Introduction
With a growing number of organizations utilizing Google Workspace for its solutions that improve collaboration and productivity, it is critical to ensure that network resources are accessed securely and effectively. Network security may be significantly enhanced using a solid authentication system like RADIUS (Remote Authentication Dial-In User Service) with Google Workspace. Centralized authentication, authorization, and accounting are made possible via a Google Workspace RADIUS server, which simplifies the administration of user credentials and access restrictions. Businesses may reduce the risk of illegal access and data breaches by integrating RADIUS with Google Workspace to guarantee that only authorized users can access vital network resources.
Furthermore, sensitive data is better protected because of cutting-edge security protocols like RadSec (RADIUS over TLS) integration in Google Workspace RADIUS solutions. RadSec protects credentials during the authentication process by encrypting communications between RADIUS clients and servers. Organizations may build a highly secure environment where every device must authenticate before entering the network by combining 802.1x, a network access control standard, with other security measures. In addition to strengthening network security, this layered security strategy—backed by SecureW2’s Cloud RADIUS solution—ensures smooth integration with Google Workspace and offers a scalable and trustworthy authentication framework for contemporary businesses.
Integration Process Overview
- Create a SAML Identity Provider in SecureW2
- Configure the SAML IDP in Google Admin Console
- The SAML Identity Provider provides context concerning who is connected to the network and ensures that only approved network users are authenticated.
- Configure Attribute Mapping
- Set specific attributes to segment the network into groups based on their identity within the organization.
- Configure Network Policies to be Distributed
- Based on these network policies, administrators can dictate the websites, applications, files, and more that different network user segments are able to access.
- Setup RADIUS Lookup
- We can create an OAuth application in Cloud RADIUS to perform a real-time lookup with Google Workspace. This will allow us to perform an additional security check, as well as revoke certificates and network access in real-time.
Configuring Google Workspace
Integrating SecureW2 with Google Workspace is necessary to simplify user authentication and improve network security. This section will show you how to use the Google Developer Console to configure SecureW2 with Google Workspace. Setting up OAuth consent and generating the required credentials guarantees smooth interaction with Google Workspace RADIUS and Google Workspace RadSec for reliable 802.1x authentication. Follow these precise instructions to safeguard your organization’s network access effectively.
- Open your Google developer console: https://console.developers.google.com
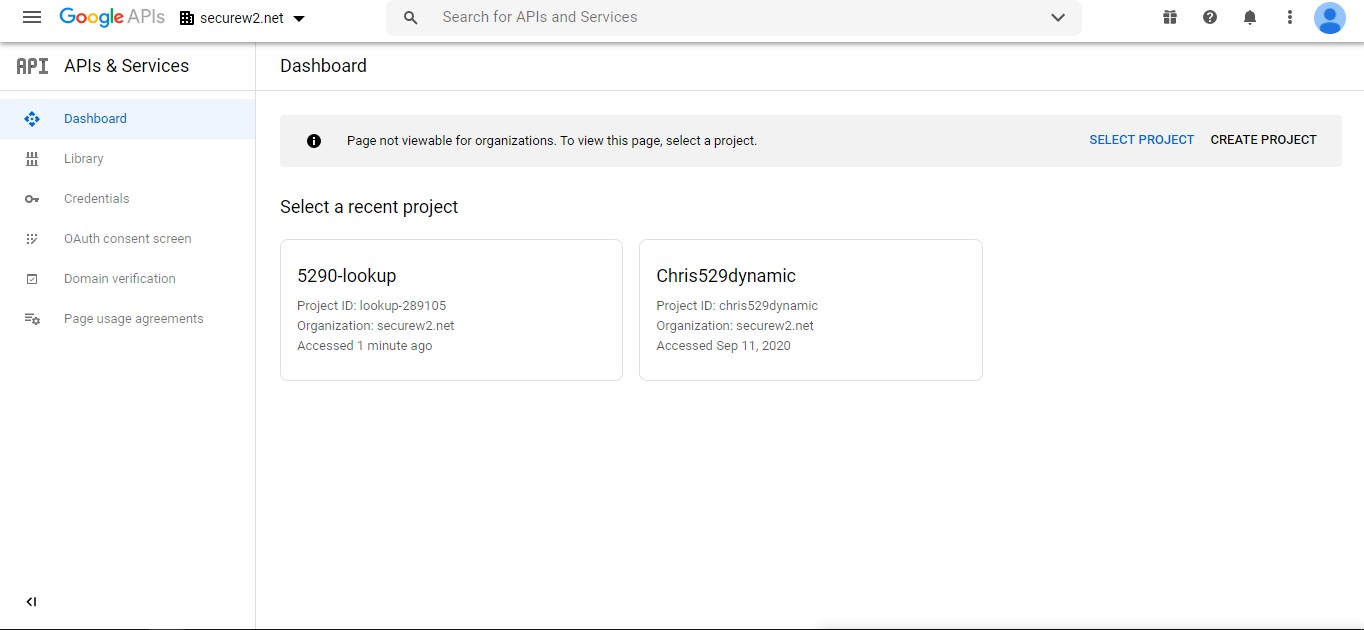
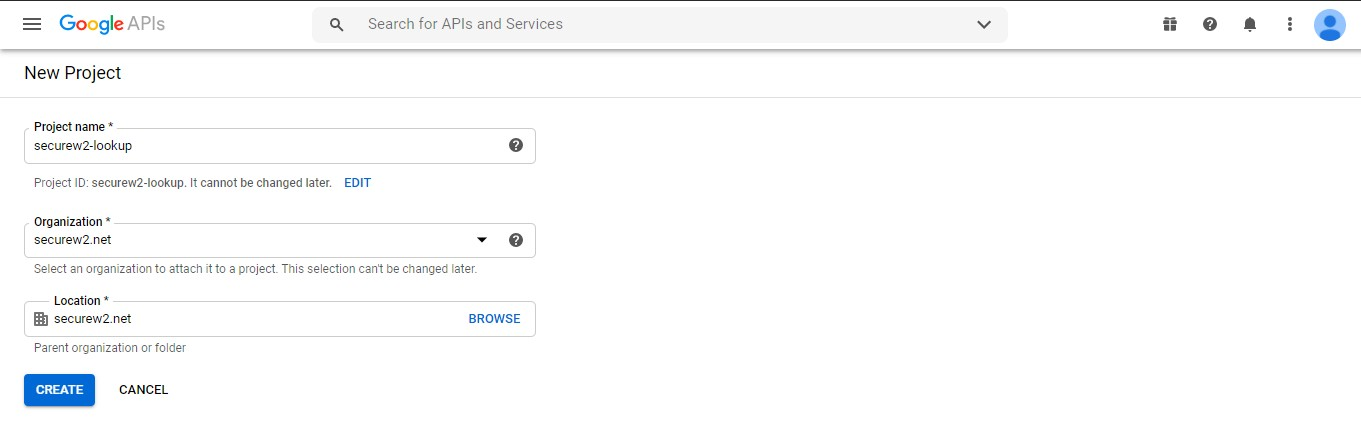
- Select the right project. Or, create a new project as shown in the following screen.
- Provide the Project name, Organization, and Location. Then, click Create.
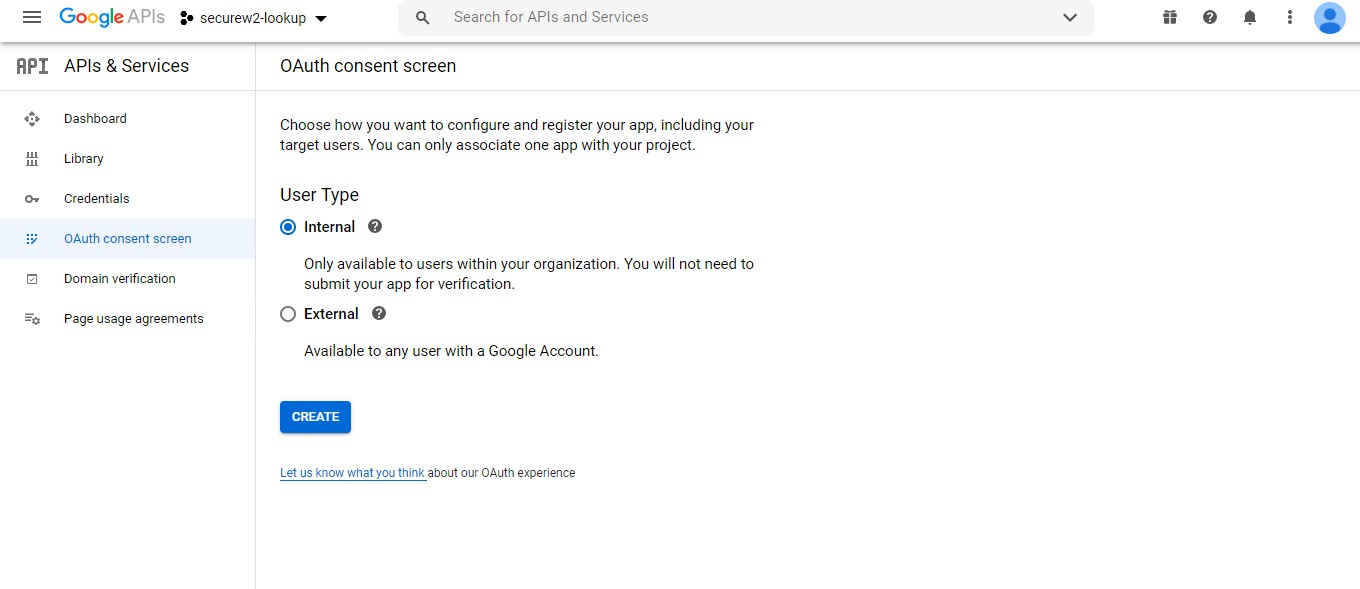
- To create a OAuth consent, click OAuth consent screen in the left menu. The following screen is displayed.
- Select Internal, then click Create. The following screen appears:
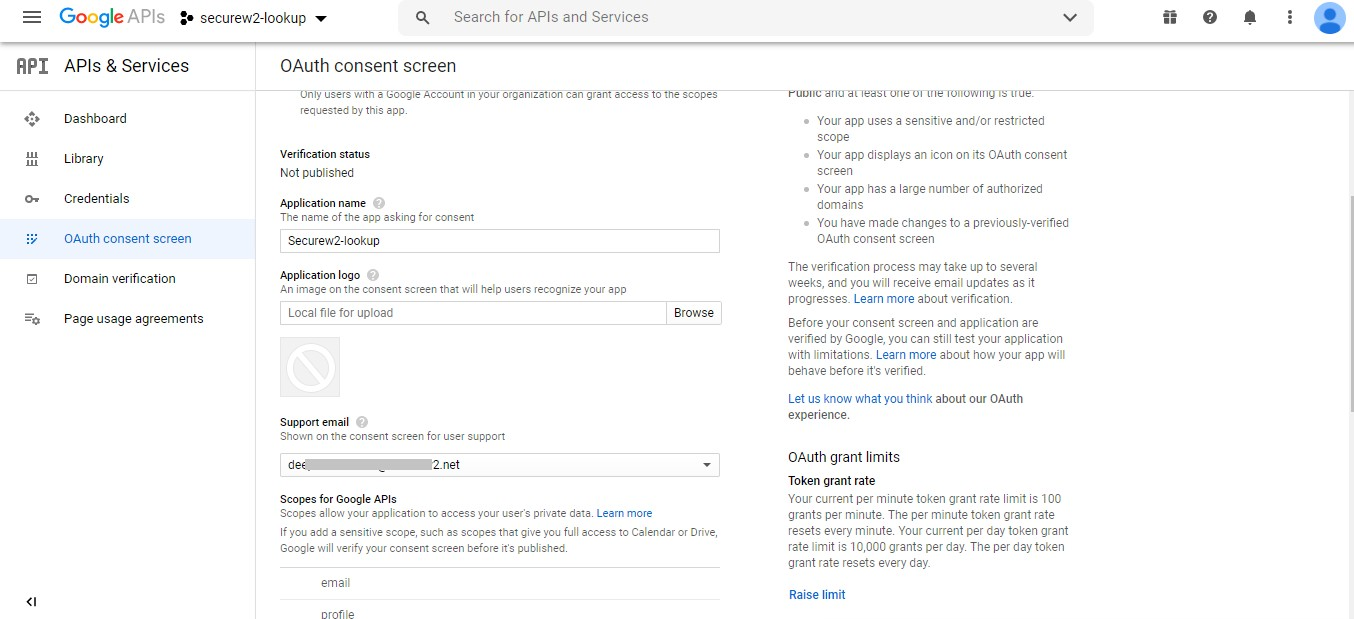
- Provide the Application name, Application logo, and Support email. Then, click Save.
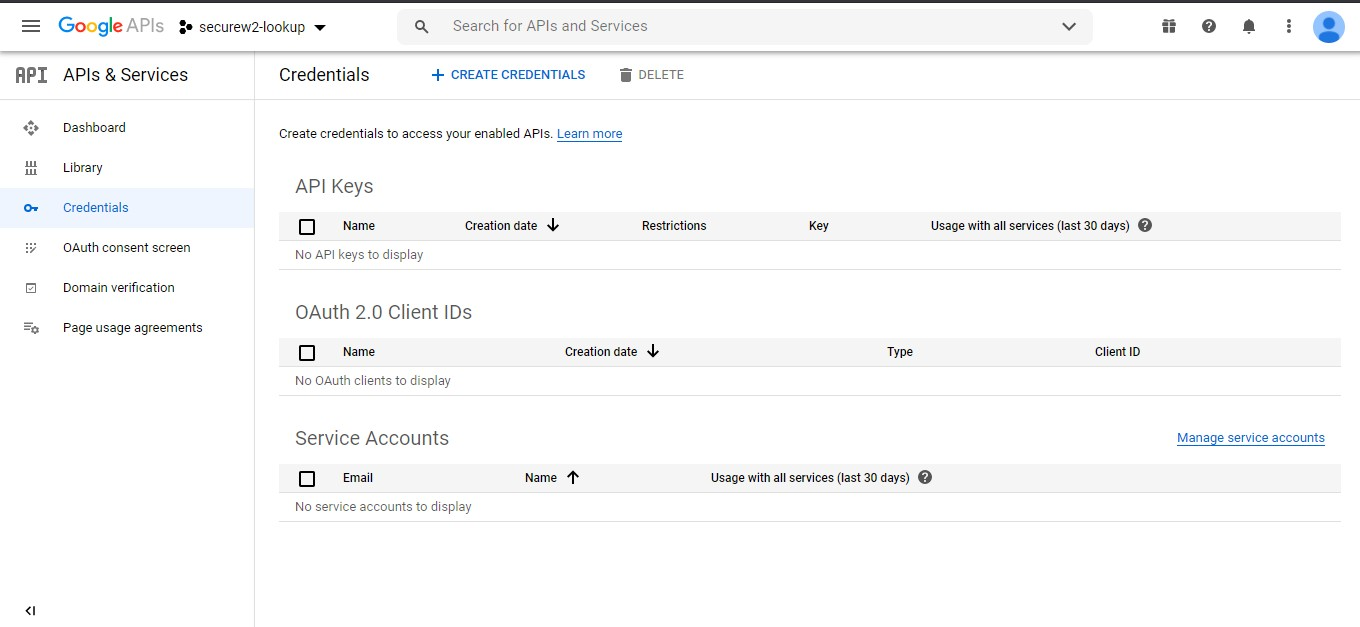
- Click Credentials in the left menu. The following screen appears.
