IP Spoofing Attack: Explained
One nasty strategy that needs our attention in the ever-changing environment of cybersecurity threats is IP spoofing. Given the increasing integration of the digital sphere into our everyday lives, it is important to comprehend the consequences of IP spoofing attacks.
Consider the case when a cybercriminal sets up a phony coffee shop with a free Wi-Fi sign to lure unwary customers into connecting to their network. This comparison highlights the seriousness of IP spoofing, a technique hackers use to impersonate authentic IP addresses to access networks without authorization to intercept and use private data. This article explores the topic of IP spoofing, revealing its complexities and emphasizing the criticality of taking proactive steps to avert such cyber threats.
What is IP Address Spoofing?
The act of creating Internet Protocol (IP) packets with a malicious source IP address to mimic a different computer system is known as IP spoofing, also known as IP address spoofing. IP spoofing gives attackers the ability to behave maliciously, frequently undetected. This might involve someone stealing your data, installing malware on your device, or bringing down your computer servers.
How Does IP Spoofing Work?
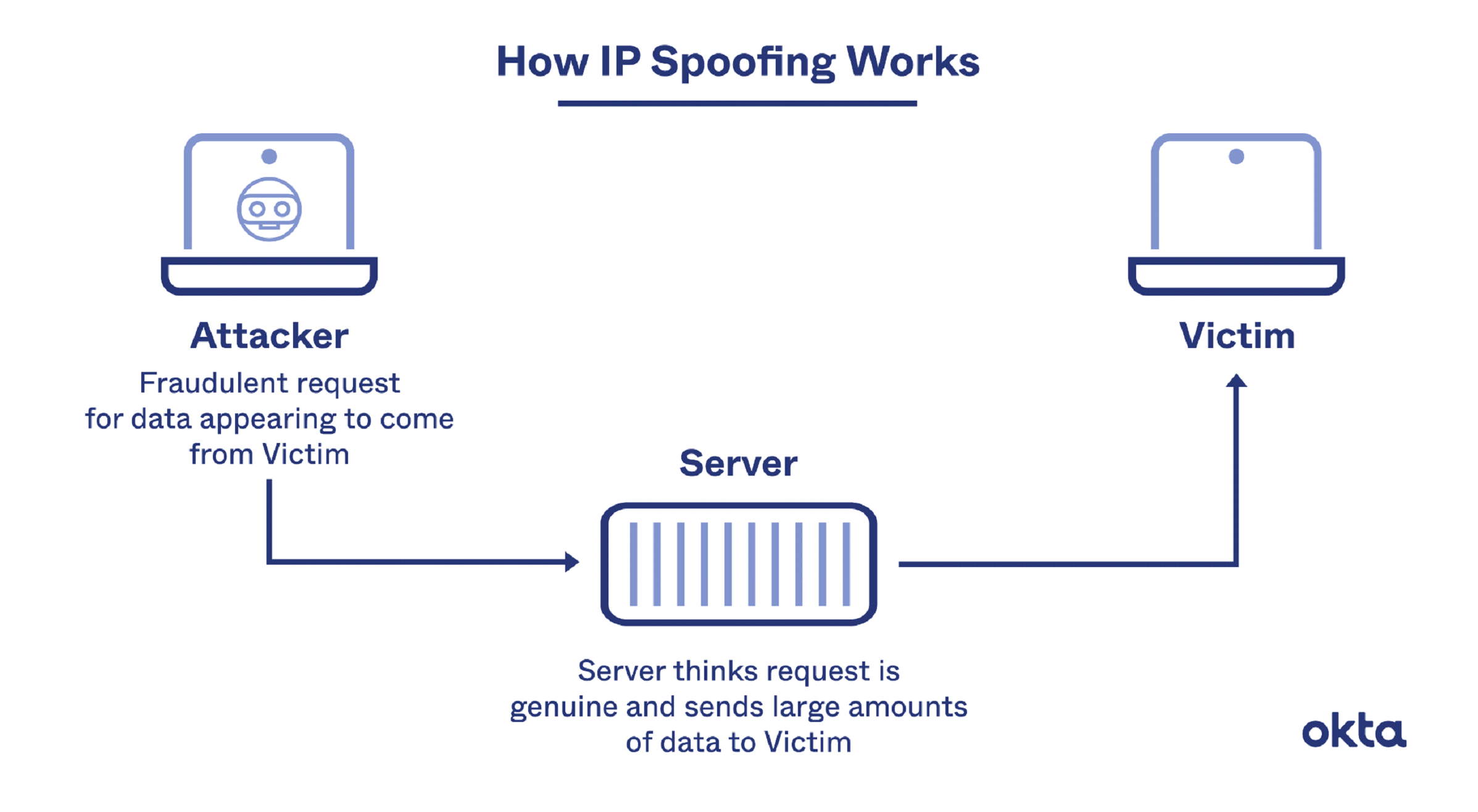
Let’s begin with some context: First, data is divided into several packets for transmission over the Internet traffic. Each packet is then delivered separately and combined at the end. The source and destination IP addresses are among the details in every packet’s IP (Internet Protocol) header.
