


Cloud RADIUS Built for ABAC
With the advancement of technology, hackers have constantly upgraded their modes of attack and have penetrated almost every industry you can think of. Here’s a recent cyberattack reported by the Department of the Treasury’s Office of Foreign Assets Control (OFAC), sanctioning several individuals and entities involved in the malicious act. It is pretty apparent that […]
Read Story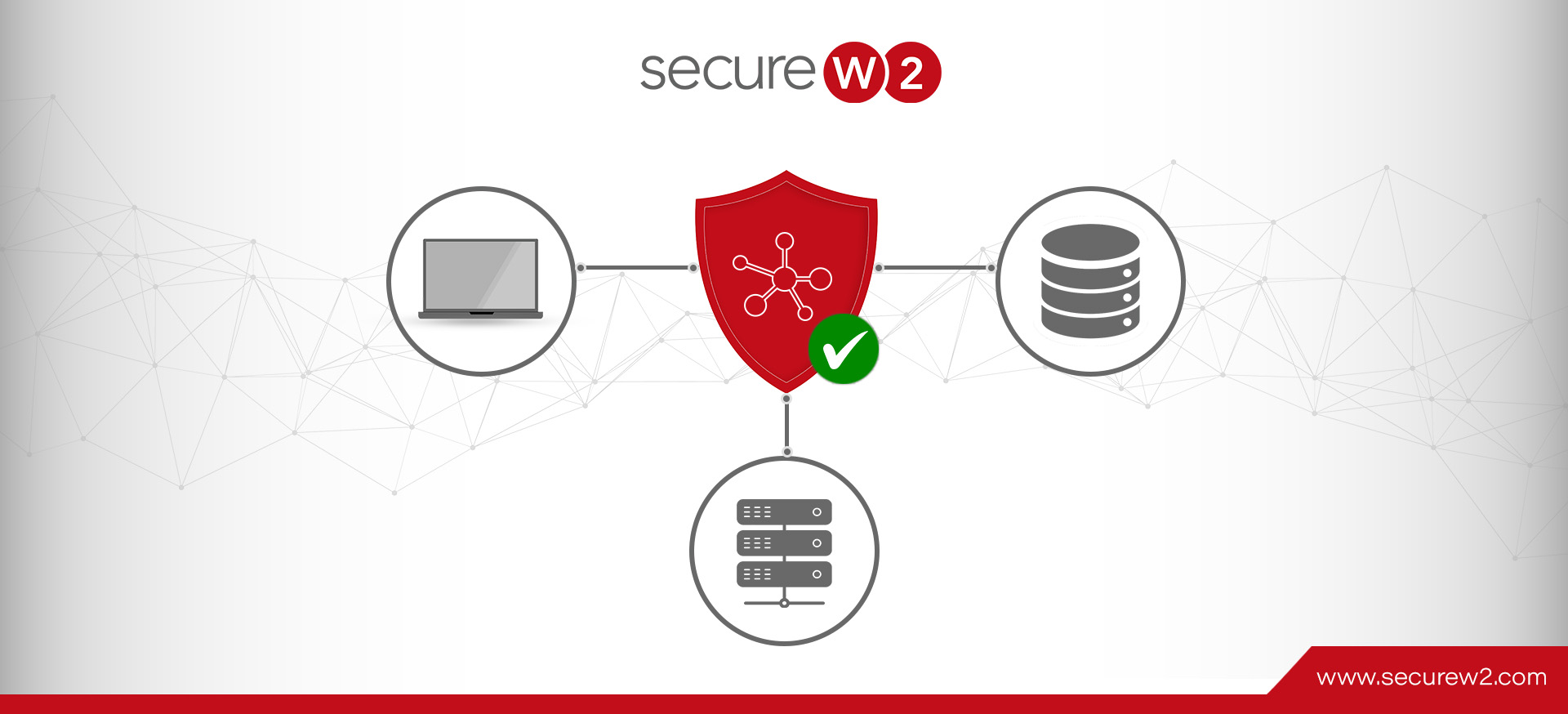
Network Segmentation Tips From the Experts
Get Network Segmentation tips from industry best support team. Read this for great tips from experts!
Read Story
Implement 802.1X for Managed Chromebooks
Secure your Managed Chromebooks with 802.1X certificates to improve network security.
Read Story
RADIUS Change of Authorization: Explained
RADIUS Change of Authorization empowers your RADIUS to dynamically update network access. But how, exactly, does it work?
Read Story
Sync AD to Google for Cloud Authentication
Is managing your K-12 network getting difficult with on-prem Active Directory. This article might help you make the transition to Google Cloud.
Read Story
How to Add Identity Context to RADIUS Auth for ZTNA
Impersonating machines in the digital age is becoming very convenient. Hackers constantly employ these techniques to penetrate the defenses of business networks. Once inside their trusted gadgets, they can travel laterally across systems to steal encrypted data. Here’s a recent cyberattack reported by the Department of the Treasury’s Office of Foreign Assets Control (OFAC), sanctioning […]
Read Story
Best RADIUS Servers for Enterprise
As the size of your network increases, so does the number of vulnerabilities. Finding a good enterprise RADIUS server will help protect your network.
Read Story
Can a RADIUS Server Authenticate a VPN
VPNs have become an important feature for many organizations due to the Covid-19 pandemic. Set up secure VPN authentication for your users using RADIUS.
Read Story
RADIUS Wi-Fi Authentication with Multiple Domains
Using a single RADIUS server to authenticate across multiple domains is possible - and even easy.
Read Story