- Click Create Credential > OAuth client ID. The following screen appears:
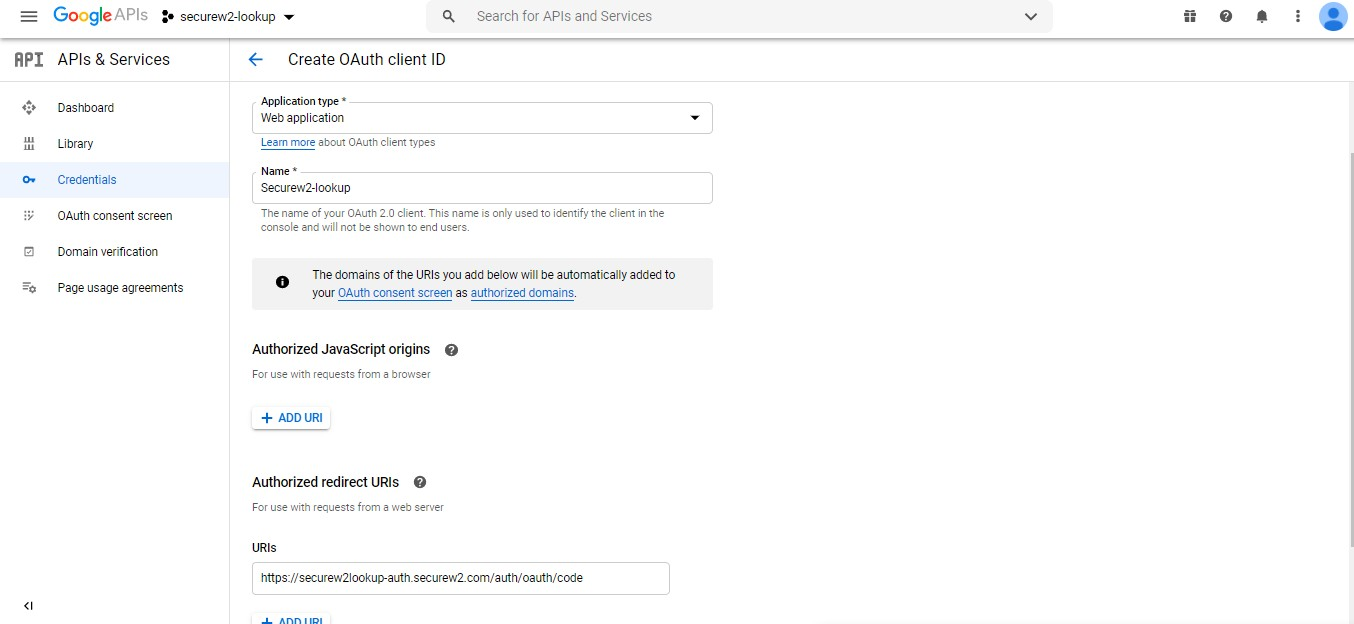
- From Application type, select Web application.
- Under Authorized redirect URIs, add the Authorization Portal redirect URI. You can get this Redirect URI from the JoinNow Management Portal while configuring the Google Workspace Identity Lookup.
For example, https: /<orgidentifier>.securew2.com/auth/oauth/code. - Click Update. The following screen is displayed.
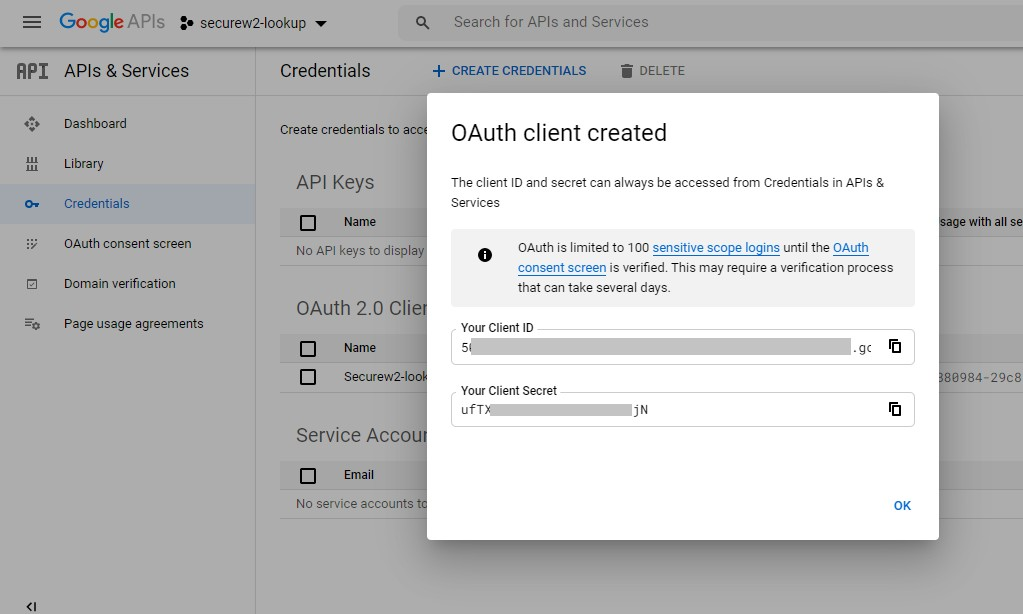
- Copy the Your Client ID and Your Client Secret values and save for later.
- To enable the Admin SDK service, navigate to Dashboard and click ENABLE API AND SERVICE.
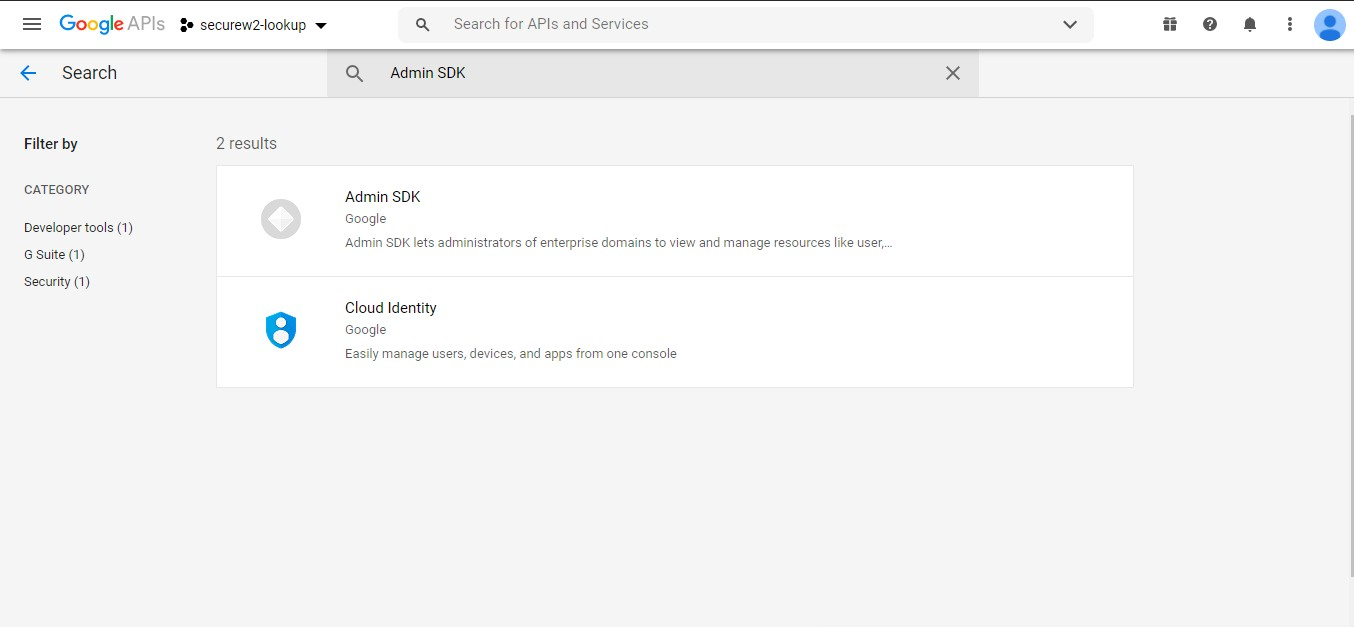
- Search for Admin SDK.
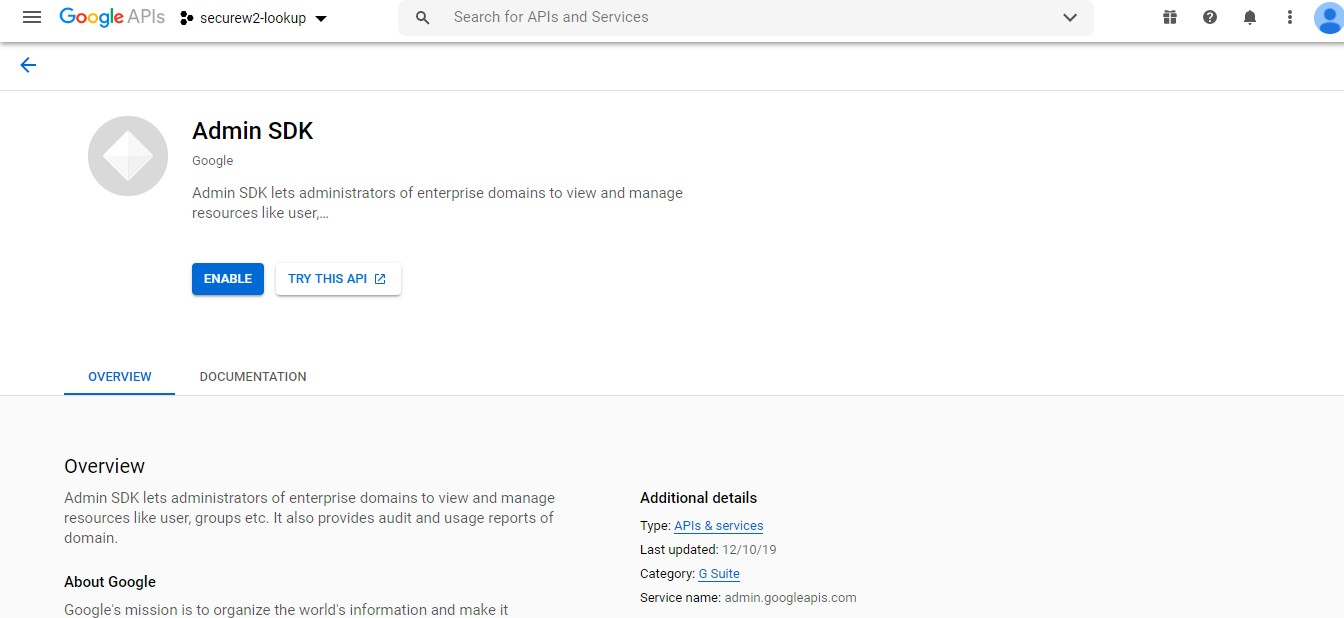
- Open Admin SDK. The following screen appears:
- Click Enable.
NOTE: The Authorize feature allows you to test Google is setup properly to work with SecureW2. You can use this feature after you configure an Identity Lookup Provider in the next part of the documentation.
Configuring SecureW2 for Google Workspace
To improve network authentication, you must configure an Identity Lookup Provider and user and group policies while configuring SecureW2 for Google Workspace. Using the Getting Started Wizard, you will create a RADIUS server, Network Profiles, and the configurations for 802.1x Google Workspace integration. Using Google Workspace RadSec for secure authentication, this part explains how to construct an Identity Lookup Provider, map characteristics, define groups, and apply policies to guarantee smooth communication between SecureW2 and Google Workspace RADIUS Server. To appropriately streamline and protect your network access, adhere to these requirements.
Getting Started
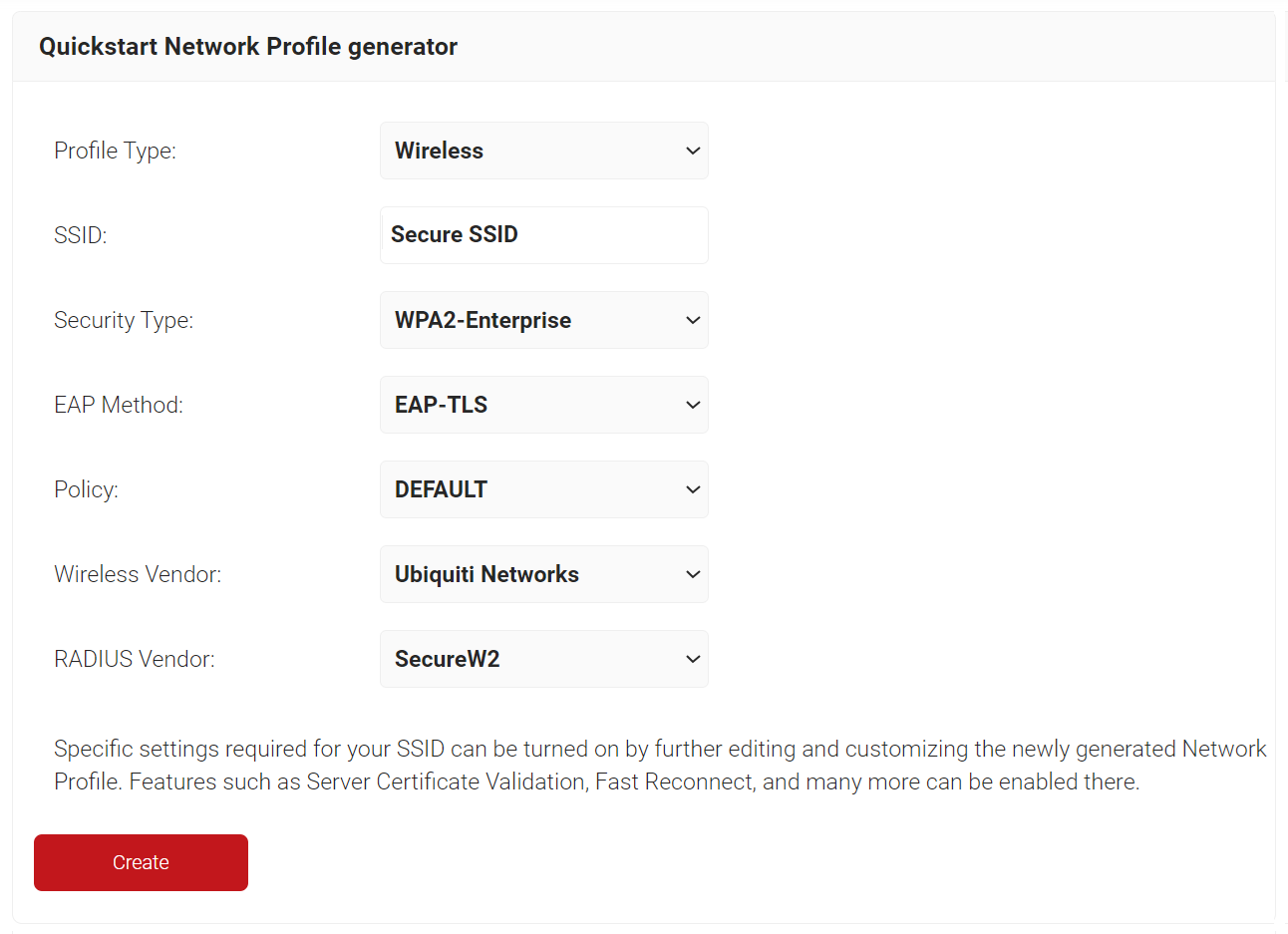
The Getting Started Wizard creates everything you need for 802.1x. It will generate a RADIUS Server, Network Profiles, a Landing Page for Device Onboarding, and all the default network settings you will need for 802.1x.
NOTE: If you have already configured SecureW2 for your network, you may skip this step.
- Navigate to Device Onboarding > Getting Started.
- On the Quickstart Network Profile generator page, from the Profile Type drop-down list, select Wireless.
- In the SSID text box, enter an SSID name.
- From the Security Type drop-down list, select WPA2-Enterprise.
- From the EAP Method drop-down list, select EAP-TLS.
- From the Policy drop-down list, retain DEFAULT.
- From the Wireless Vendor drop-down list, select a vendor.
- From the Radius Vendor drop-down list, select a RADIUS vendor.
- Click Create. It takes 60-90 seconds for the process to complete.
Creating an Identity Lookup Provider
During the RADIUS authentication process, Identity Lookup validates that a user is active within the organization by checking the identifying information against the existing users in the Identity Provider. Here we will create an Identity Lookup provider in SecureW2 so we can connect our Identity Provider to lookup users, groups and their devices.