IP spoofing is when a hacker uses tools to change the source address in the packet header so that the receiving computer networks believe the incoming packets are from a reliable source and accept it, such as another computer on an authorized network. As this occurs at the network level, there are no outward indications of manipulation.
IP address spoofing can be used to get around IP address authentication in systems that depend on verifying IP addresses before trusting connections between networked computers.. Once a hacker breaches the network device and makes it inside, looking into the system is simple. Due to this weakness, advanced security techniques, such as multi-step authentication, are gradually replacing the usage of basic authentication as a defense method.
While IP spoofing is frequently used by hackers to commit online fraud and identity theft or to take down business websites and servers, it can also have legal applications. For instance, businesses could utilize IP address spoofing to test websites before they go live. Testing the website and seeing whether it can withstand many logins without overloading would generate thousands of virtual users. Utilizing IP spoofing in this manner is not prohibited.
Types of IP Spoofing
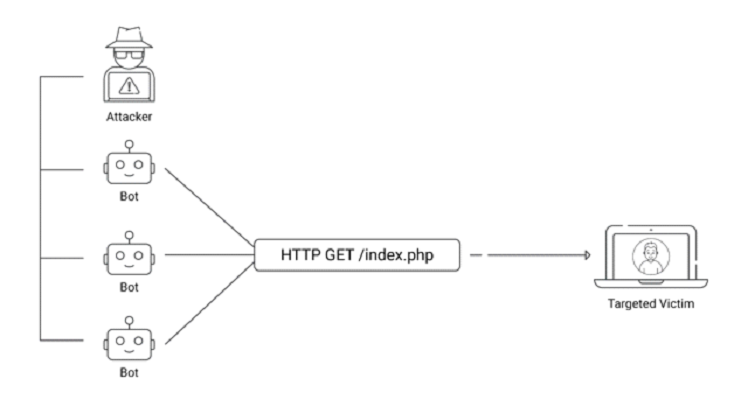
Distributed Denial of Service (DDoS) attacks
Hackers use fake IP addresses to flood computer systems with data packets during a denial-of-service attack. This enables them to remain anonymous while slowing down or crashing a network or website with high internet malicious traffic volumes.
