Exploring the Benefits of Cloud 802.1X Security for Modern Enterprises
In modern times, cloud infrastructure is expeditiously superseding on-premise infrastructure as the favoured alternative for numerous enterprises. The myriad benefits of cloud computing are especially evident in the realm of cybersecurity. Due to the escalating need for safeguarded wireless networks, 802.1X authentication has surfaced as the predominant standard for guaranteeing network security.
The protocol was formerly established via on-premises infrastructure. Nevertheless, cloud-based solutions such as Azure AD and SecureW2’s Cloud RADIUS are increasingly prevalent. In this article, we shall delve into the advantages of leveraging cloud infrastructure for 802.1X authentication, while also highlighting the disparities between on-premise and cloud-based environments.
Understanding the Basics of 802.1X and WPA2 Enterprise
The 802.1X protocol is a highly effective network authentication mechanism that is widely employed to guarantee secure network access. IEEE has developed a port-based network access control protocol that is widely accepted as a standard in the cybersecurity industry. The protocol operates through the process of device authentication for network-connected endpoints, including laptops and smartphones, to ensure that solely authorised users are granted access to the network.
The implementation of 802.1X allows for individualized user authentication through the utilization of either password or digital certificate credentials, thereby enabling network access. Digital certificates serve as virtual identification badges that enable secure authentication and access. Certificates are issued by Certificate Authorities (CAs) to clients and comprise of crucial information that is utilized for user or device identification purposes.