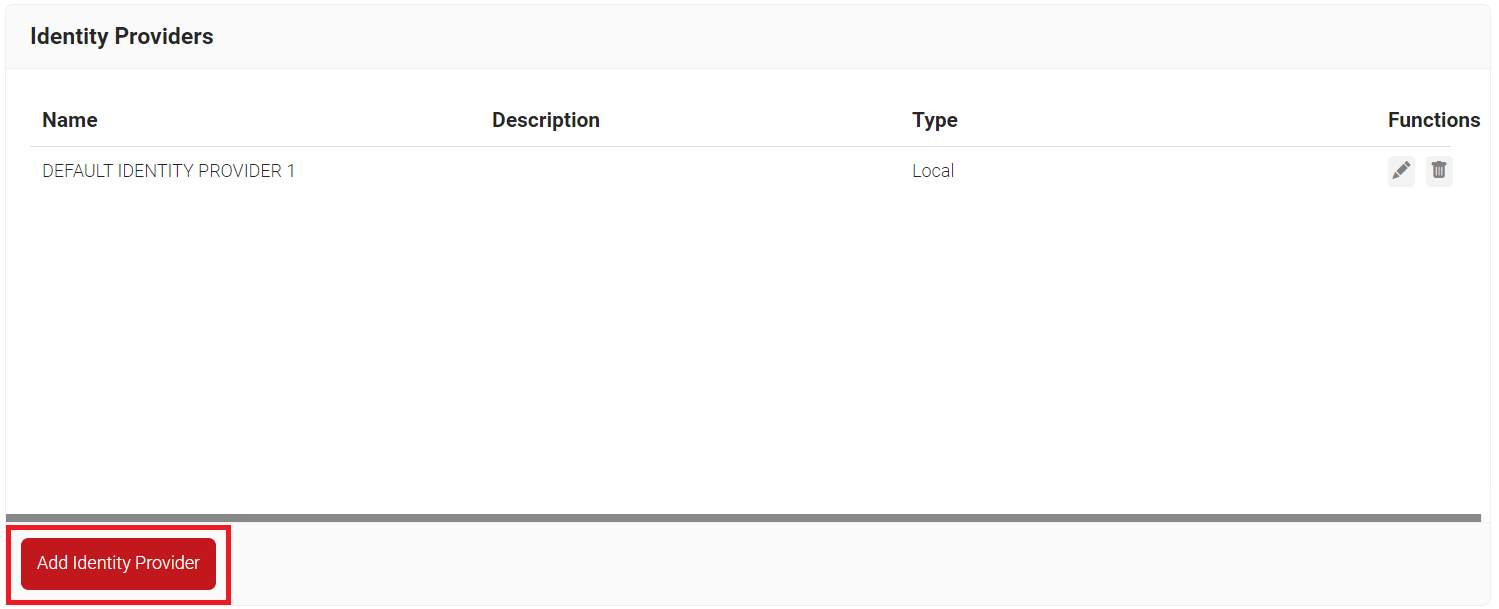
- Log in to the JoinNow MultiOS Management Portal.
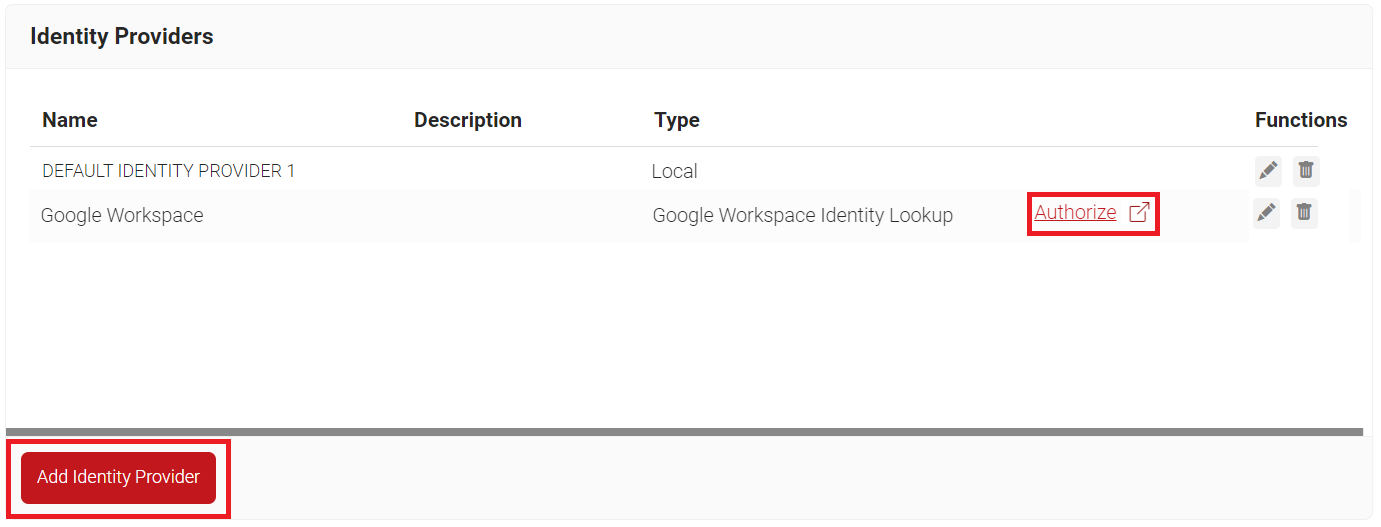
- Navigate to Identity Management > Identity Providers.
- Click Add Identity Provider.
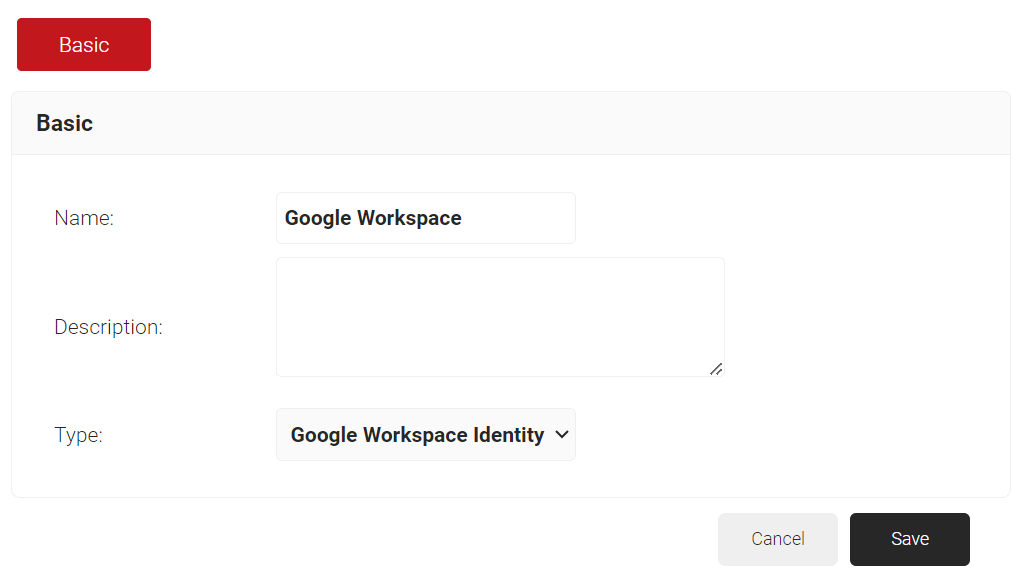
- In the Name field, enter the name of the Identity lookup provider.
- In the Description field, enter the suitable description for the Identity lookup provider.
- From the Type drop-down list, select Google Workspace Identity Lookup.
- Click Save.
- The page refreshes and displays the Configuration, Attribute Mapping and Groups tabs.
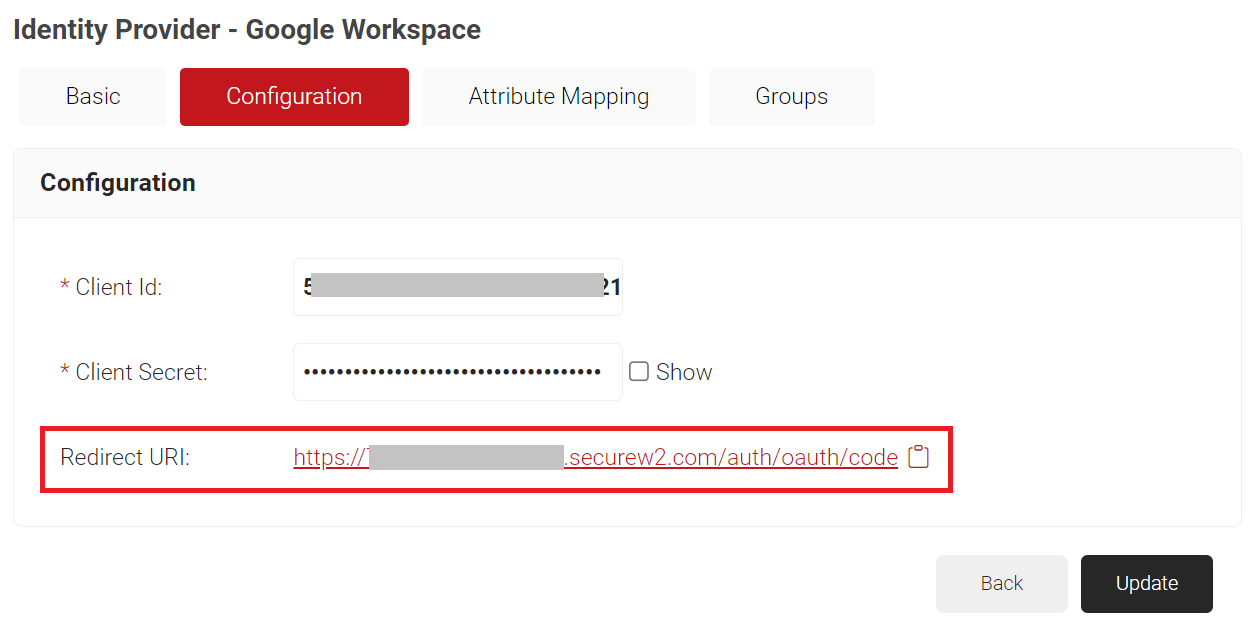
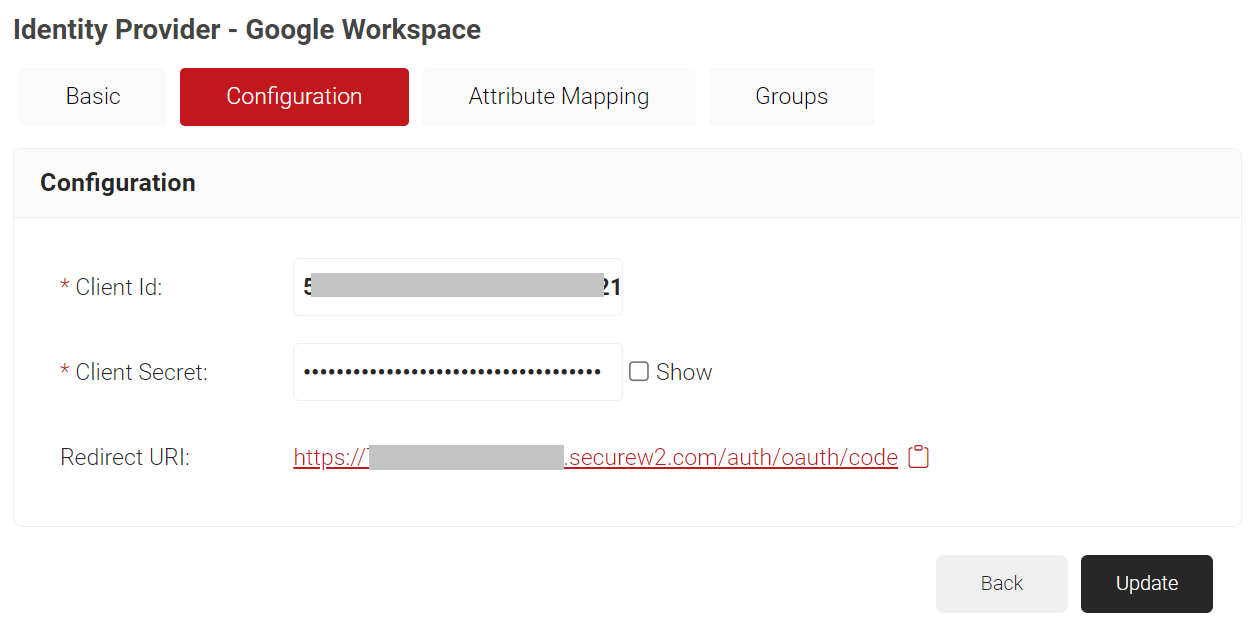
- Select the Configuration tab.
- Under the Configuration section, provide the following information.
- In Client Id, enter the client Id that you retrieved from Google Workspace (refer the Configuring Google Workspace section, step 12).
- In Client Secret, enter the client secret you generated in the Google Workspace (refer the Configuring Google Workspace section, step 12).
NOTE: After updating the Identity Provider, this secret will not be retrievable. Therefore, make sure this is saved in a secure place. - Click Update.
- Click Authorize on your new Google Workspace Identity Lookup. This will test the connection between SecureW2 and Google Workspace.
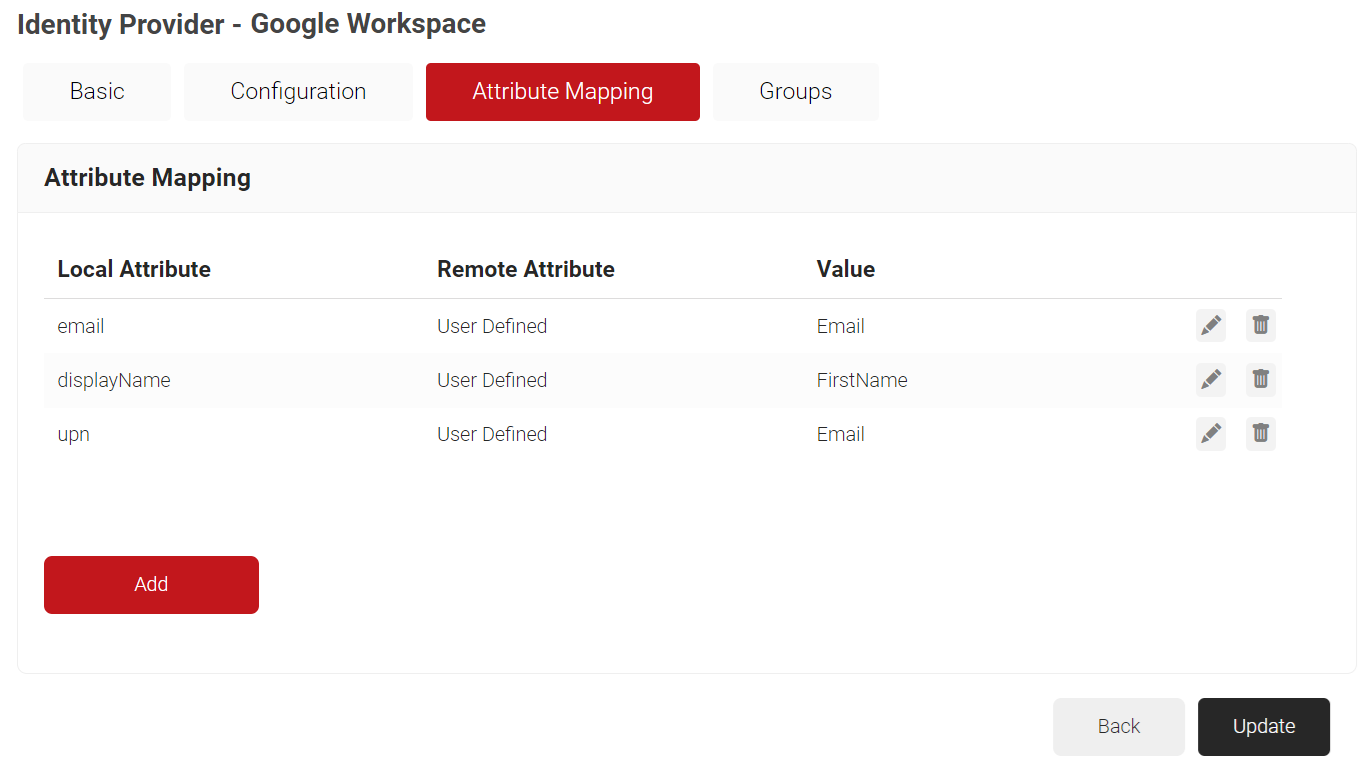
Configuring Attribute Mapping
To add a custom attribute to the IDP, perform the following steps:
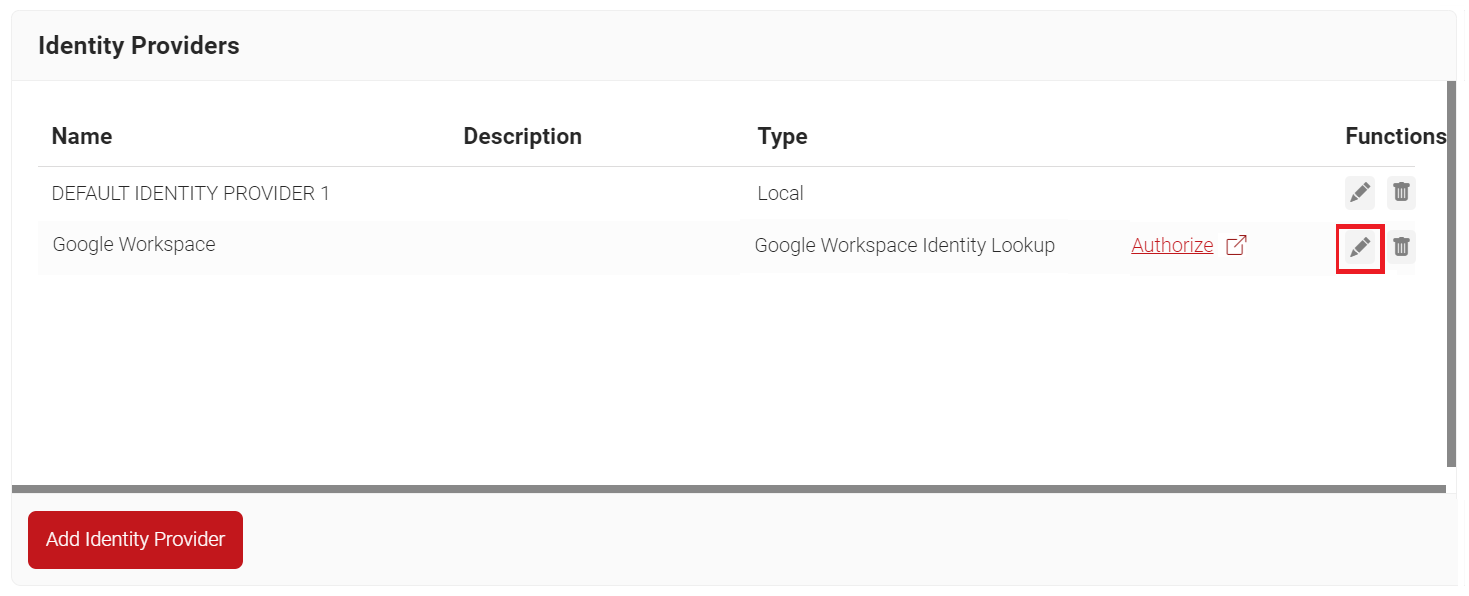
- Navigate to Identity Management > Identity Providers.