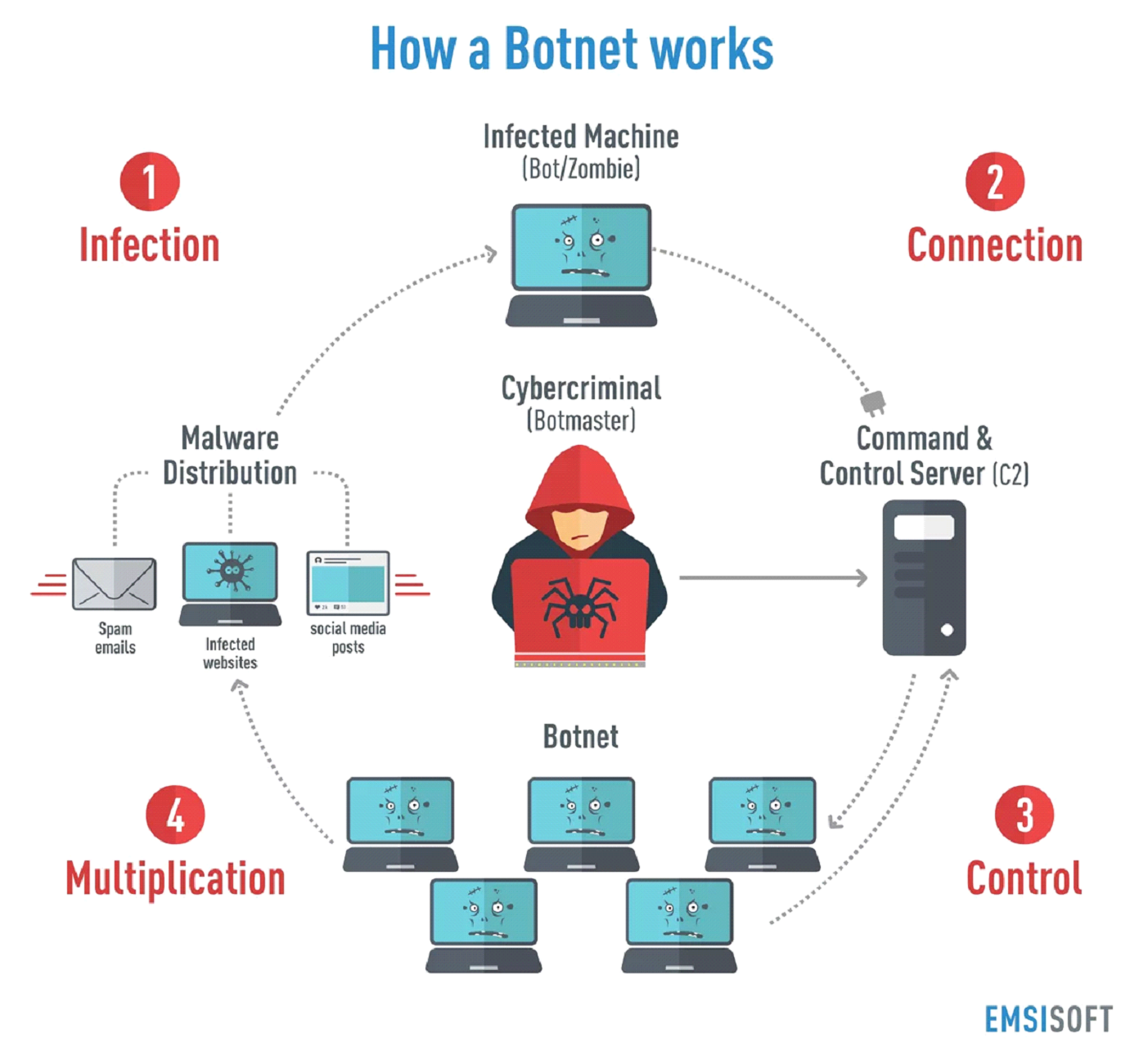
Masking botnet devices
By masking botnets, IP spoofing may be used to gain access to machines. A botnet is a collection of computers that hackers may take control of from one central location. A specialized bot that operates on each machine performs fraudulent activities on the attacker’s behalf. Because every bot in the network has a fake destination IP address, making the malicious actors difficult to identify, IP spoofing enables the attacker to conceal the botnet. This can extend an attack’s duration to increase its reward.