WPA2-Enterprise is a security protocol that utilises 802.1X authentication for enhanced security measures. In contrast to the widely used WPA2-PSK protocol, the WPA protocol provides a greater array of security measures for Wi-Fi protection. It is imperative that every user provides a unique username and password for network access when utilising WPA2-Enterprise, which facilitates personalised user authentication. In contrast to the utilisation of WPA2-PSK, where all users are mandated to share a common password.
The utilization of 802.1X and WPA2-Enterprise is interdependent. The nomenclature is frequently utilized interchangeably, consequently. Establishing a WPA2-Enterprise network with unique user credentials fortifies the network’s security posture by mitigating the risk of unauthorized access from malicious actors. The absence of a shared password eliminates the possibility of password theft, thereby enhancing the network’s resilience against cyber threats.
The Components of 802.1X and WPA2 Enterprise
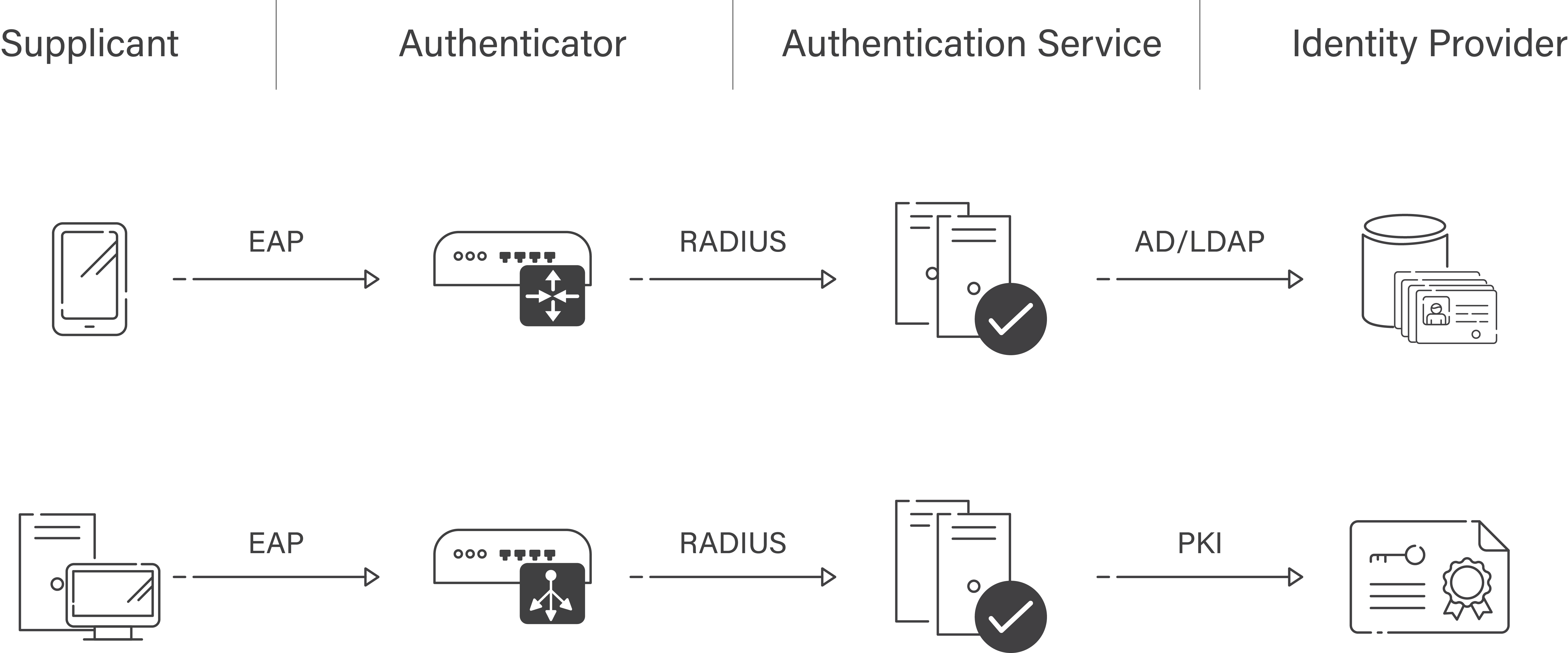
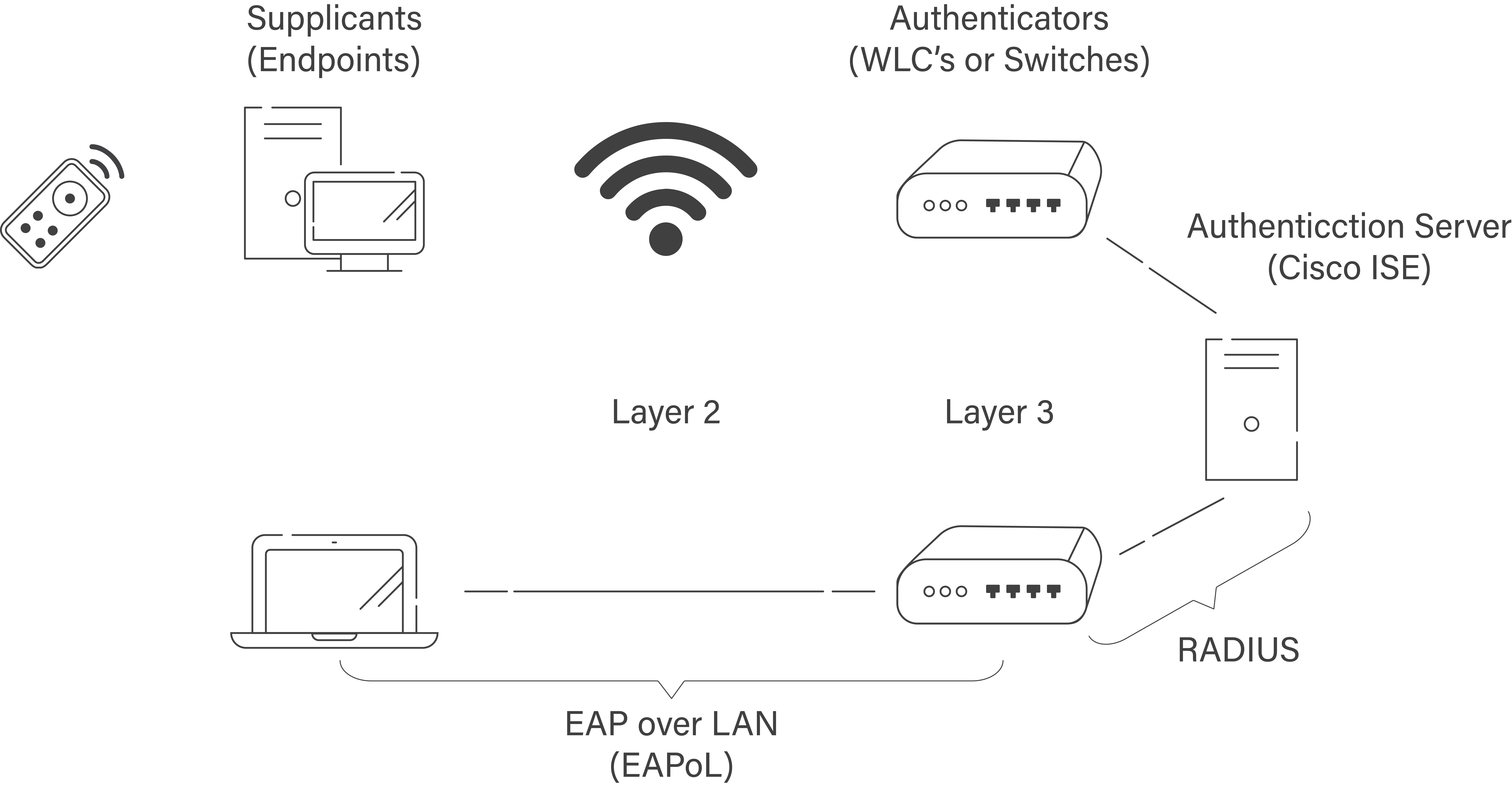
Three basic components make up the 802.1X authentication framework: the supplicant, the authenticator, and the authentication server. In the realm of network security, the term “supplicant” refers to the client device, like a cell phone or computer, that is endeavoring to establish a network connection. The wireless access point, commonly referred to as the network access device, functions as the authenticator within the system. The established entity responsible for handling authentication is the authentication server, which may take the form of a RADIUS server.
The tripartite components employed in 802.1X authentication are similarly leveraged in WPA2 Enterprise. Utilizing distinct credentials for each user provides an extra level of protection. It is imperative to authenticate user credentials against the authentication server prior to granting network access.
Why Is 802.1X the Best Solution for Enterprise Network Security?