- On the Identity Providers page, click the Edit link of the IDP you created earlier (refer the Creating an Identity Lookup Provider section).
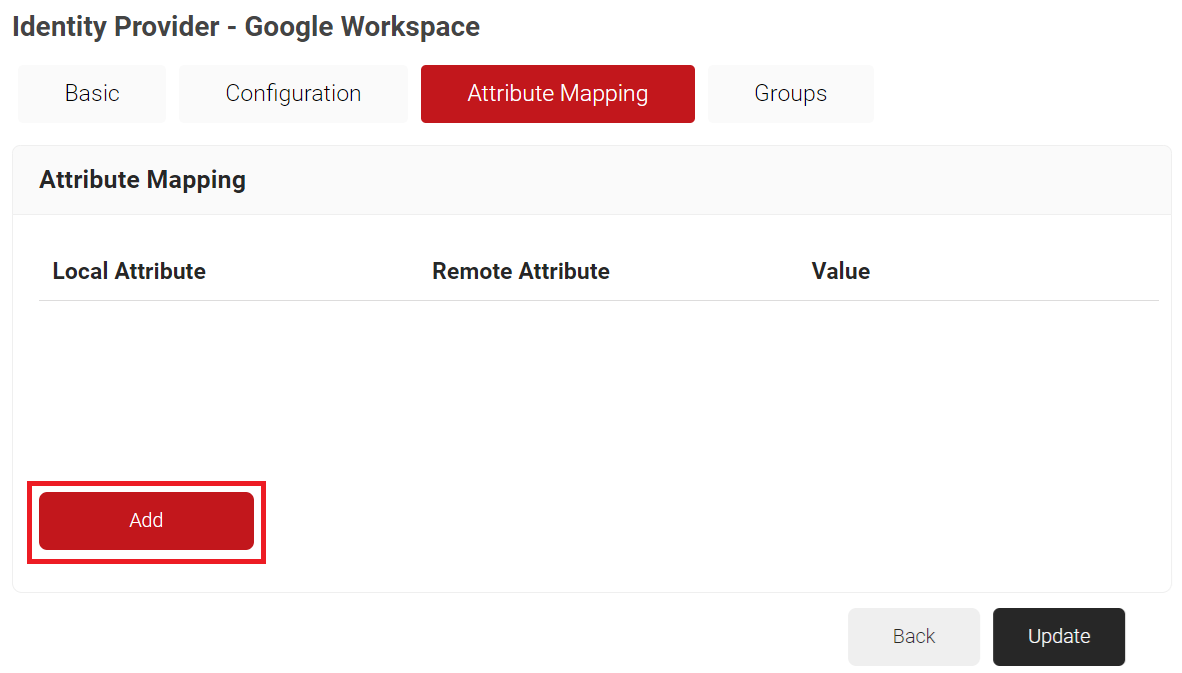
- Select the Attribute Mapping tab and then click Add.
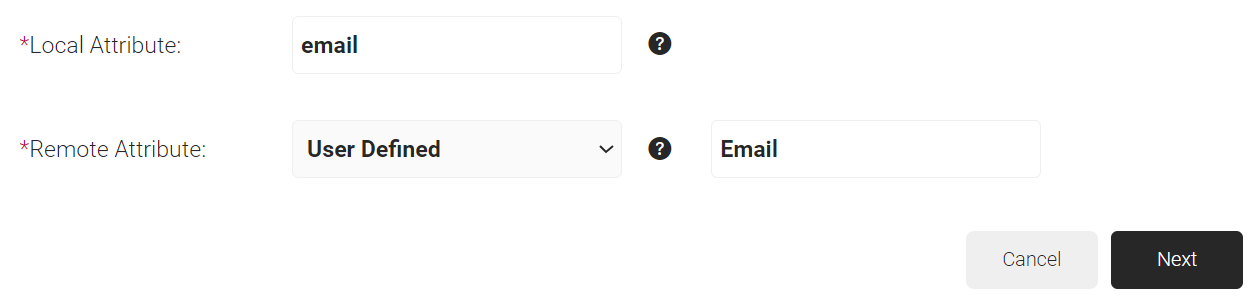
- In the Local Attribute field, enter email as the name of the variable.
- From the Remote Attribute drop-down list, select User Defined and enter Email in the field that appears next to the Remote Attribute field.
- Click Next.
- Click Add.
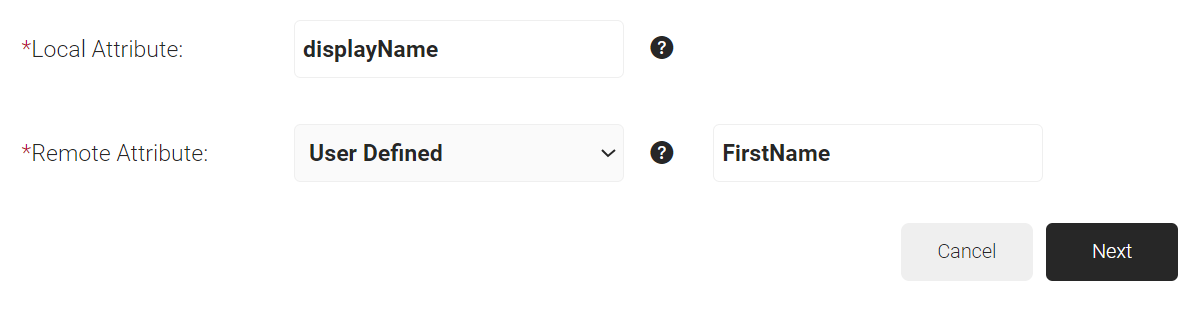
- In the Local Attribute field, enter displayName as the name of the variable.
- From the Remote Attribute drop-down list, select User Defined and enter FirstName in the field that appears next to the Remote Attribute field.
- Click Next.
- Click Add.
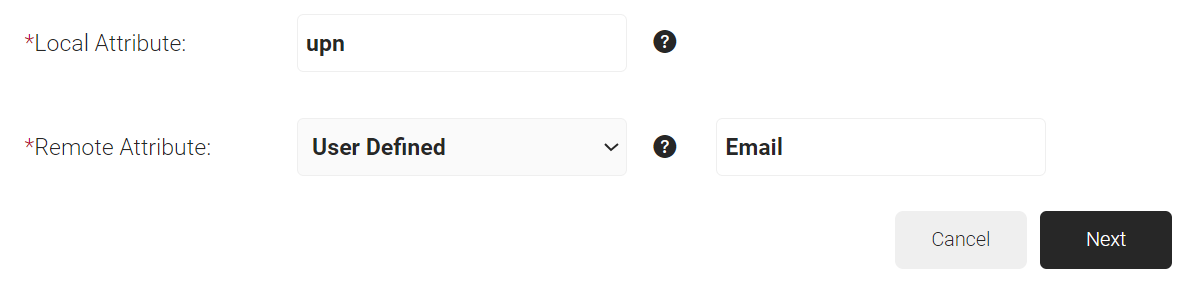
- In the Local Attribute field, enter upn as the name of the variable.
- From the Remote Attribute drop-down list, select User Defined and enter Email in the field that appears next to Remote Attribute field.
- Click Next.
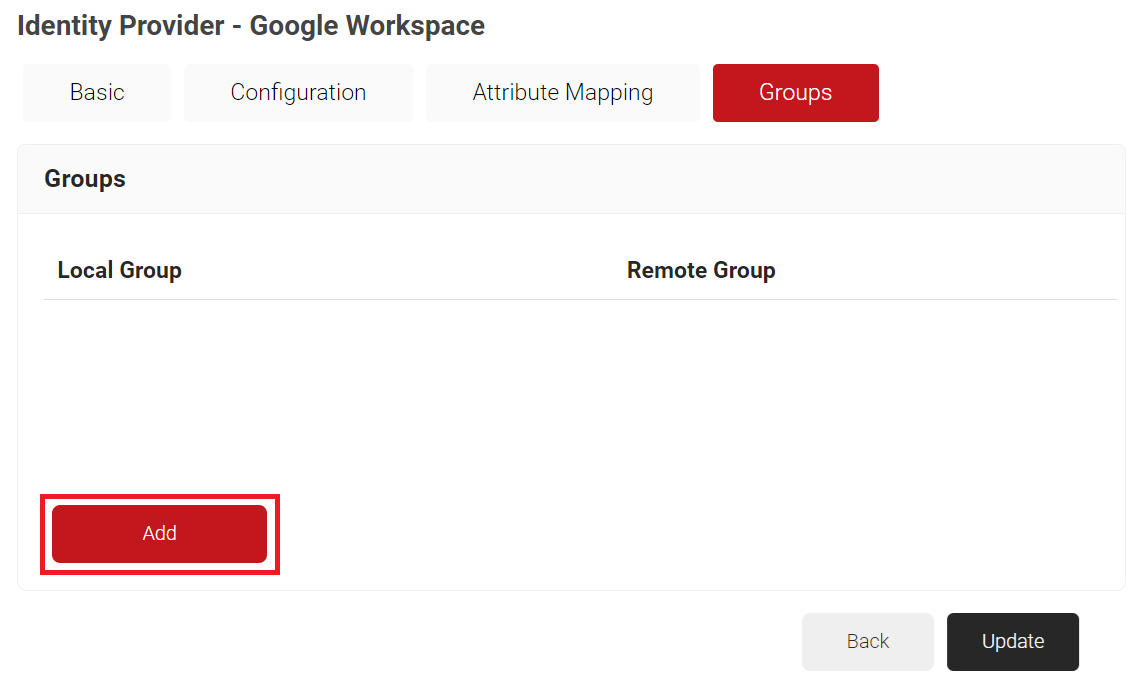
Configuring Groups
Cloud RADIUS can perform a User Group Lookup so we can create network access policies based off of the Groups a user is in. The process is the same as how you added attributes in the previous section.
- Navigate to Identity Management > Identity Providers.
- Click the Edit link on the Identity Lookup Provider created earlier (refer the Creating an Identity Lookup Provider section).
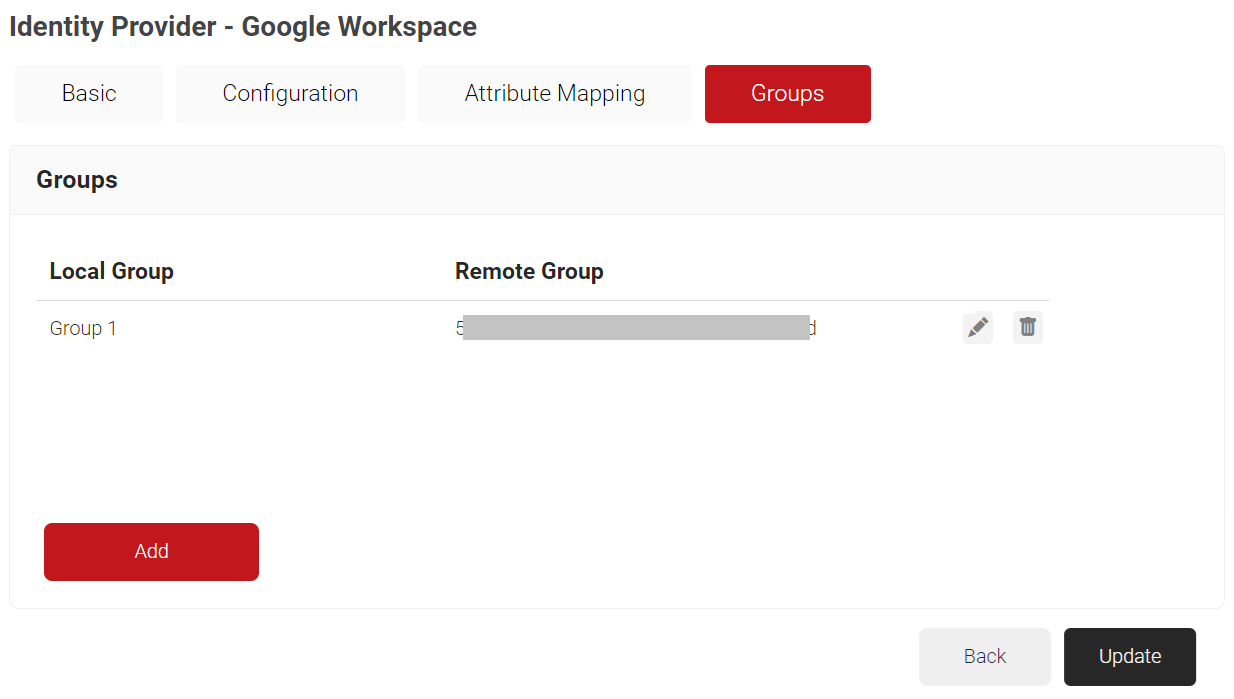
- Select the Groups tab.
- Click Add.