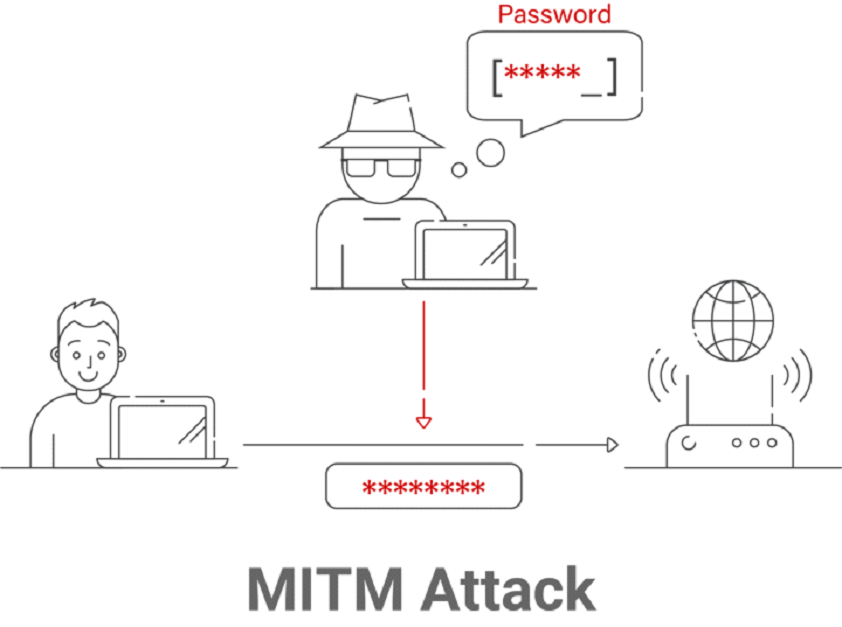
Man-in-the-middle attacks
‘Man-in-the-middle’ attacks are another malicious type of IP spoofing that aims to stop two computers from communicating, change the packets, and send them again without the original sender or recipient noticing. Attackers can follow every detail of a conversation if they manage to fake an IP address and get access to personal communication accounts. Data theft, user redirection to phony websites, and other activities are feasible from there. Man-in-the-middle attacks can be more profitable than other types of hacking because, over time, hackers amass a plethora of sensitive data that they may exploit or sell.
Examples of IP Spoofing
When attackers conduct a DDoS attack, they utilize fake IP addresses to overload computer network servers with fraudulent packets volumes too enormous for the destination computers to manage. Botnets are frequently used to deliver packets that are distributed globally. Large botnets may comprise tens of thousands of machines, each of which may impersonate many source IP addresses at the same time. The automated attacks are difficult to track down.
Following are some examples of how spoofing has been utilized in DDoS attacks:
GitHub: The GitHub was the target of what at the time was thought to be the largest DDoS attack ever on February 28, 2018. Attackers submitted requests to memcached servers, frequently used to speed up database-driven websites, by impersonating GitHub’s IP address. A factor of around 50 magnified the data the servers provided from those calls to GitHub. Consequently, up to 51 kilobytes were delivered to the victim for every byte supplied by the attacker. A malicious traffic spike of 1.35 terabits per second knocked GitHub down for ten minutes.
Tsutomu Shimomura: Hacker Kevin Mitnick used IP spoofing to target rival hacker Tsutomu Shimomura’s systems on December 25, 1994. By discovering the pattern of TCP sequence numbers that the computer creates, Mitnick took advantage of the trust connection that existed between the server and Shimomura’s X terminal computer. He sent an endless stream of SYN requests from fake IP addresses that were routable but inactive, flooding the system. The computer’s memory became full of SYN requests as it could not respond to the queries. We call this method SYN scanning.
How to Detect IP Spoofing
IP spoofing is difficult for end users to detect, which makes it risky. This is because Layer 3 of the Open System Interconnection communications architecture, or the network layers, is where IP spoof attacks are executed. This eliminates any outward indications of manipulation since faked internet connection requests frequently seem authentic from the outside.
However, businesses may examine endpoint traffic using network monitoring software. The most popular technique for doing this is packet filtering. Inconsistencies between a packet’s IP address and the required IP addresses listed on access control lists (ACLs) are detected by packet filtering systems, which are frequently found in routers and firewalls. Additionally, they identify false packets.
Ingress filtering and egress filtering are the two primary forms of packet filtering:
When a packet arrives, ingress filtering examines it to see if the source IP header corresponds to an allowed source address. Packets that appear suspicious will be refused.
Egress filtering scans outgoing packets for source IP addresses that differ from those on the company’s network. This is intended to stop insiders from using IP spoofing to conduct attacks.
What are Other Types of Network Spoofing?
Spoofing comes in various forms, and it frequently occurs on IP-based networks. However, most do not involve changing a packet’s IP address, known as IP address spoofing.
