
Use Azure, Okta, and Google for Network Authentication
Cloud RADIUS is the industry’s only passwordless authentication solution, designed to work natively with cloud Identities like Azure, Okta and Google. No LDAP or AD servers required.
- Enforce Policies with Real-Time OAuth Lookup against Azure, Okta, & Google Workspace.
- Dynamically assign appropriate network security based on user, group, attributes, and device policies for Wi-Fi, Wired, ZTNA and VPN.
- 100% passwordless, no more LDAP/Directory dependence.
Designed for Passwordless Certificate-Based Security
Available with a full-suite Public-Key Infrastructure (PKI), Cloud RADIUS was designed to be a turnkey passwordless authentication platform.
- Eliminate the risk of Wi-Fi being used to steal cloud identities via Evil Twin and Man-in-the-Middle Attacks
- Prevent phished credentials from being used to access your network
- Improve user experience with faster connections, better Wi-Fi roaming, and no more password-reset disconnects
- Everything you need for EAP-TLS 802.1x authentication, recommended by industry titans such as Microsoft. NSA, CISA, and Google
MDM Integration via Gateways for Corporate and IoT Devices
Certificate-based authentication needs a simple zero-touch approach for distribution and renewal. Use your device management platforms (including IoT) and MDM / EMM platforms via robust APIs to distribute and manage certificates.
- Extensive APIs including SCEP, JSON, WSTEP, EST, and more
- Proven integration with all major MDMs including Jamf, Workspace One, Soti, Mosyle, MobileIron, Meraki, and many more
- Enhanced MS Intune integration with enhanced policy and lifecycle management
- Enhanced Google Workspace integration for zero-touch Chromebook provisioning
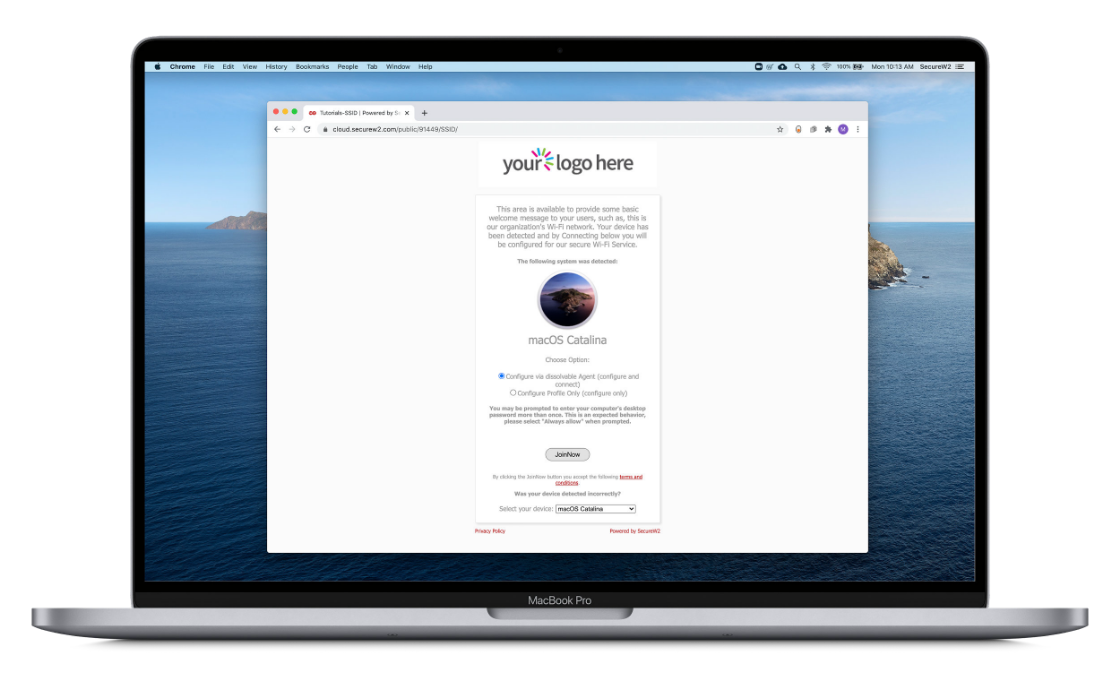
802.1X Setup Software Available for All Operating Systems
Lock down BYOD and unmanaged devices with the #1 rated 802.1x Onboarding Software. Ensure every device is properly configured to authenticate against Cloud RADIUS.
- Device configuration software to ease user burden and errors while improving security
- Provision certificates and device configuration (Wi-Fi/VPN/etc) in just a few clicks
- Connect devices to networks and provide reporting, device analytics, and remote troubleshooting data.
- All instructions and CSS Completely Customizable
- Support for iOS, Windows, macOS, Android, ChromeOS, Linux, and Kindle
Security at Lightning Speed with Real-Time Intelligence (RTI)
With Cloud RADIUS, you can rest assured that devices are removed from your network the instant your policies determine so. Instead of depending on Reauthentication timers, Real-Time Intelligence technology proactively revokes network connectivity instantly and is always synced with your Cloud Identity.
Service Across the Globe, Designed for Roaming
With international support, and capable for OpenRoaming and Passpoint, Cloud RADIUS gives you an advanced foundation for authentication.
- Service Regions include North and South America, Europe, Oceania, and Asia-Pacific
- Passpoint and OpenRoaming enabled; The only Cloud RADIUS part of the Wireless Broadband Alliance
- Further reinforce your authentication security with RADIUS over TLS (RadSec) support.
Single-Pane AAA, Device Onboarding and Certificate Management Software
Cloud RADIUS is built-in SecureW2’s network security platform, giving full, single-pane visibility into all the authentication activity going on to the network.
- Single-pane management for RADIUS, PKI, and Device Onboarding
- View RADIUS event logs, WPA2-Enterprise device configuration history, and certificate enrollment and status in real-time
- Grant different permissions for IT personnel to remotely troubleshoot network connectivity issues on the spot
See Why Everyone’s Moving to CloudRADIUS