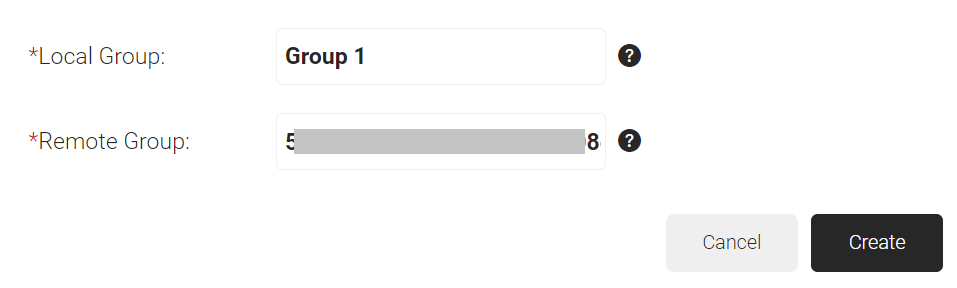
- On the displayed page, in the Local Group field, enter the name of the group.
NOTE: This name shows up later as your ‘Group‘ in the JoinNow MultiOS Management Portal when we configure policies. - In the Remote Group field, enter the name of your group as it is configured in the Google Workspace.
- Click Create.
- Repeat as necessary for any Group you wish to create Network Policies around.
- Click Update.
Configuring Policies
SecureW2 policies allows the organization administrators to segment users and restrict/allow resources based on information stored in their directory entry. Since enforcement occurs at runtime, changes made to a user’s permissions are propagated throughout the system immediately rather than a day or two later, as is typical with most RADIUS servers.
Configuring Account Lookup Policy
Lookup Policies are how we tie the new Identity Lookup Provider to domains. Here you create a condition that ties your domain to the new Identity Lookup Provider you just created in the previous section.
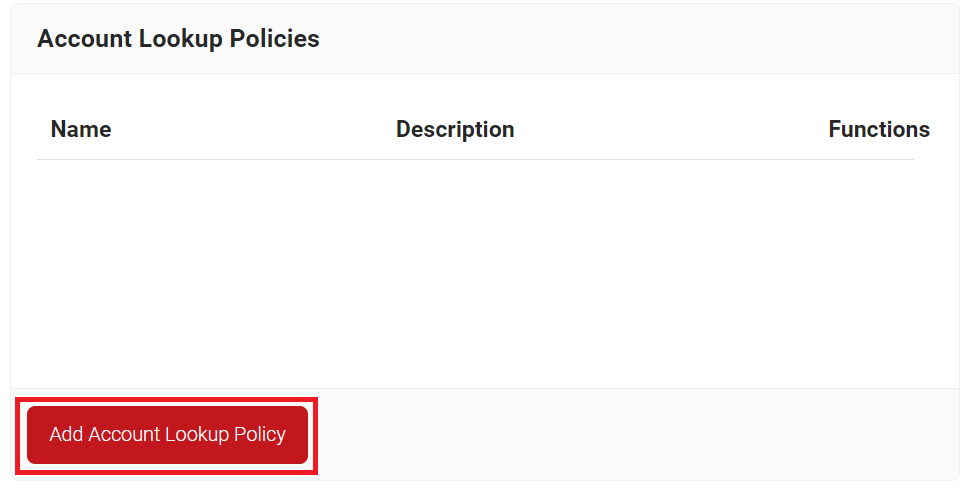
- Navigate to Policy Management > Account Lookup Policies.
- Click Add Account Lookup Policy.
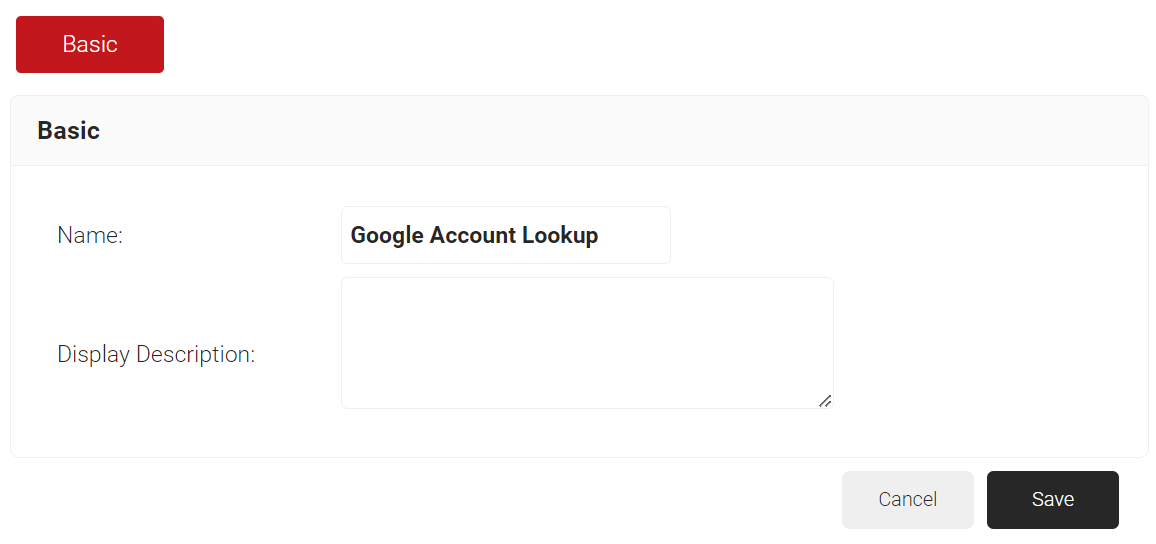
- In the Name field, enter the name of the Account Lookup Policy.
- In the Display Description field, enter the suitable description for the Account Lookup Policy.
- Click Save.
- The page refreshes and displays the Conditions and Settings tabs.
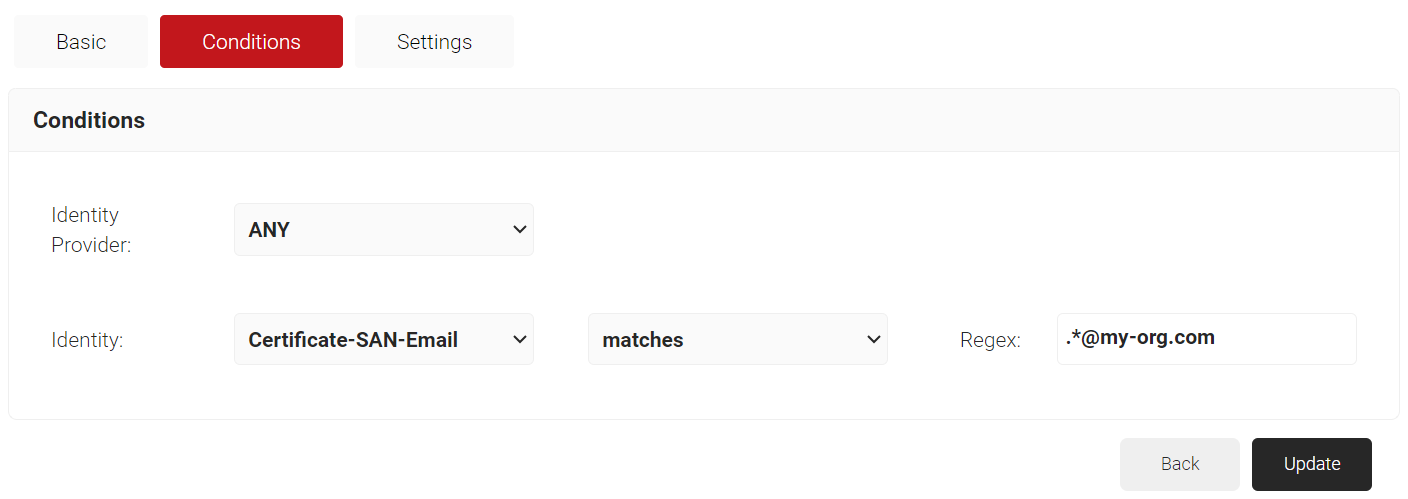
- Select the Conditions tab.
- Under the Conditions section, from the Identity drop-down list, select any one of the following options:
- Username
- Certificate-CommonName
- Certificate-SAN-UPN
- Certificate-SAN-Email
- Configure Regex to match the values of your devices configured in the Identity field.
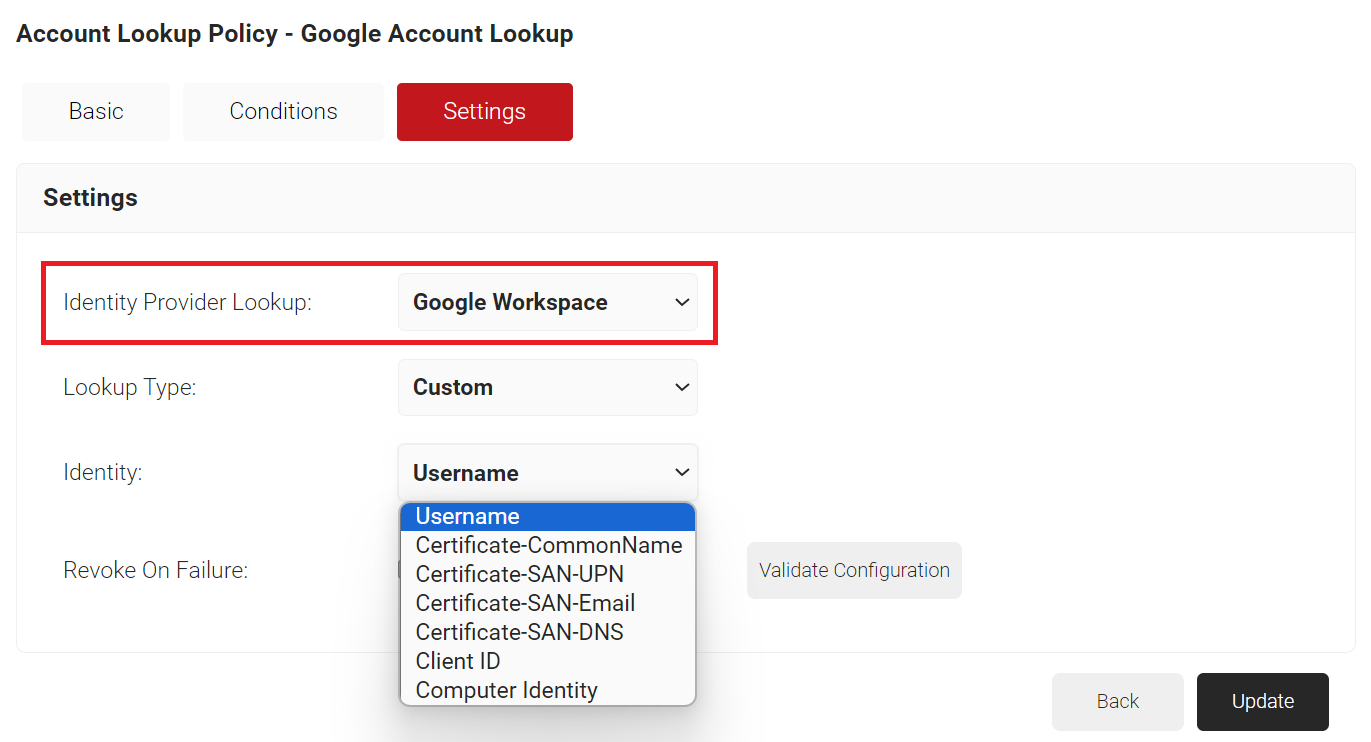
- Under the Settings tab, from the Identity Provider Lookup drop-down list, select the Google Workspace Identity Lookup you created earlier (refer the Creating an Identity Lookup Provider section).
- From the Lookup Type drop-down list, select the lookup type: Auto or Custom.
- From the Identity drop-down list, select an option from the following:
- Username
- Certificate-CommonName
- Certificate-SAN-UPN
- Certificate-SAN-Email
- Certificate-SAN-DNS
- Client ID
- Computer Identity
- Select the Revoke On Failure checkbox.
- Click Update.
Configuring User Role Policy
The following user role policies need to be configured.
User Role Policy for Enrollment
The first User Role Policy you need to create is one for enrollment. This is what MultiOS will use when end users are enrolling themselves for certificates. JoinNow MultiOS will not use the application you previously created in Google, but instead need to use a separate SAML Application in Google.
Refer to one of our SAML Identity Provider configuration guides if you have not set this up already. Once you have your SAML IDP, start here:
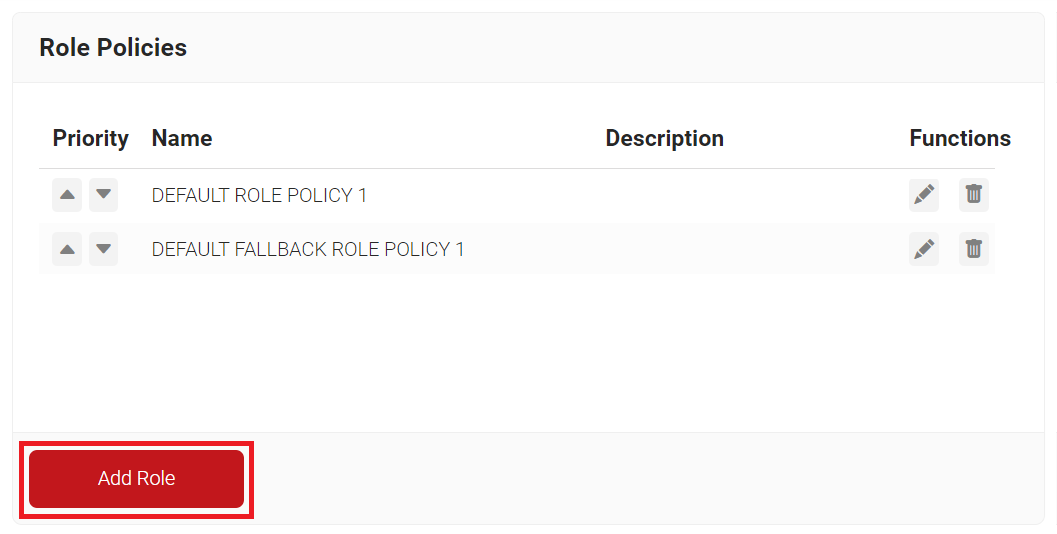
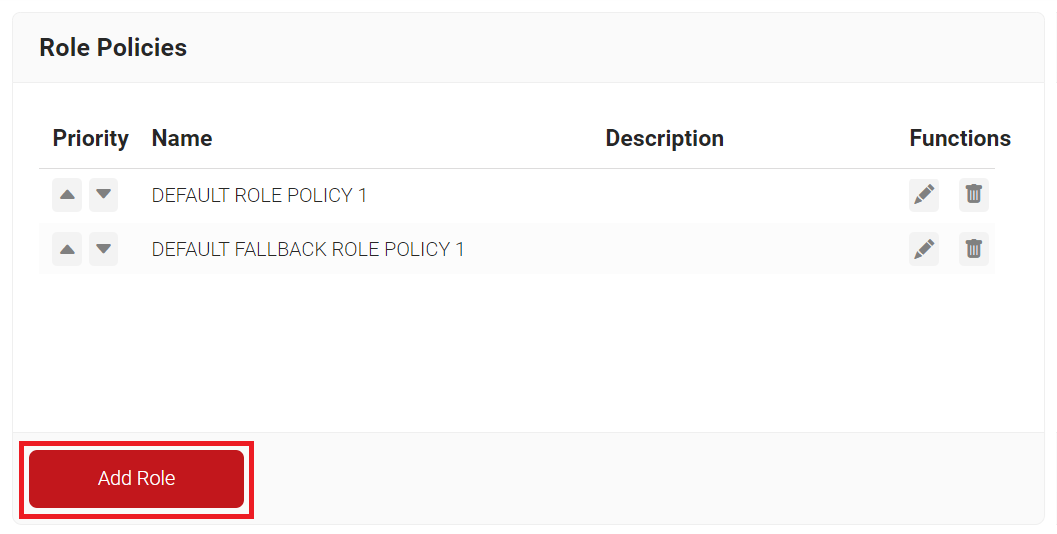
- Navigate to Policy Management > Role Policies.
- On the Role Policies page, click Add Role.