Other forms of spoofing that work with IP addresses are as follows:
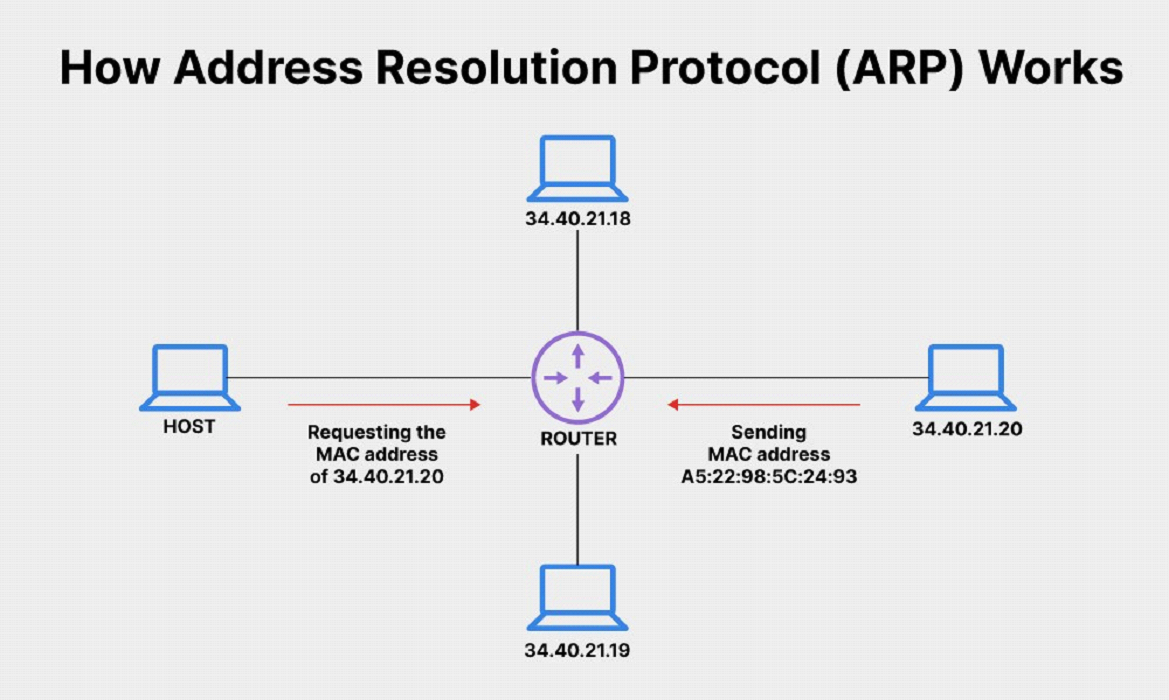
Address Resolution Protocol
When an attacker uses a local area network (LAN) to transmit bogus ARP messages, it’s known as an ARP spoofing attack. This ties the attacker’s media access control address (MAC address) with the IP address of a genuine computer or server on the network. This happens in the Ethernet frames carrying that protocol at the data link layer.
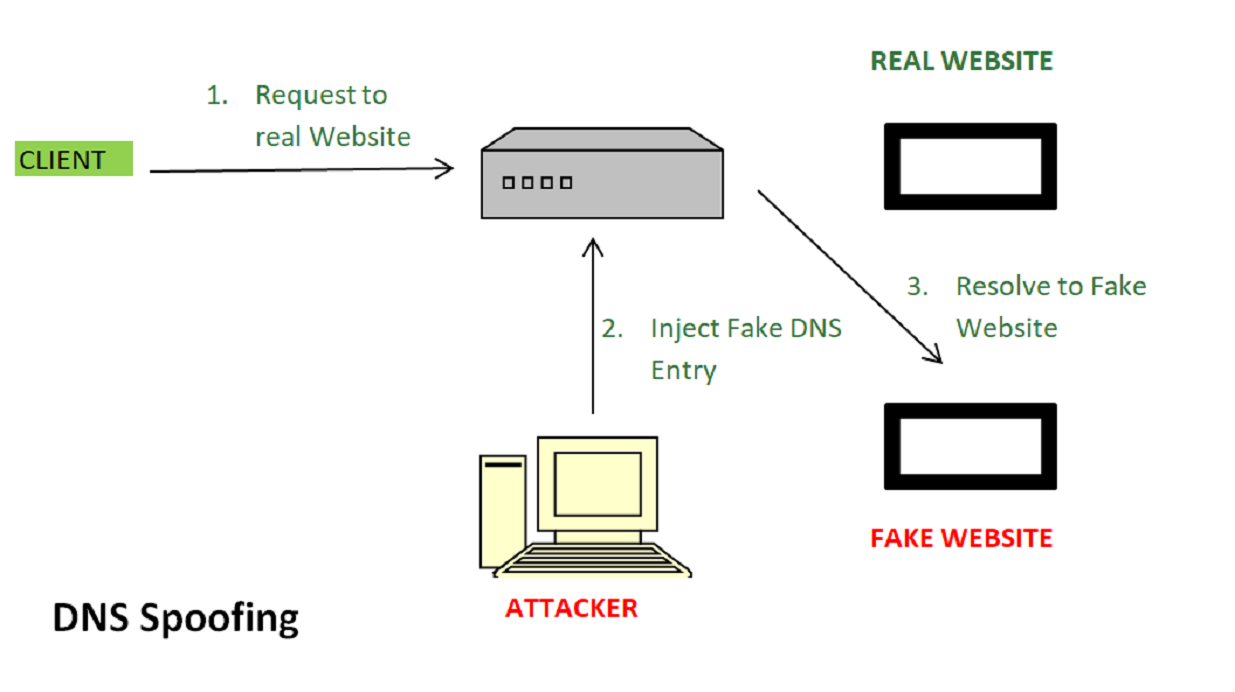
Domain Name System
A DNS spoofing attack records and directs internet traffic toward phony servers rather than real ones. Webpages are mapped from IP addresses to DNS servers, which users access to access webpages. The malicious actor can insert fictitious DNS entries into DNS servers, causing users to access the server and be routed to the hacker’s inserted site instead of their intended one.
Other spoofing techniques target various kinds of data and might not even remotely interfere with IP addresses. Here are a few instances:
Caller ID.
Caller ID spoofing modifies the caller ID to simulate a call originating from a different location. This frequently occurs when telemarketers dial the target’s area code.
Email.
Attackers tamper with email header data to make it appear that a different address sent the message. A phishing assault frequently includes a spoof email that links to a replica of a website that looks to be the original. The fake website aims to deceive its intended audience into providing login credentials or other confidential data.
Global positioning system (GPS).
The act of deceiving a mobile device into displaying a position that differs from its actual geographic location is known as GPS spoofing. A third-party program that generates distinct location and navigational data can be used.
Short Message Service (SMS).
SMS or text message spoofing is changing the sender’s phone number to hide their actual number. In their communications, attackers could include links that lead to malware downloads or phishing websites. Using this technique, legitimate organizations may also create an easy-to-remember alphanumeric ID instead of a phone number that is hard to remember.