In the realm of enterprise network security, 802.1X is widely acknowledged as the most robust and impregnable option available. The robust access control and authentication mechanisms in place ensure that network access is restricted to authorised personnel and devices, thereby enhancing security. In addition, the implementation of 802.1X provides enterprises with the flexibility to safeguard their network through the utilisation of diverse authentication techniques, including but not limited to username/password, digital certificates, and smart cards.
In contrast to other network security protocols, WPA2-PSK networks employ a uniform password for all users, thereby rendering them susceptible to password breaches or unauthorized dissemination. The aforementioned action could potentially lead to illicit network entry and plausible data security violations. It is imperative to note that WPA2-Enterprise surpasses WPA2-PSK in terms of security as it provides personalized user authentication and utilizes 802.1X for authentication.
On-Premise 802.1X Security
Formerly, the 802.1X security protocol was implemented to verify user identities through local infrastructure, such as Active Directory and NPS (RADIUS Server). The traditional approach does possess certain significant constraints, however.
A notable drawback associated with on-premise infrastructure pertains to the substantial expenses incurred during the setup and maintenance phases. In order to effectively oversee the infrastructure, it is imperative for businesses to allocate resources towards requisite technology, software, and personnel. Scaling the infrastructure to accommodate the organization’s growing demands could pose significant challenges and incur substantial costs.
The scalability of on-premise infrastructure is comparatively inferior to that of cloud-based alternatives. The process of incorporating additional locations or users requires meticulous manual configuration, which can be a laborious and vulnerable task. Additionally, it could potentially pose challenges for an organization to expeditiously adapt to novel circumstances and requisites.
In essence, while on-premise infrastructure may offer a degree of security, it presents a costly and challenging-to-expand alternative, rendering it less appropriate for modern enterprise networks.