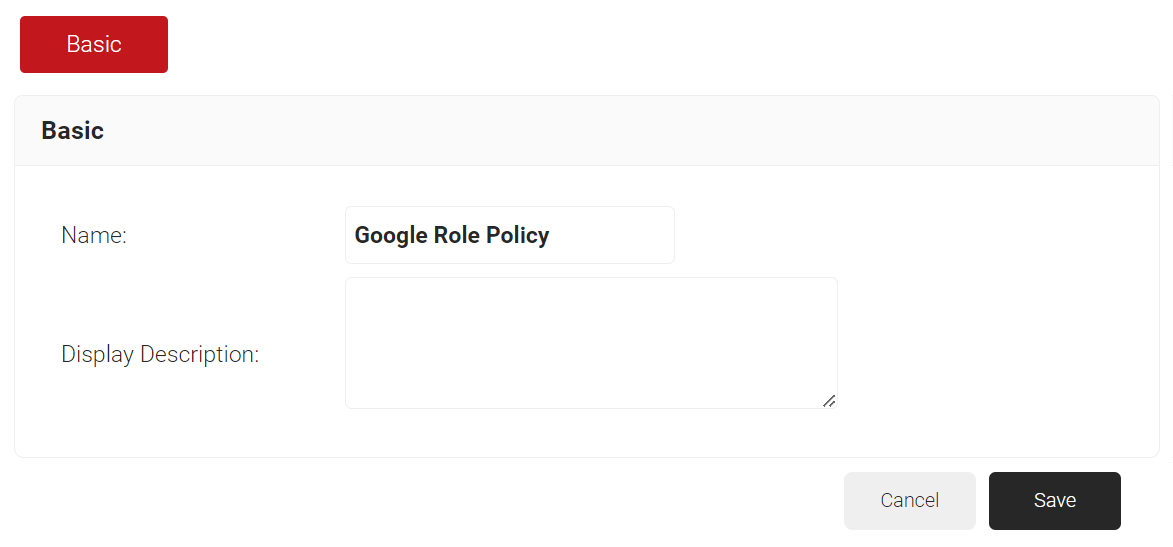
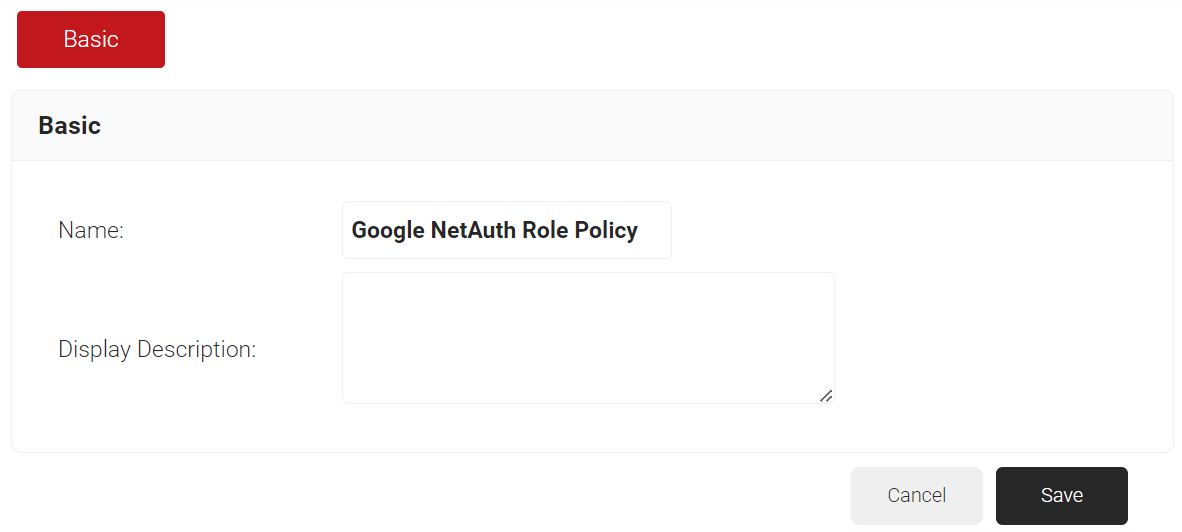
- In the Name field, enter the name of the Role policy.
- In the Display Description field, enter the suitable description for the Role policy.
- Click Save.
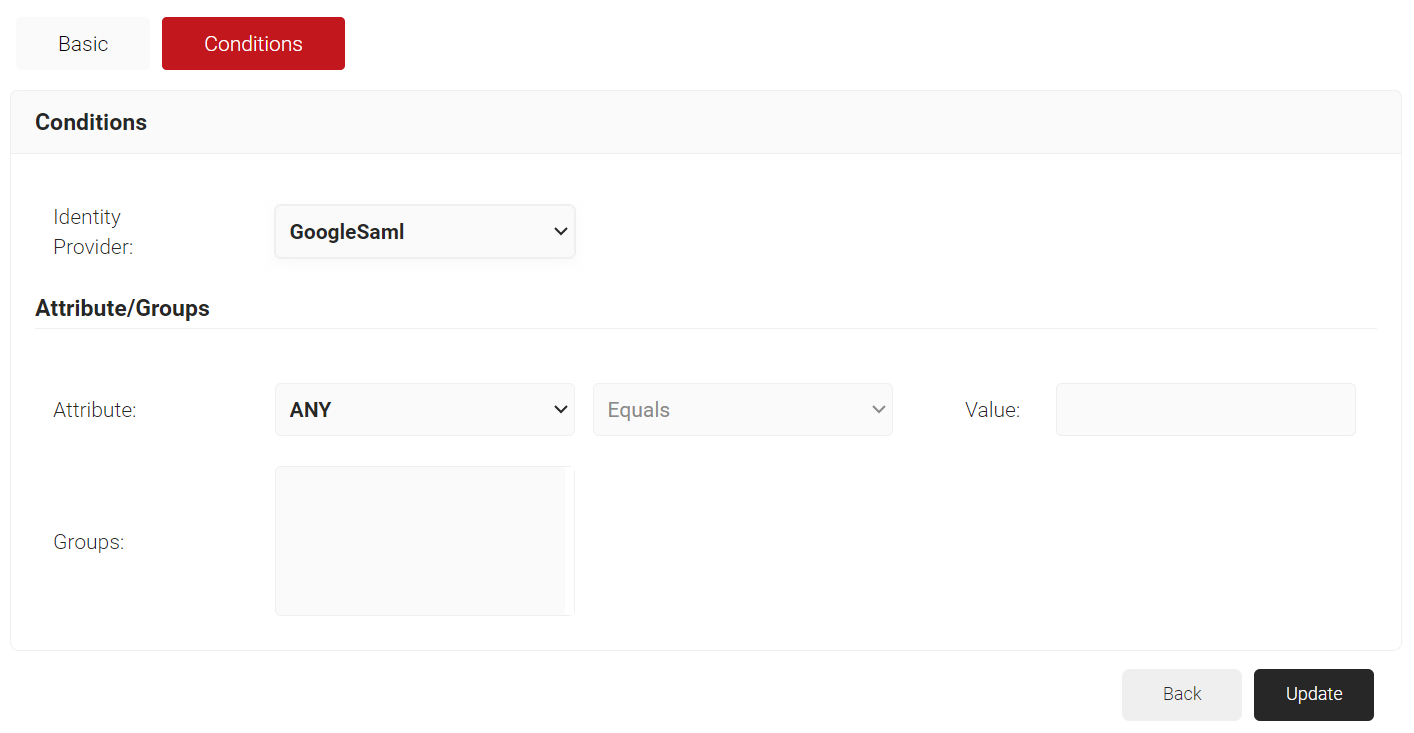
- Select the Conditions tab.
- From the Identity Provider drop-down list, select the Identity Provider you created earlier.
- Click Update.
User Role Policy for Network Authentication
Next, create a User Role Policy for Network Authentication. This policy will be used by Cloud RADIUS’ Dynamic Policy Engine to lookup user status at the moment of authentication. Then Cloud RADIUS can dynamically apply Network policies, which need to be configured next.
- Navigate to Policy Management > Role Policies.
- On the Role Policies page, click Add Role.
- In the Name field, enter the name of the Role policy.
- In the Display Description field, enter the suitable description for the Role policy.
- Click Save.
- Select the Conditions tab.
- From the Identity Provider drop-down list, select the Google Workspace Identity Lookup that you created earlier (refer the Creating an Identity Lookup Provider section).
- Click Update.
Group Role Policy for Network Authentication
Finally, create Role Policies for any Groups that we want to give differentiated network access. We can then leverage Cloud RADIUS’ Dynamic Policy Engine to send unique RADIUS attributes based on the Group users belong to with our Network policies.
- Navigate to Policy Management > Role Policies.
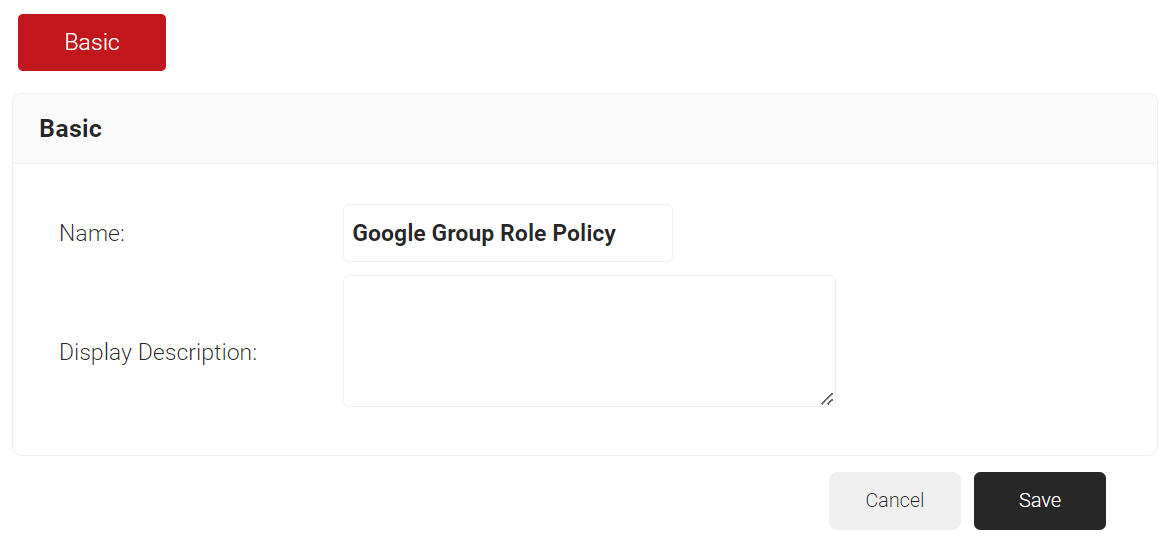
- On the Role Policies page, click Add Role.
- In the Name field, enter the name of the group role policy.
- In the Display Description field, enter the suitable description for the group role policy.
- Click Save.
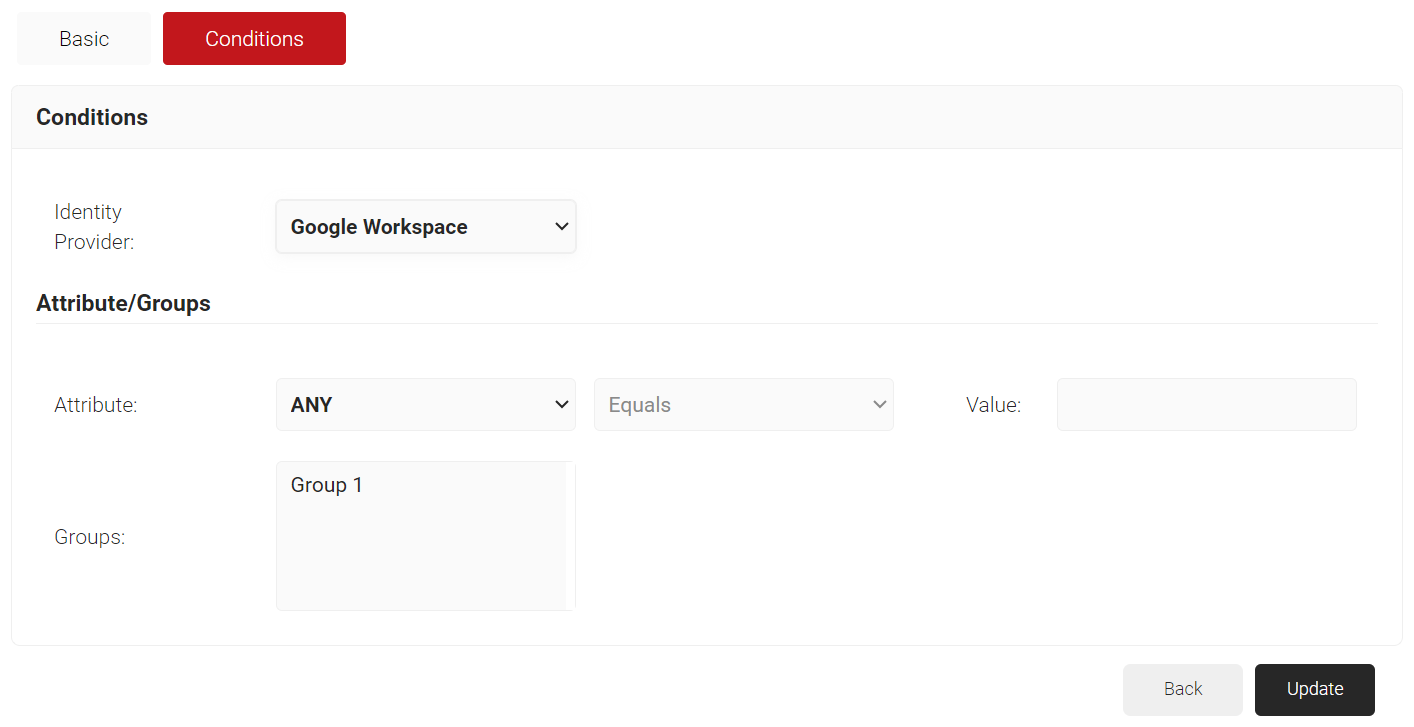
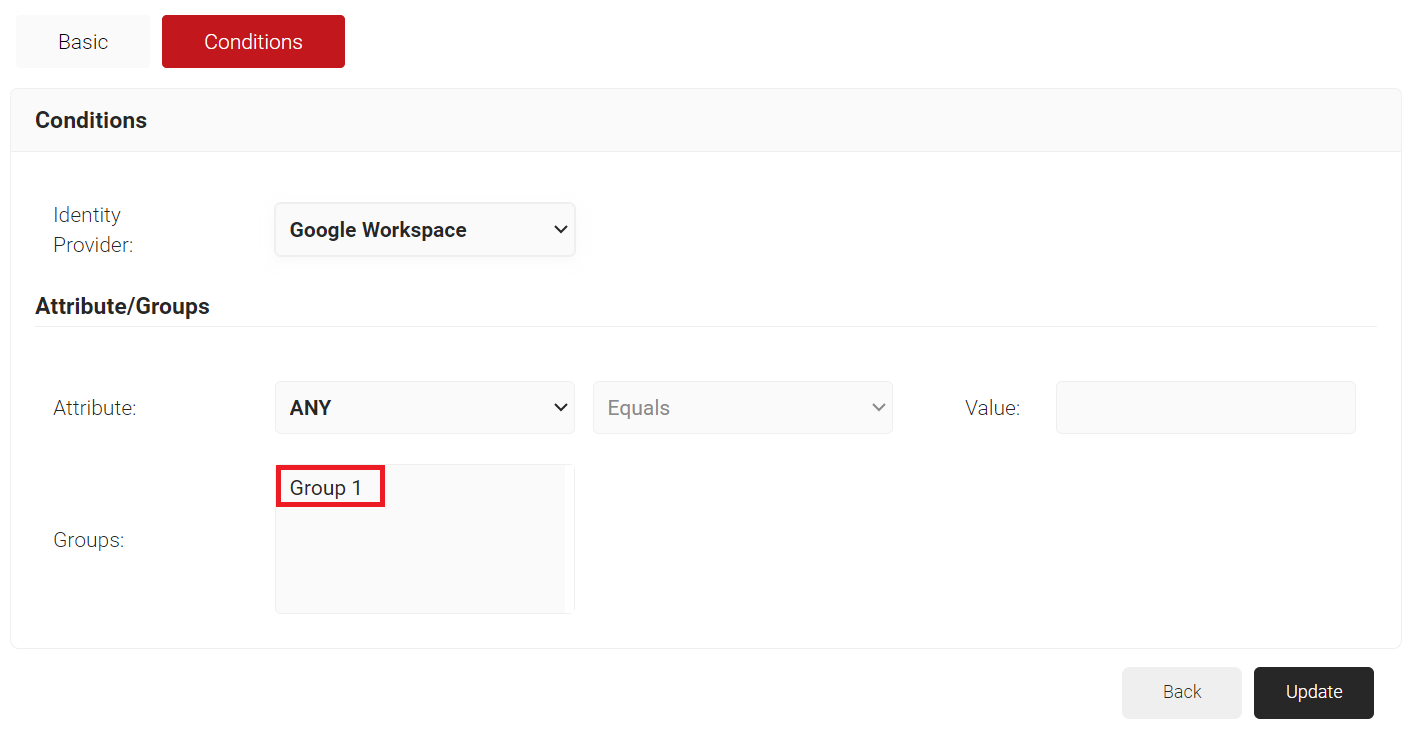
- Select the Conditions tab.
