
Resolve Wi-Fi authentication error- Security Key Incorrect.
Solved Wi-Fi authentication Error, Security Key Incorrect. Here are some easy fixes.
Read StoryRADIUS security news and updates from the Cloud RADIUS team.

Solved Wi-Fi authentication Error, Security Key Incorrect. Here are some easy fixes.
Read Story

Security Error Untrusted Server Certificate is hurting your online presence? Check out this article for solutions.
Read Story
Network Policy Server (NPS) is Microsoft’s RADIUS server option, controlling network authentication, authorization, and accounting. It offers a centralized mechanism for implementing network security regulations and is commonly used by enterprises to guarantee that only authorized people and devices may access network resources. Through its integration with Active Directory, network-wide user authentication is made simple. […]
Read Story
FreeRADIUS is the foundation of many DIY RADIUS servers around the world, but the lack of a graphical user interface (GUI) makes it tough to manage. Here are your options.
Read Story
Wireless encryption standards have developed to account for shifting network needs, emerging security threats, and discovered flaws in older encryption methods. WPA2-PSK/Personal and WPA2-ENT are the two variants of the WPA2 protocol that are in use today and provide different levels of security. WPA2 Enterprise uses IEEE 802.1X to deliver enterprise-grade authentication, and it was […]
Read Story
Simple Certificate Enrollment Protocol (SCEP) is a standard for certificate management. SCEP is predominantly used for certificate-based authentication. A Mobile device management (MDM) solution uses SCEP to push the payload that houses the SCEP URL and the shared secret to managed devices in the network. The significant advantages of certificate-based authentication are: Jamf is a […]
Read Story
Organizations are looking at ways to protect their network as increased cyber attacks are infiltrating complex network systems. The rapid growth of artificial intelligence has also led to a steep rise in the number of complex attacks being attempted on organizational networks. It is becoming increasingly difficult for administrators to view the users and devices […]
Read Story
Secure your organizations network from hacking and vector attacks. Read on to find out more!
Read Story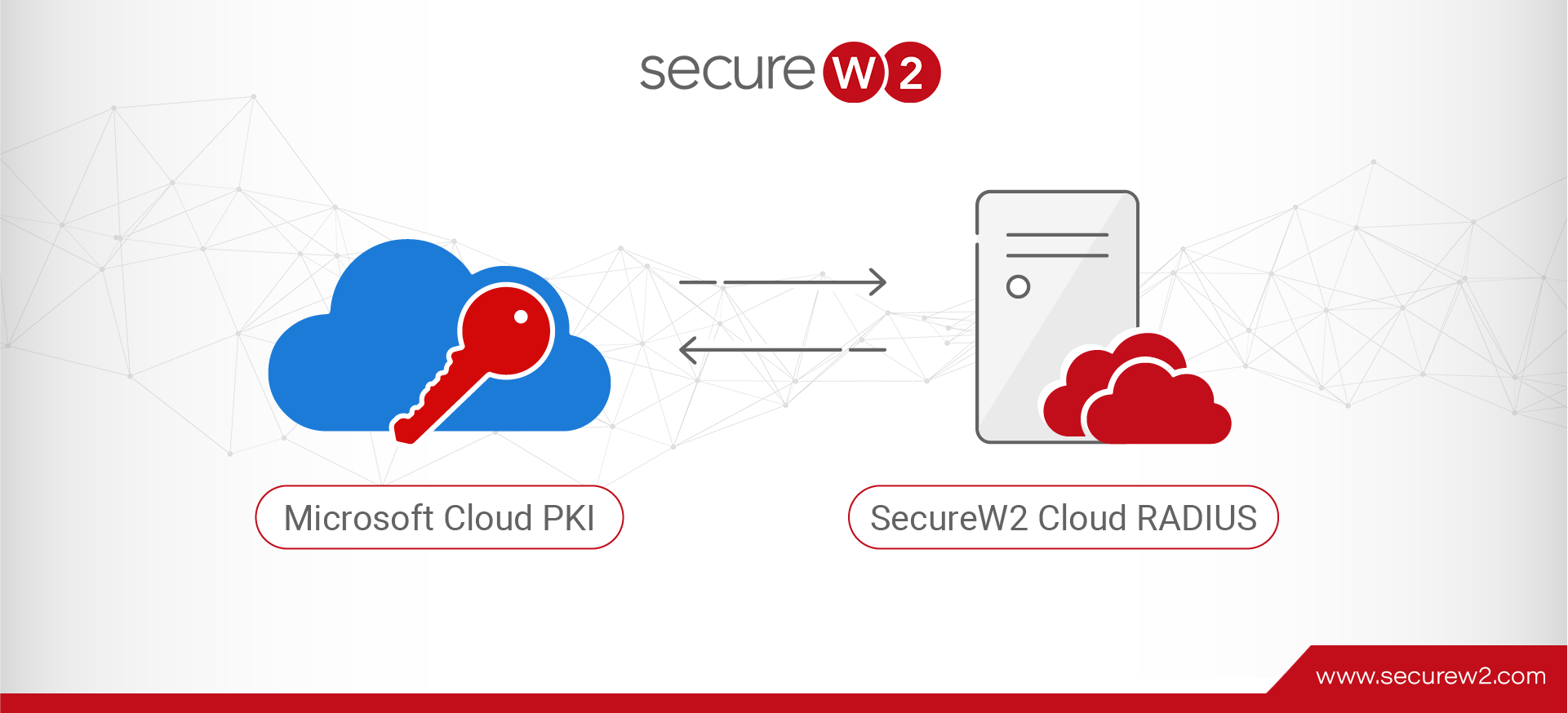
Microsoft Cloud PKI, a recent addition to Intune suite of services, enables organizations to issue certificates to Intune-managed devices. We at SecureW2 have been advocating for certificate-driven authentication for more than a decade, and are really excited about Microsoft’s new PKI enabling certificate authentication for many small organizations that historically couldn’t leverage certs. However, as […]
Read Story