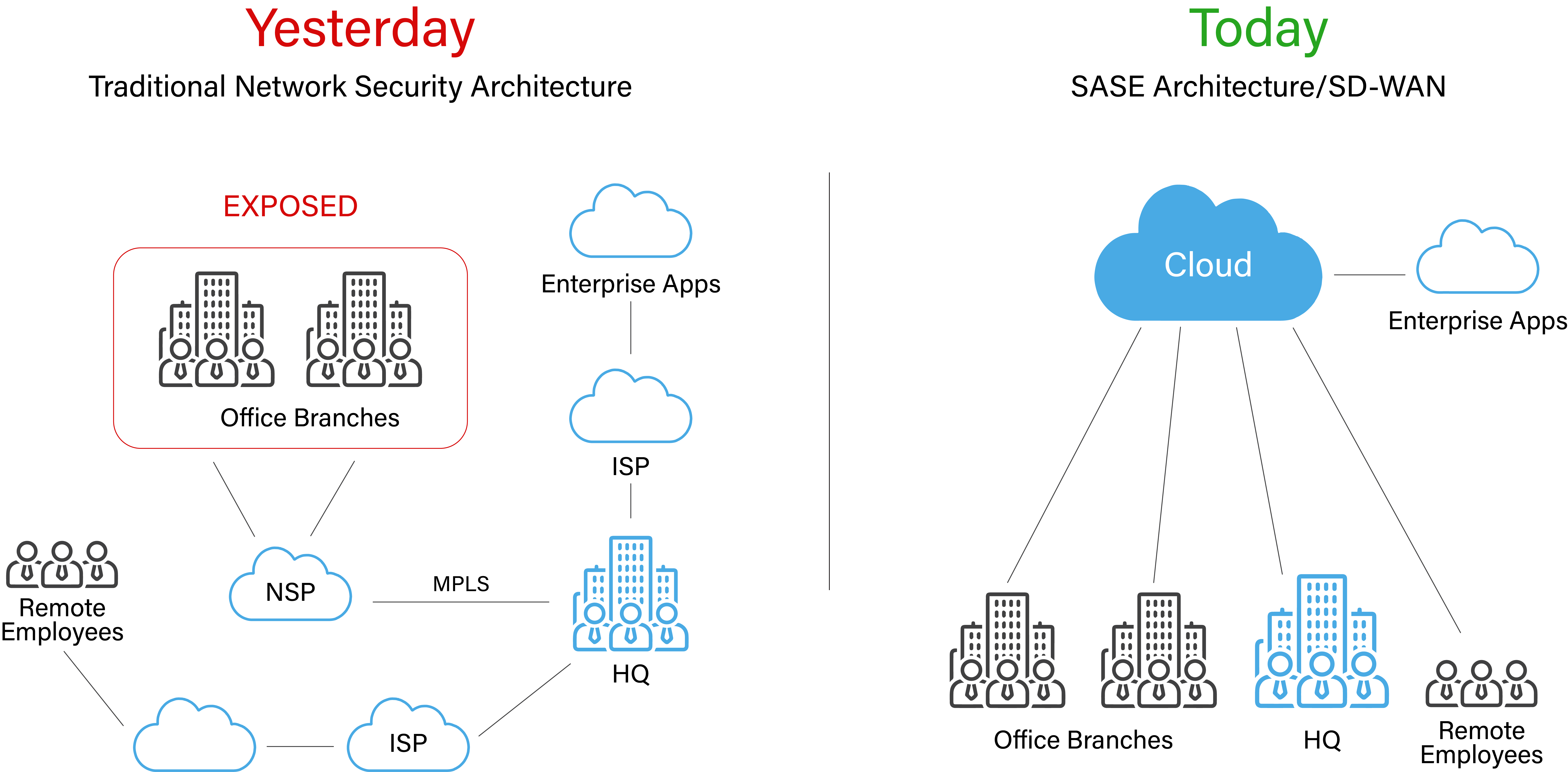
The Advantages of Cloud 802.1X Security for Enterprise Networks
Cloud-based 802.1X security offers organizations a handful of major advantages. Those advantages include the following:
⦁ Scalability
⦁ Reduced Complexity
⦁ Centralized Management
⦁ Improved Security
Scalability
The utilisation of cloud-based 802.1X security offers significant advantages in terms of scalability. Cloud-based security solutions offer adaptability and scalability, allowing for seamless adjustments to evolving business requirements and growth potential. The conventional security solutions deployed on-premise can be quite expensive and laborious to expand in proportion to the organization’s growth, unlike the alternative approach.