- From the Identity Provider drop-down list, select the Google Workspace Identity Lookup you created in the earlier (refer the Creating an Identity Lookup Provider section).
- Under Attribute/Groups, in the Groups field, select the group you want to apply this Role to. The group names that show up here, are the Local Groups you configured in your Identity Lookup Provider.
- Click Update.
Default Fallback Role Policy
You may notice that there is a “DEFAULT FALLBACK ROLE POLICY” in your User Role policies after you create a Identity Lookup Provider.
The purpose of this policy is that If the Identity Lookup fails, allow the user to still authenticate to the network but assign them a unique role.
This ensures that both users do not experience disconnection if there is a small hiccup in the connection between Google and Cloud RADIUS, but your network can remain secure and you can have those users auto-assigned into a Guest VLAN.
Note: DEFAULT FALLBACK ROLE POLICY is by default assigned the DEFAULT NETWORK POLICY.
Configuring Network Policy
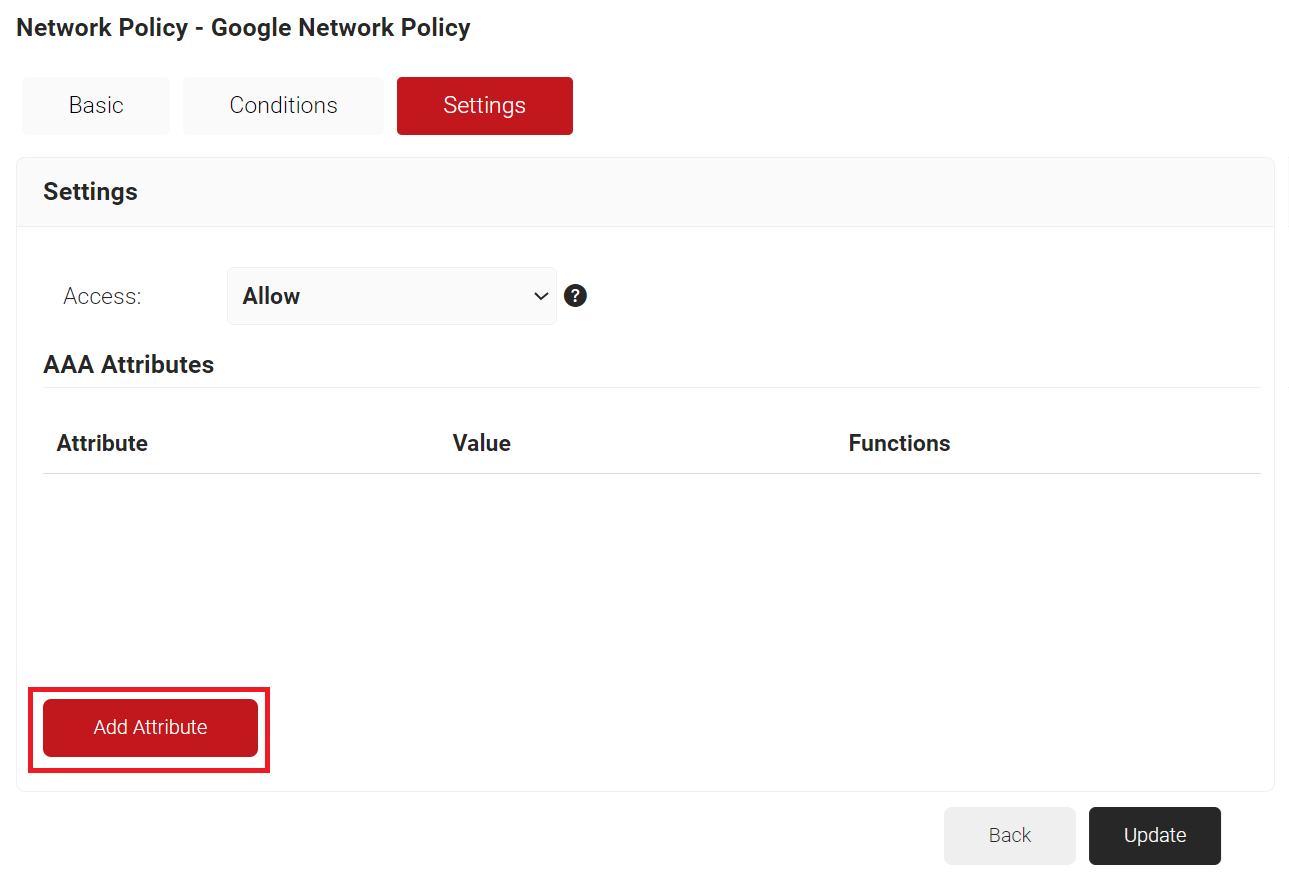
The purpose of a Network Policy is to specify how Cloud RADIUS will authorize access to a particular User Role. A typical Network Policy would say something like: “If User Role = Staff, authorize access and assign them to VLAN 2”. You can configure any RADIUS Attribute to be sent to the wireless controller. If you leave the attribute section blank, it will just send Access Accept. To create and configure the Network Policy, follow the steps below:
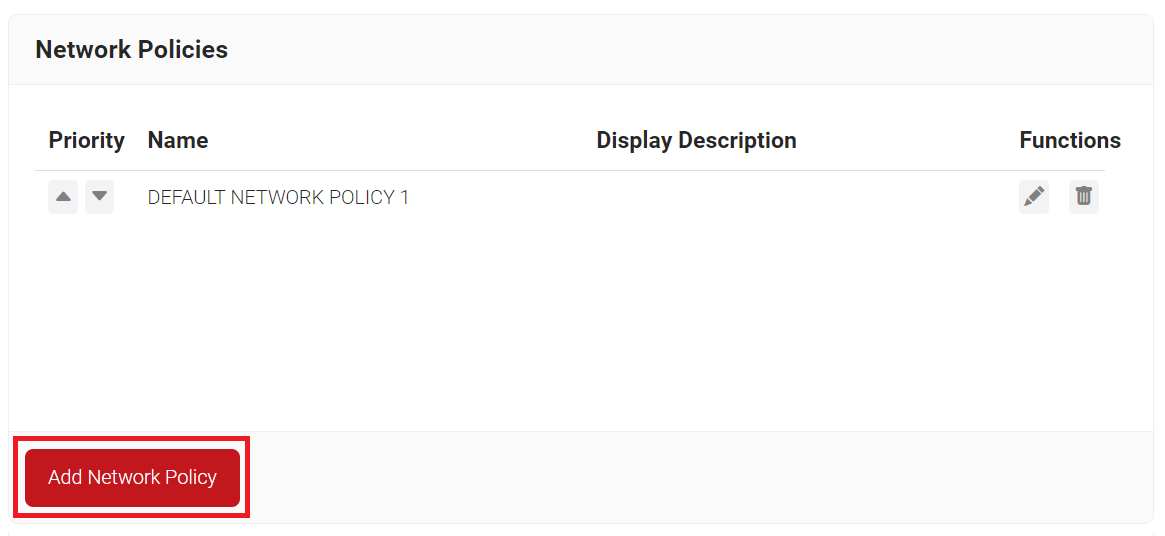
- Navigate to Policy Management > Network Policies.
- On the Network Policies page, click Add Network Policy.
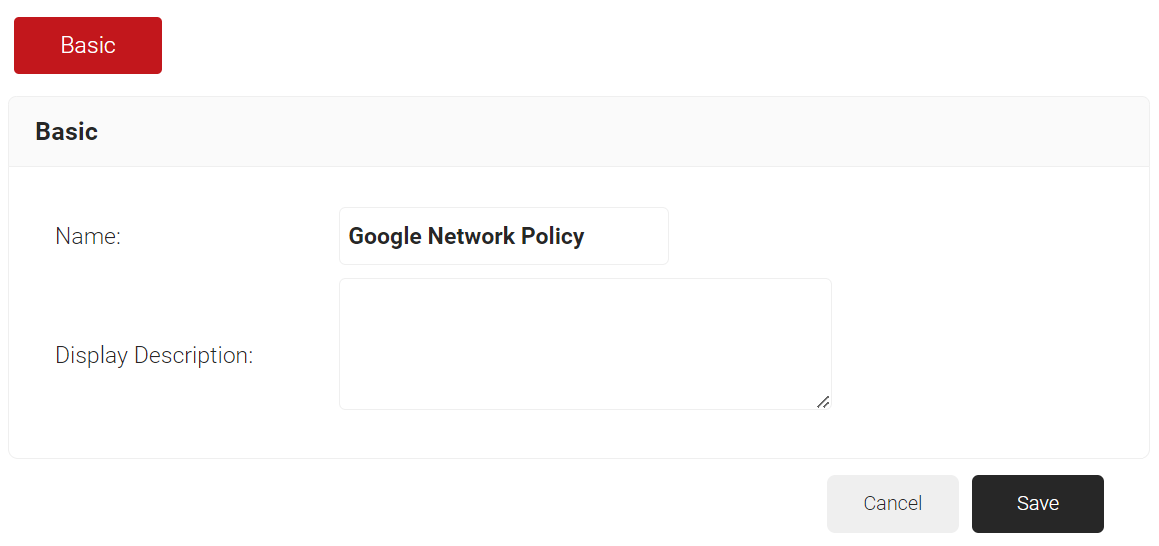
- In the Name field, enter the name of the network policy.
- In the Display Description field, enter the suitable description for the network policy.
- Click Save.
- Select the Conditions tab.
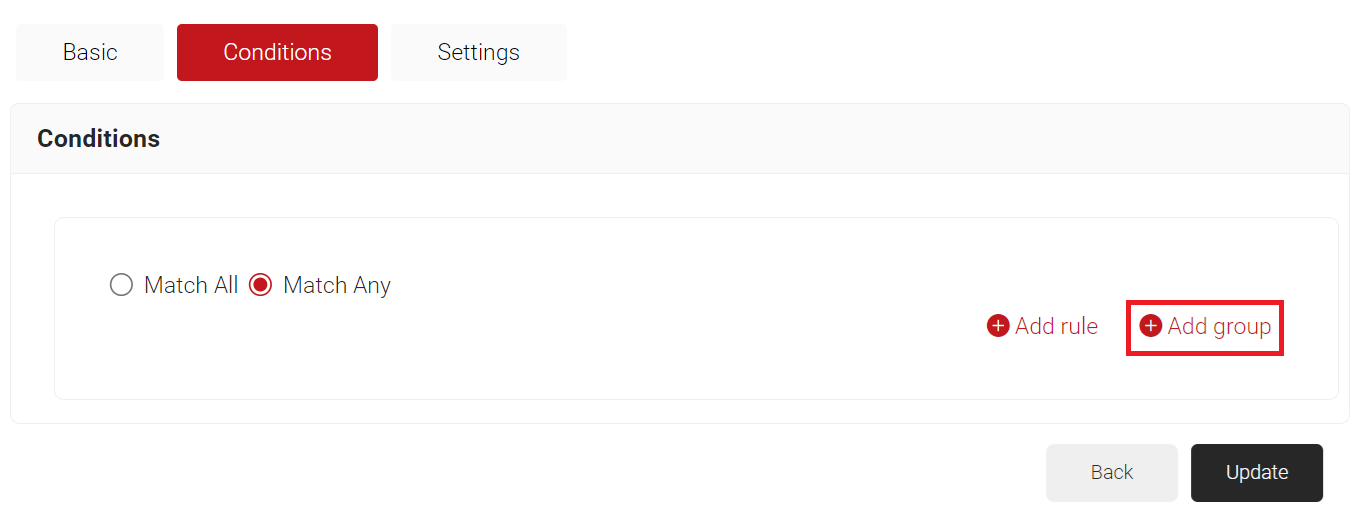
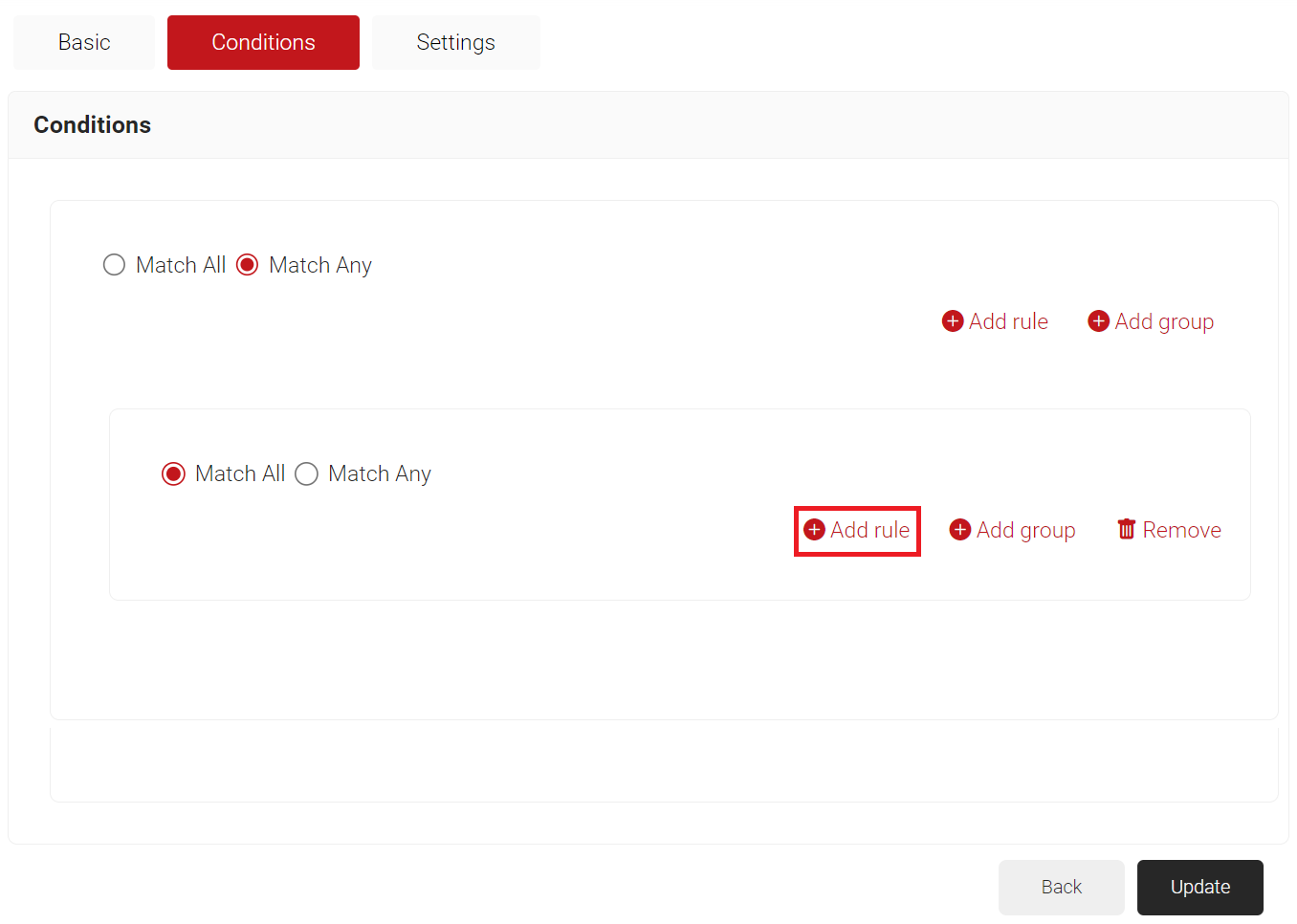
- Click Add group and select the user role you want to assign to this network policy.
