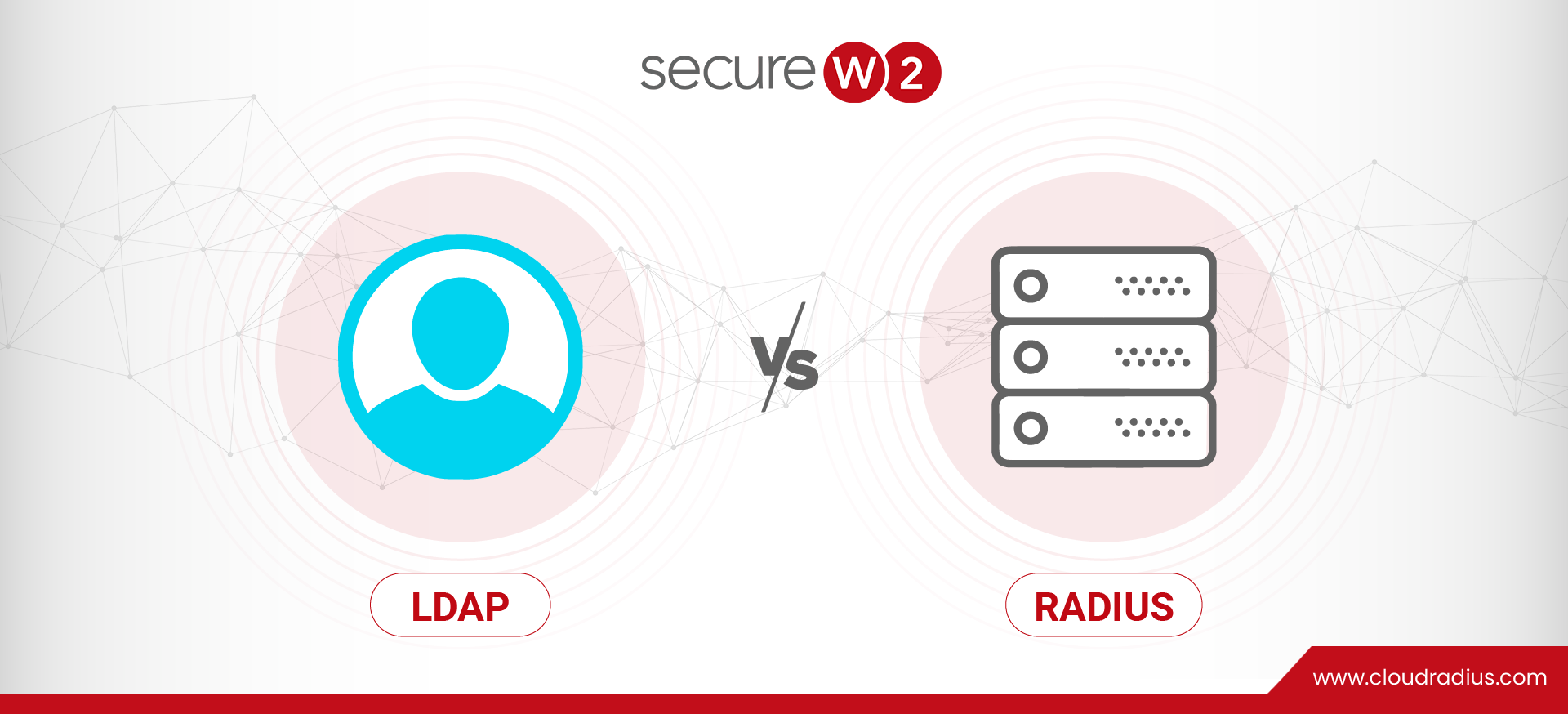
LDAP Vs. RADIUS
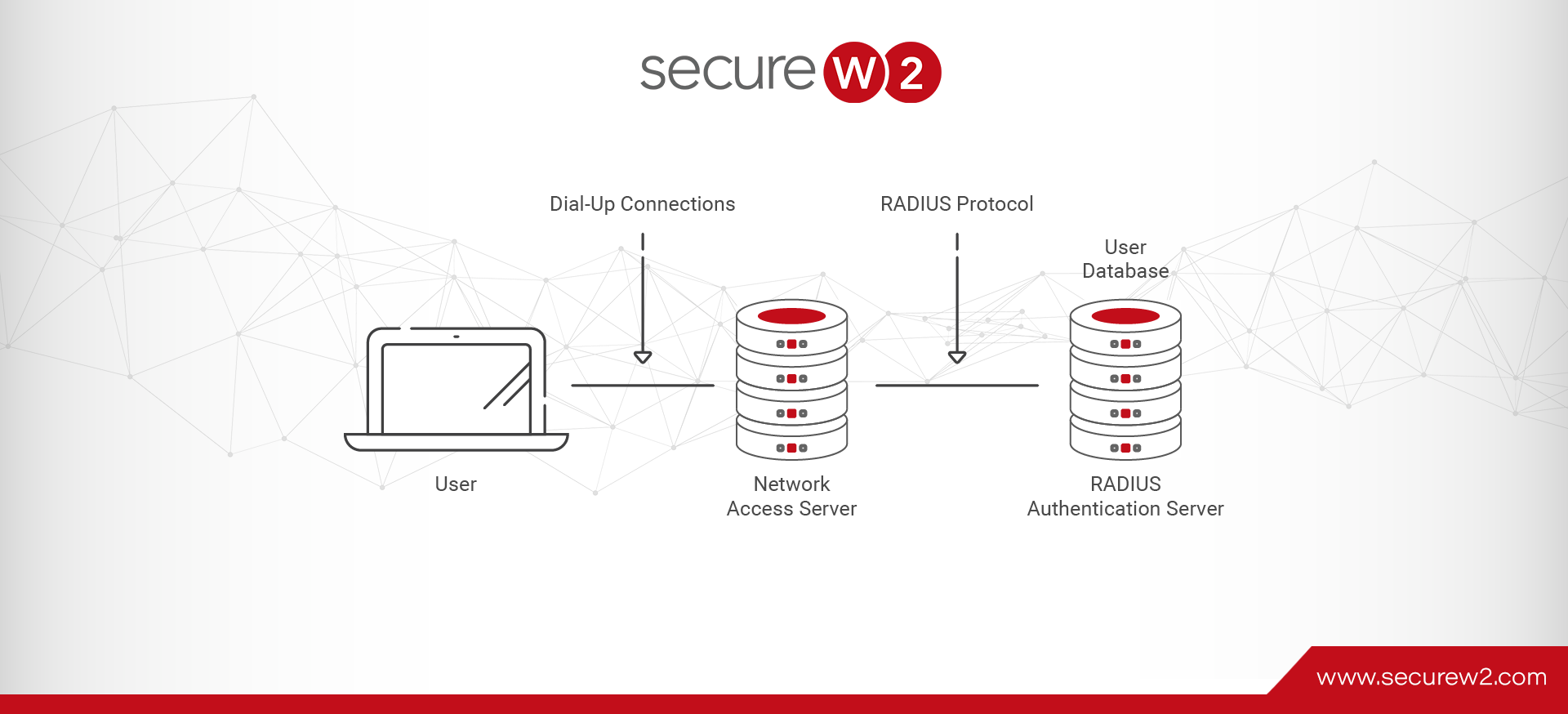
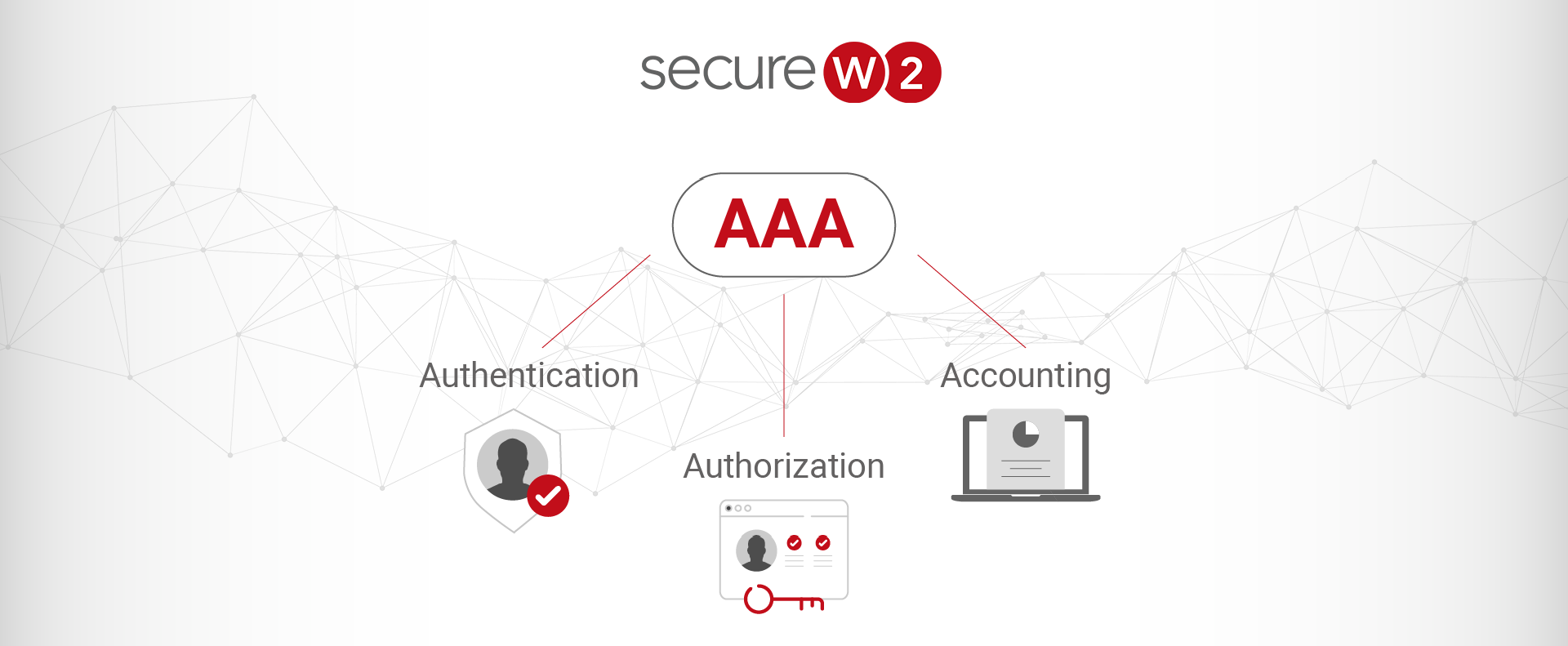
Two widely used protocols, LDAP (Lightweight Directory Access Protocol) and RADIUS (Remote Authentication Dial-In User Service) are essential to network authentication and access management. These protocols are the crucial building pieces that allow for effective and safe user management in a networked setting. LDAP is especially good at handling user IDs and associated attributes since […]
Read Story