Introduction
Using SecureW2’s WPA2-Enterprise Onboarding Software and PKI Services with your Extreme Networks Access Points can vastly improve network security, user experience, and significantly reduce the number of Wi-Fi-related support tickets received. It enables organization’s to easily adopt certificate-based network authentication, and replace Wi-Fi passwords.
Credential-based authentication is vulnerable to over-the-air credential theft, and creates a really poor end user experience with the necessity of password-change policies.
SecureW2 streamlines 802.1x authentication management, which allows easier device monitoring for admin. End users can enroll for a certificate and self-configure their devices in minutes. Plus it’s authenticated for as long as the certificate is valid, so end users don’t have to reconfigure their devices every couple of months like they have to with passwords.
This guide will cover how to integrate SecureW2 with the Extreme Networks ECA, so organizations can easily support EAP-TLS certificate-based 802.1x authentication.
Tech Overview
- Configuring SecureW2 PKI services
- Deploying and maintaining a PKI isn’t easy, that’s why SecureW2 offers turnkey cloud-based PKI services to make it incredibly easy to support certificate-based authentication.
- Configuring SecureW2’s RADIUS to ECA
- SecureW2’s cloud-based RADIUS server can integrate with any software, doesn’t require major overhaul, and is great for clients who don’t want additional infrastructure.
- SecureW2’s PKI Services integrate with any RADIUS Server as well if you have existing infrastructure.
- SecureW2’s cloud-based RADIUS server can integrate with any software, doesn’t require major overhaul, and is great for clients who don’t want additional infrastructure.
- Configuring Secure SSID as WPA2-Enterprise EAP-TLS
- Many have thought that EAP-TLS was too difficult to deploy. SecureW2 shows that not only does EAP-TLS credential-based authentication provide better network security, it can be set up in a matter of hours rather than days.
- Configure ECA’s Onboarding SSID
- Once you’ve configured the settings, SecureW2 allows you to customize a landing page and SSID for devices to be properly onboarded and authenticated.
Prerequisites and Limitations
- A SecureW2 Network Profile configured for EAP-TLS
- An ExtremeCloud Appliance (ECA)
- An Extreme Access Point compatible with ECA (this guide uses a AP3915i)
Integrating the SecureW2 Cloud RADIUS
- From the left-hand side pane, navigate to ONBOARD > AAA