By implementing cloud-based 802.1X security protocols, organisations can efficiently manage personnel and equipment access, while also maintaining the flexibility to adjust resources as required. For enterprises experiencing rapid growth or fluctuating demand, this can prove to be particularly beneficial as it facilitates easy customization of the security framework to align with the evolving requirements.
The implementation of Cloud 802.1X security offers enhanced flexibility and agility in comparison to conventional on-premise systems. Enterprises can expeditiously integrate cloud-native security solutions with other cloud-based services such as identity and access management or threat detection to establish a comprehensive security framework. In addition, it is noteworthy that security solutions based on cloud technology often offer automated updates and patching. This can significantly contribute to ensuring that the security framework of the organization is constantly updated and fortified against the latest security risks.
Reduced Complexity
The streamlined deployment and management capabilities inherent in cloud infrastructure represent a significant advantage when implementing 802.1X security measures. To establish and sustain conventional on-premises 802.1X security, a substantial quantity of infrastructure and resources is required. The aforementioned encompasses a range of network infrastructure such as servers, switches, and other hardware components. Additionally, it necessitates the presence of proficient IT professionals to configure and maintain the system’s optimal functionality.
The implementation and upkeep of Cloud 802.1X security, in contrast, present a more streamlined procedure. Cloud-based authentication servers such as SecureW2’s Cloud RADIUS enable organisations to efficiently establish and administer their 802.1X security protocols without incurring the cost of expensive on-premise equipment. By implementing this measure, the burden on IT personnel can be reduced, enabling them to focus on other critical tasks instead of managing complex network equipment.
Utilizing digital certificates, end users can securely and seamlessly connect to the network via cloud-based 802.1X security measures. Certificates obviate the need for end users to manually input information, unlike passwords which necessitate memorization or resetting upon each connection. The implementation of this measure has the potential to optimize productivity by reducing time expenditure and minimizing aggravation.
Centralized Management
The centralised management feature is a pivotal benefit of cloud-based 802.1X security. Cloud-based infrastructure enables organisations to easily monitor and administer their security settings and policies, ensuring consistent maintenance and compliance across multiple locations.
Rapid and seamless provisioning and deprovisioning of personnel, devices, and access points is a key benefit of centralised administration for enterprises. Through the utilisation of cloud-based infrastructure, IT personnel can remotely manage user and device access via a centralised management console, without the need for physical on-site presence.
The task of overseeing security configurations and protocols across multiple on-premises sites can be a tedious and demanding endeavor. Manual configuration of each device and access point may be deemed necessary for IT personnel, and ensuring consistency across various locations can pose a challenge.
Improved Security
Regarding network security, it is imperative to acknowledge that cloud-based and on-premise 802.1X authentication solutions possess distinct benefits and drawbacks. When configured appropriately, on-premise solutions can offer a high level of security, despite the marketing claims of cloud-based solutions being more advanced.
The vulnerability of on-premise authentication mechanisms lies primarily in their physical security measures. To ensure robust access control, it is imperative that physical servers are housed in dedicated rooms equipped with appropriate locking mechanisms and other security features. A weak point in physical security might expose the entire authentication server, leading to unauthorised access and information leaks.
Cloud-based authentication systems provide enhanced security as the cloud service provider is responsible for managing and securing the infrastructure. In addition to enhanced adaptability and scalability, these solutions facilitate the development of tailored security protocols that align with the unique requirements of an enterprise.
It is imperative to acknowledge that cloud-based solutions may not consistently provide enhanced granular control across security policies compared to on-premise solutions. Whilst on-premise solutions may incur higher costs and have limited scalability, they can still provide a comparable level of security to their cloud-based counterparts.
SecureW2 Simplifies Network Security With Centralized Management and Advanced Threat Detection
The cloud-based security solutions provided by SecureW2 present a multitude of advantages for entities of different sizes. Our solutions offer centralised management of network security policies and settings, powerful threat identification and response abilities, and additional features to enhance your cybersecurity posture.
Our cloud-based solutions have been architected with a focus on seamless deployment and management, thereby alleviating the operational overhead on your IT personnel and enabling you to concentrate on your primary business goals. Furthermore, our cybersecurity solutions have the potential to offer a higher degree of cost efficiency compared to conventional on-site security solutions.
Contact us today to learn more about our cloud-based 802.1X solutions.