
Implementing WPA2-ENT with RADIUS provides maximum network security, mainly when X.509 digital certificates are used for authentication.
WPA2-Enterprise needs an 802.1X authentication server anyway; therefore, implementing the highest level of authentication security during setup is only natural.
Wi-Fi Protected Access 3 (WPA3)
WPA3 is the latest Wi-Fi security protocol that was unveiled in January 2018. The novel protocol exhibits several improvements in security in contrast to its forerunner, WPA2. The aforementioned measures encompass an elevated level of security protocols featuring a 192-bit level of encryption, in addition to reinforced defenses against brute-force attacks. The application of the 802.1X protocol is evident in the two discrete configurations of WPA3, specifically WPA3-PSK and WPA3-Enterprise.
Unfortunately, a considerable number of users are unable to utilize WPA3 due to the lack of compatibility with the majority of devices currently available in the market.
WPA3-PSK
WPA3-PSK provides enhanced security by allowing the authentication procedure to increase PSK’s efficiency. This approach leverages Simultaneous Authentication of Equals (SAE) to make brute-force dictionary attacks far more challenging for hackers.
This protocol requires user input for each authentication attempt, resulting in a considerable lag for brute-force attackers.
WPA3-ENTERPRISE
WPA3-Enterprise’s primary enhancement is its insistence on server certificate validation, which verifies the claimed identity of the server to which a client is connected.
Are you interested in learning more about WPA3? Find out what this article says about the modifications that WPA3 will cause.
WPA2 & WPA3 ENTERPRISE Protocols
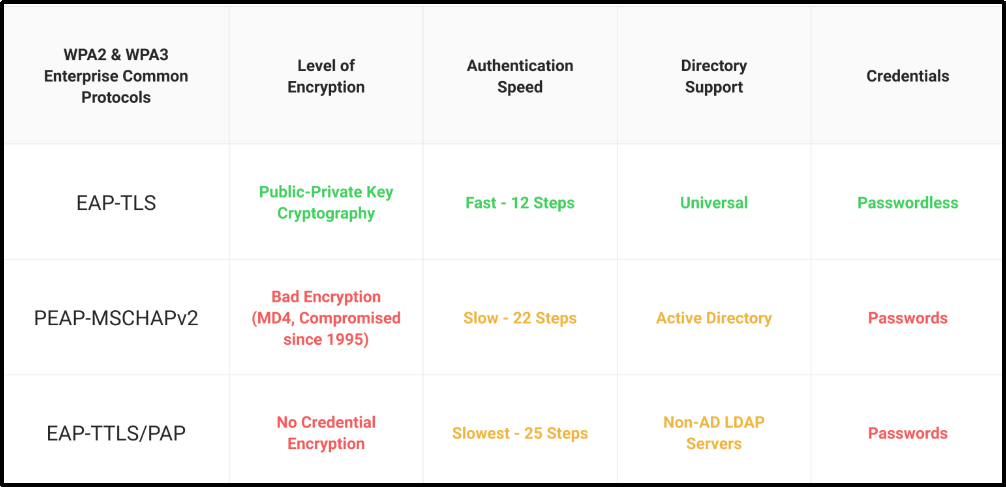
With WPA2-Enterprise, a safe EAP form of authentication is needed. PEAP-MSCHAPv2, EAP-TTLS/PAP, and EAP-TLS are some of the most widely deployed forms. It’s flexible enough to work with a broad range of credentials and supports MFA for added peace of mind.
Typically, when users are added to a network secured by WPA2-Enterprise, they are given a unique identification. While this identification is often a password linked to a specific user, certificates are increasingly being used in place of passwords by many businesses.
Certificates are far superior to passwords. This is because certificates are kept on the device, and the user does not need to manually make any changes to them.
Certificates are comparatively superior to passwords. The certificates are stored on the device and require no manual modification by the user. This stands in opposition to intricate passwords, which necessitate users to commit them to memory and regularly revise them. Upon joining the network, the certificate undergoes immediate validation. The allocation of certificates is device-specific and their transfer or revocation necessitates the authorization of a network administrator. Public key cryptography serves as a safeguard against the utilization of pilfered certificates by malevolent actors. Also, public key cryptography stops attackers from using stolen certificates.
EAP-TLS
EAP-TLS authentication is a method of authentication that relies on digital certificates instead of credentials to verify the identities of users. For further information on EAP-TLS, refer to this article.
EAP-TTLS/PAP
EAP-TTLS/PAP is a credential-based authentication system similar to PEAP and susceptible to the same vulnerabilities as credential-based identification. To read more about EAP-TTLS/PAP, refer to this article.
PEAP-MSCHAPv2
A valid set of credentials is necessary to connect to PEAP-MSCHAPv2. To read more about PEAP–MSCHAPv2, refer to this article.
Managing Wi-Fi With Digital Certificates
Due to the prevalence of passwords, wireless networks often face security difficulties. Passwords inject a human error factor into network security. On the contrary, passwords are susceptible to being compromised through various means such as theft, loss, brute force attacks, or man-in-the-middle attacks.
Certificate-based authentication is among several feasible options. Certificates provide protection to transmitted data through public-private key encryption and authenticate users by implementing the highly secure authentication protocol, EAP-TLS.
Prerequisites for Implementing Certificates
If certificates are so much more secure than passwords, why haven’t more organizations implemented them? The answer, in short, is the complexity of the supporting infrastructure required for their rollout.
A PKI is needed for the generation and upkeep of certificates. Creating a PKI in the past has been time consuming and difficult, and needless-to-say, expensive. However, SecureW2 can provide a straightforward installation that makes running the most secure network easy.
How Can I Secure My Organization’s Wireless Network?
In 2004, the first implementation of WPA2-Enterprise took place. Post which over-the-air encryption and robust security for wireless networks were made available to corporations and universities. The powerful authentication mechanism known as 802.1X has allowed users to access protected networks for many years.
Nevertheless, there may be issues with installing and onboarding new users when utilizing WPA2-Enterprise on a large-scale network.
EAP-TLS and EAP-TTLS/PAP techniques keep data safe throughout wireless transmission but differ in privacy, efficiency, and user-friendliness. In a nutshell, EAP-TLS with certificate-based authentication is safer, better for users, and boosts productivity and security.
SecureW2’s Managed PKI Simplifies Certificate-Backed EAP-TLS
An otherwise conscientious administrator may be dissuaded from implementing the best possible authentication security because of the time and effort required for any customized solution. However, with SecureW2’s Managed PKI Solution, most businesses will likely find the optimal balance between cost and control.
As our turnkey PKI is vendor-neutral and can be integrated into existing network structures, it has the potential to save on setup and maintenance costs. You may also use it straight-from-the-box as a simple plug-and-play network security solution. Our onboarding software is the gold standard in every region, and IT departments love our straightforward, unified management interface.
We have affordable options for organizations of every size. Click here to see our pricing.