URL.
In this kind of spoofing, attackers utilize a nearly exact replica of a legitimate URL, just with a few characters altered. The idea is to trick the victim into visiting an authentic webpage and then get them to submit sensitive data on it.
How to Prevent Spoofing Attacks
You can stop spoofing assaults by using smart security tools. For example, most phishing emails will not get through a spam filter or your mailbox. Several businesses use similar software and even certain network providers to prevent spam calls from getting to consumers’ phones. Software that detects spoofing attempts may offer more defense against certain spoofing types previously discussed, improving your capacity to identify and stop them before they can do any damage.
A few recommended practices might lessen the chance that you will become a target of a spoofing attack. Relying on trust relationships for network authentication should be avoided wherever feasible. If not, attackers may use those connections to pull off effective spoofing attacks. Because packet filtering can identify and reject packets with contradicting source address information, it can stop IP spoofing assaults. Using network protocols that use cryptography, such as Secure Shell (SSH) and HTTP Secure (HTTPS), can provide your environment with an extra degree of security.
Safeguard Your Digital Frontier with SecureW2
When it comes to understanding the complex world of cybersecurity, IP spoofing is one dark threat that requires our combined attention. Safeguarding our digital lives requires knowing IP spoofing and avoiding it, much like we would secure our houses against prospective intruders.
In this endeavor to achieve digital security, SecureW2 proves to be a reliable partner. Using state-of-the-art techniques like data encryption via certificates and 802.1x EAP-TLS authentication, SecureW2 significantly reduces the risk of IP spoofing by helping prevent devices and credentials from being compromised.
Contact us today to learn more about how certificate-driven security can protect your organization’s devices and networks from compromise.