NOTE: You can assign a network policy to multiple user roles. - Click Add rule.
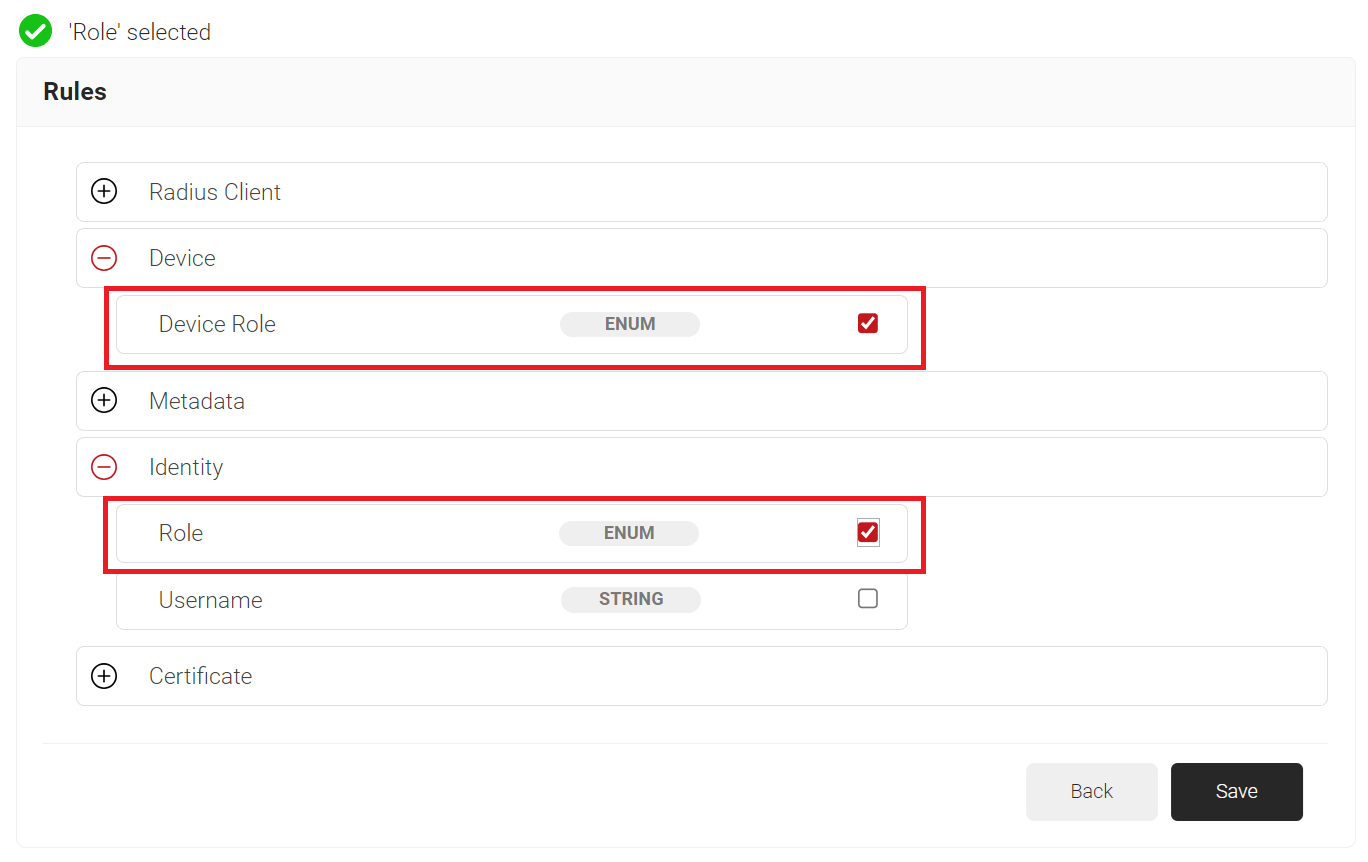
- Expand Identity and select the Role option.
- Expand Device and select the Device Role option.
- Click Save.
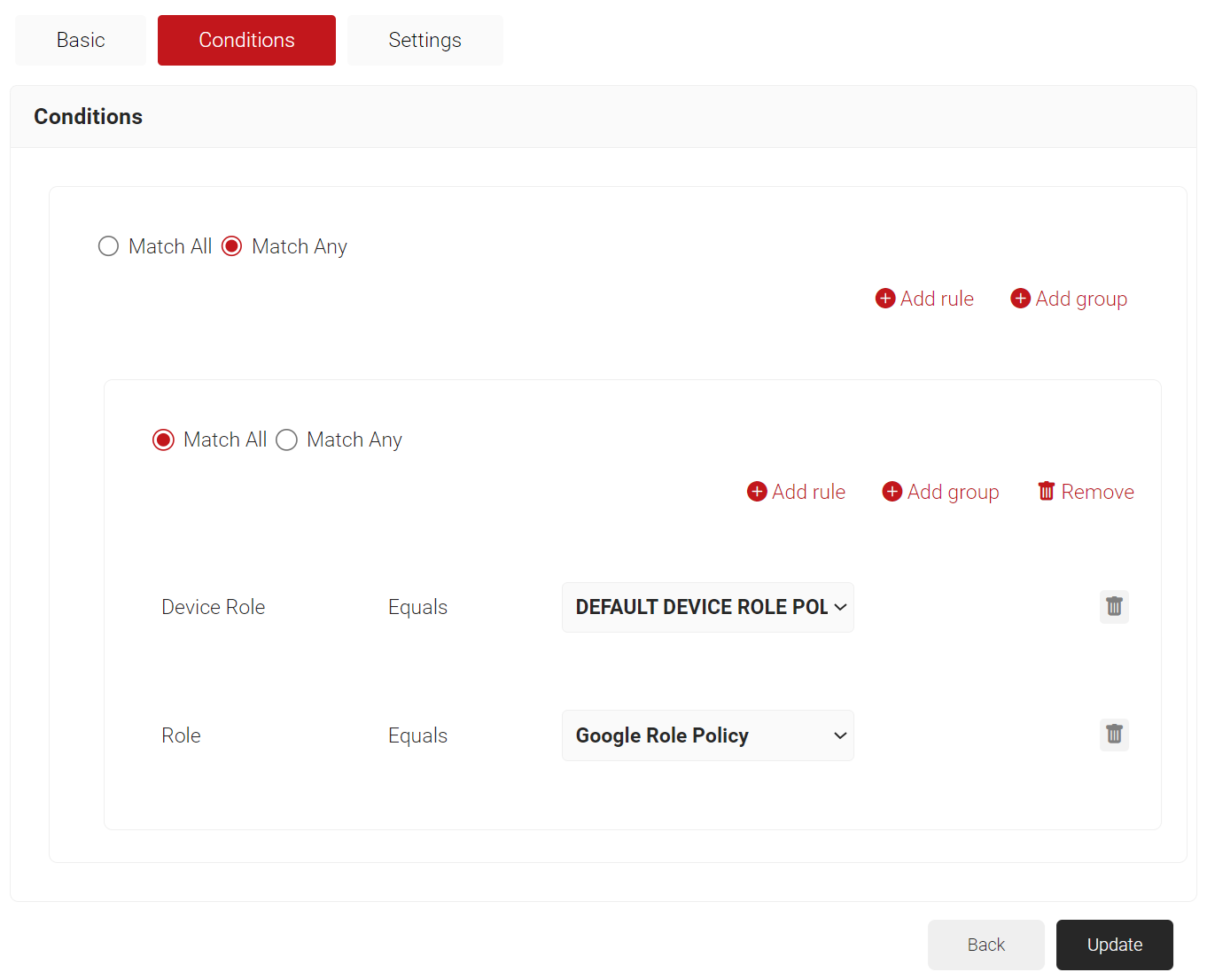
- The Role and Device Role options appears under the Conditions tab.
- From the Role Equals drop-down list, select the role policy you created earlier (refer the User Role Policy for Enrollment section). You can select multiple User Roles to assign to a Network Policy.
- Select the Settings tab.
- Click Add Attribute.
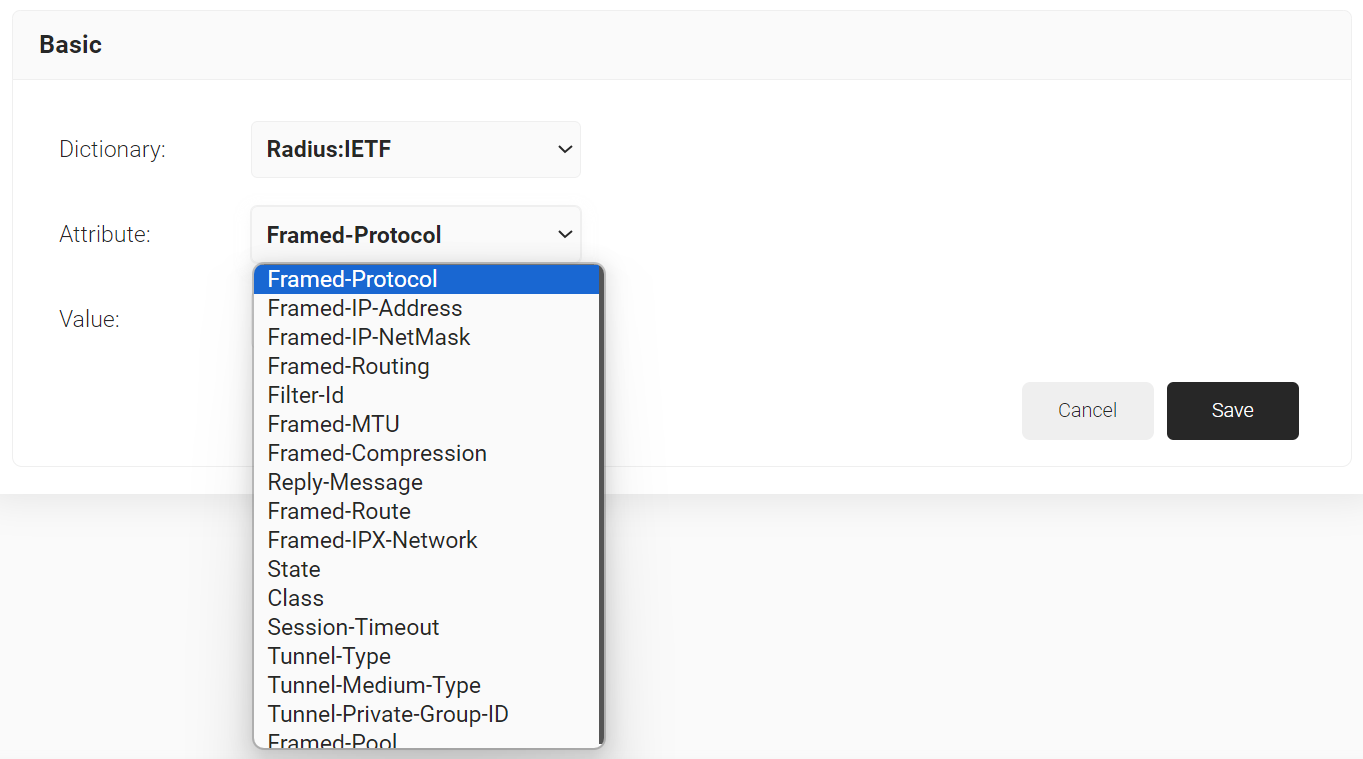
- From the Dictionary drop-down list, select an option: Radius:IETF or Custom.
- From the Attribute drop-down list, select an option.
- In the Value field, enter the appropriate value for the attribute.
- Click Save.
- Click Update.
NOTE: Repeat the process for all the attributes you want to send to the User Role.
Enhancing Network Security with SecureW2 and Google Workspace
Integrating SecureW2 with Google Workspace for network authentication ensures administrators and users a robust, secure, and smooth experience. Following the procedures here will allow you to utilize SecureW2’s Cloud RADIUS solution, assuring safe fully, certificate-based 802.1x authentication and easing network management. The combination of SecureW2 with Google Workspace improves security while simplifying the login process, reducing administrative load, and increasing user experience.
SecureW2’s revolutionary solutions provide unrivaled security and ease of use. With capabilities such as automated certificate enrollment, full identity search, and extensive policy administration, SecureW2 is the solution for organizations wishing to protect their networks using Google Workspace. Our cloud-based RADIUS server offers high availability and minimum maintenance, letting you focus on what is most important—your company.
Contact us now to find out how we can assist your organization in achieving seamless and secure authentication.
RADIUS Authentication for Google Workspace FAQs
Our platform enables administrators to take attributes from Google Workspace and tie them to users through the use of digital certificates. These certificates can then be used in tandem with Cloud RADIUS to passwordlessly authenticate to a range of resources, including Wi-Fi and wired networks.
The authentication process is straightforward. Once the user is enrolled for a certificate, they’re able to send the certificate to Cloud RADIUS when they connect to your secure Wi-Fi network. Cloud RADIUS will verify that the certificate isn’t expired, then perform Identity Lookup in real-time to confirm that the user is authorized in Google Workspace. This method of authenticating users isn’t just more secure; it’s more user-friendly. Since they no longer need to enter in passwords whenever they need to re-authenticate or endure annoying disconnects when their password is reset, they can enjoy uninterrupted access.
Using Google credentials for Wi-Fi and VPN authentication introduces substantial security threats and administration issues. Direct credential use raises the danger of phishing attacks, as leaked passwords can provide unauthorized access to critical network resources. Furthermore, password-based authentication lacks the strength of contemporary security methods, making the network vulnerable to brute-force assaults.
Furthermore, maintaining and safeguarding passwords can be complicated, leading to inadequate password practices among users. Instead, combining Google Workspace with a solution such as SecureW2's Cloud RADIUS and Digital Certificates improves security by enabling passwordless authentication. This strategy reduces the chance of credential theft while simultaneously streamlining the authentication process, resulting in a safe and quick network access experience.
By using TLS (Transport Layer Security) to encrypt RADIUS communication and guarantee that authentication data is transferred securely across the network, RadSec improves the security of RADIUS authentication with Google Workspace. In contrast to standard RADIUS's plain text transmission, RadSec's end-to-end encryption shields sensitive credentials against eavesdropping and manipulation.
This secure connection is essential when connecting with Google Workspace since it guarantees the protection of sensitive data, including user credentials, throughout the authentication process. RadSec now allows mutual authentication to strengthen security further, enabling the client and server to authenticate. Businesses may securely authenticate customers to VPN and Wi-Fi services while protecting the integrity and privacy of their Google Workspace login credentials by implementing RadSec.
Building a custom RADIUS server for Google Workspace may be difficult and resource-consuming. An in-depth understanding of network protocols, security procedures, and continual maintenance to guarantee compliance with Google Workspace's authentication protocols is necessary for developing a safe and dependable RADIUS server. It also requires frequent upgrades to fix security flaws and adjust to evolving requirements.
Strong encryption and security methods, like RadSec, are also necessary for Google Workspace integration to safeguard user credentials. A lack of these cutting-edge capabilities in an Indigenous solution might pose security problems. Furthermore, development, testing, and maintenance can take time and money.
A professionally managed solution like SecureW2 guarantees that professionals handle these difficulties and offers a secure, dependable, and compliant authentication service by leaving the complexity of creation and maintenance to the professionals.
The Cloud RADIUS solution from SecureW2 is the best option for Google Workspace authentication because of its strong security, smooth integration, and user-friendliness. Supporting cutting-edge encryption protocols like EAP-TLS offers a safe authentication technique and guarantees the protection of user credentials. Because SecureW2's RADIUS is cloud-based, there is no need for on-premises equipment, which lowers maintenance and operating expenses.
Furthermore, SecureW2 simplifies the deployment process by providing a simple connection with Google Workspace. The solution facilitates features that improve security and lower the possibility of credential theft, such as certificate-based authentication. Organizations using SecureW2 may use round-the-clock monitoring and assistance, guaranteeing consistent, dependable functioning. SecureW2's Cloud RADIUS offers an extensive, safe, and reasonably priced authentication solution designed specifically for Google Workspace.