- Under RADIUS Servers, click the Add button on the Default AAA Configuration page
- Configure the following parameters for the SecureW2 RADIUS server
- RADIUS Server IP address <SecureW2 RADIUS IP Address>
- Authorization Client UDP Port <SecureW2 RADIUS Port>
- Shared Secret <SecureW2 RADIUS Shared Secret>
- Click on the Save button on the top right-hand side
- This process needs to be repeated, so both the Primary and Secondary IP Addresses are added
Creating an WPA2-Enterprise Onboarding SSID
- Navigate to Networks > Add
- Configure the following parameters:
- Network Name – Example: Onboard
- SSID – Enter a character string to identify the wireless network
- Status – Enable the network service
- Auth Type – Open
- Enable Captive Portal – Check this option to enable captive portal support
- Captive Portal Type – Select External
- ECP URL – URL address of the SecureW2 network profile
- Walled Garden Rules – Click Walled Garden Rules to configure policy rules for the external captive portal
- Click on L3,L4 Rules (IP and Port) Rules(0 Rules) > New
- Create entries to allow end-user devices to reach SecureW2 servers, Google Play Store, and for disabling CNA browsers
- For a full list of resources to allow in the Walled Garden, please refer to the SecureW2 JoinNow Configuration Guide in the Management Portal
- Click Save
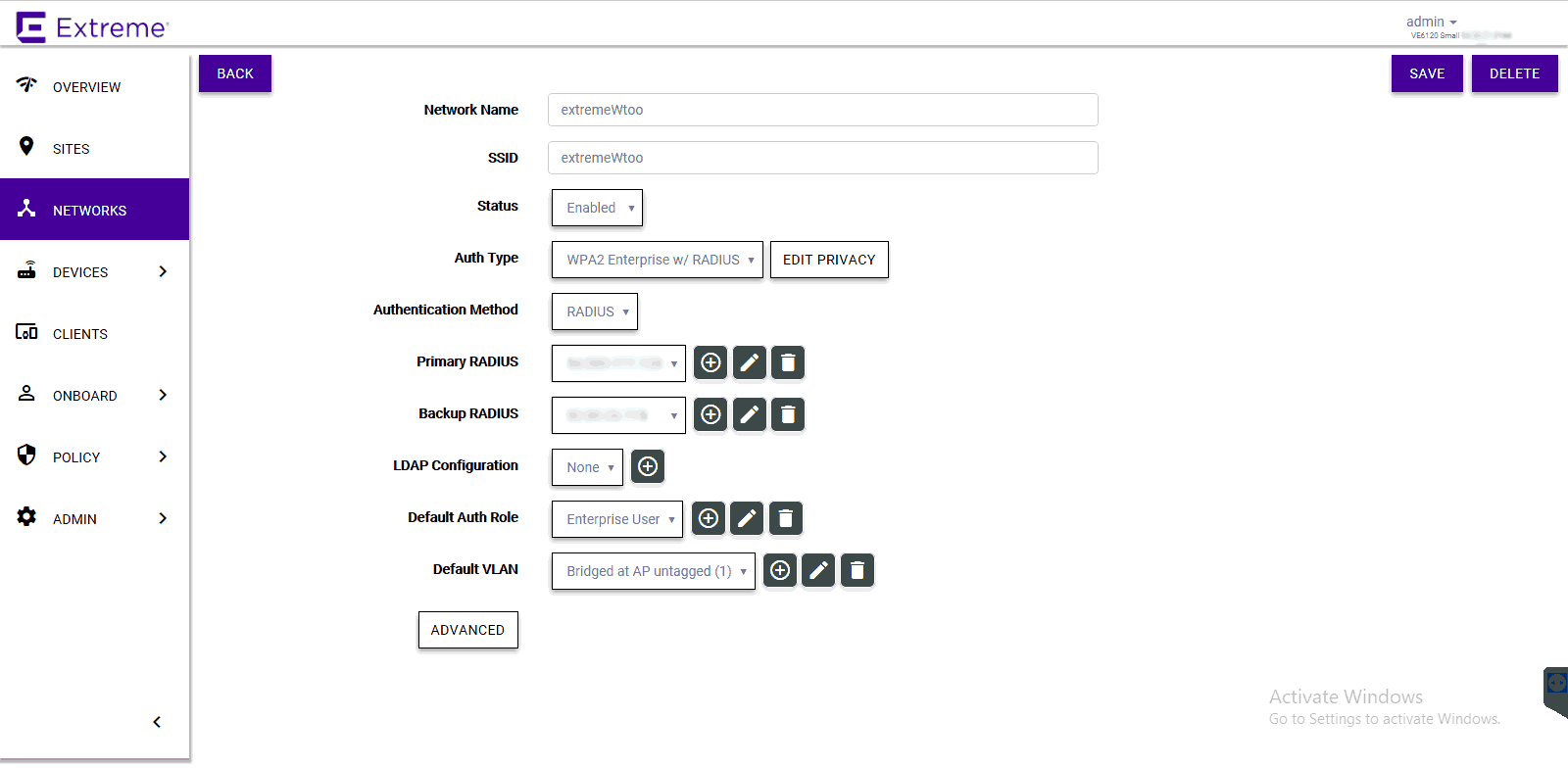
Configure the WPA2-Enterprise Secure SSID
- Navigate to Networks > Add
- Configure the following parameters:
- Network Name – Example: SecureSSID
- SSID – Enter a character string to identify the wireless network
- Status – Enable the network service
- Auth Type – WPA2 Enterprise w/ RADIUS
- Authentication Method – RADIUS
- Primary RADIUS – SecureW2 RADIUS IP Address added earlier
- Backup RADIUS – Other SecureW2 RADIUS IP Address added earlier
- Default Auth Role – Select Enterprise User
- Default VLAN – Select a VLAN
- Click Save
Assigning the Configured Networks to a Site
- Go to the Sites tab and select the preferred site that is already configured
- Click Configure Site
- Click the Device Groups tab and select a device group
- Click on the Profile field to edit the device group profile
- Go to the Networks tab and select the configured network
- Go to the Roles tab and select the previously configured roles
-
- Click Ok > Save
Once that’s finished, you’re all set!
Ready to get started configuring your ECA for EAP-TLS? SecureW2 has affordable options for organizations of all shapes and sizes. Click here to check out our pricing form.