A Guide to Integrate Azure AD For RADIUS Authentication Easily
- Since Azure AD native authentication (i.e. SAML) isn’t RADIUS integrated, leveraging digital certificate-based RADIUS authentication is the industry’s gold standard with passwordless security.
- Advanced Cloud RADIUS can tie in natively with Azure AD to provide granular access control by using security policies that reference Azure AD.
- Leverage your Intune/MEM (or other MDM) to deliver and manage digital certificates for RADIUS authentication.
Are you moving all your applications to the cloud to authenticate against Azure AD, but don’t know how to do Wi-Fi or RADIUS with your Azure AD? Don’t worry, you’re not alone. Hundreds of organizations contact us every month with this problem.
On their own, organizations have performed an LDAP sync, duplicating their Azure AD on-premise as a way to tie network authentication to their cloud Azure AD. For organizations with existing credential-based 802.1X, this can be a good temporary solution that allows them to move to Cloud Azure AD, but they still have to use their legacy servers. Configuration guides are hard to find and what you can find are difficult to configure, according to a Microsoft forum about the Azure AD-LDAP synchronization.
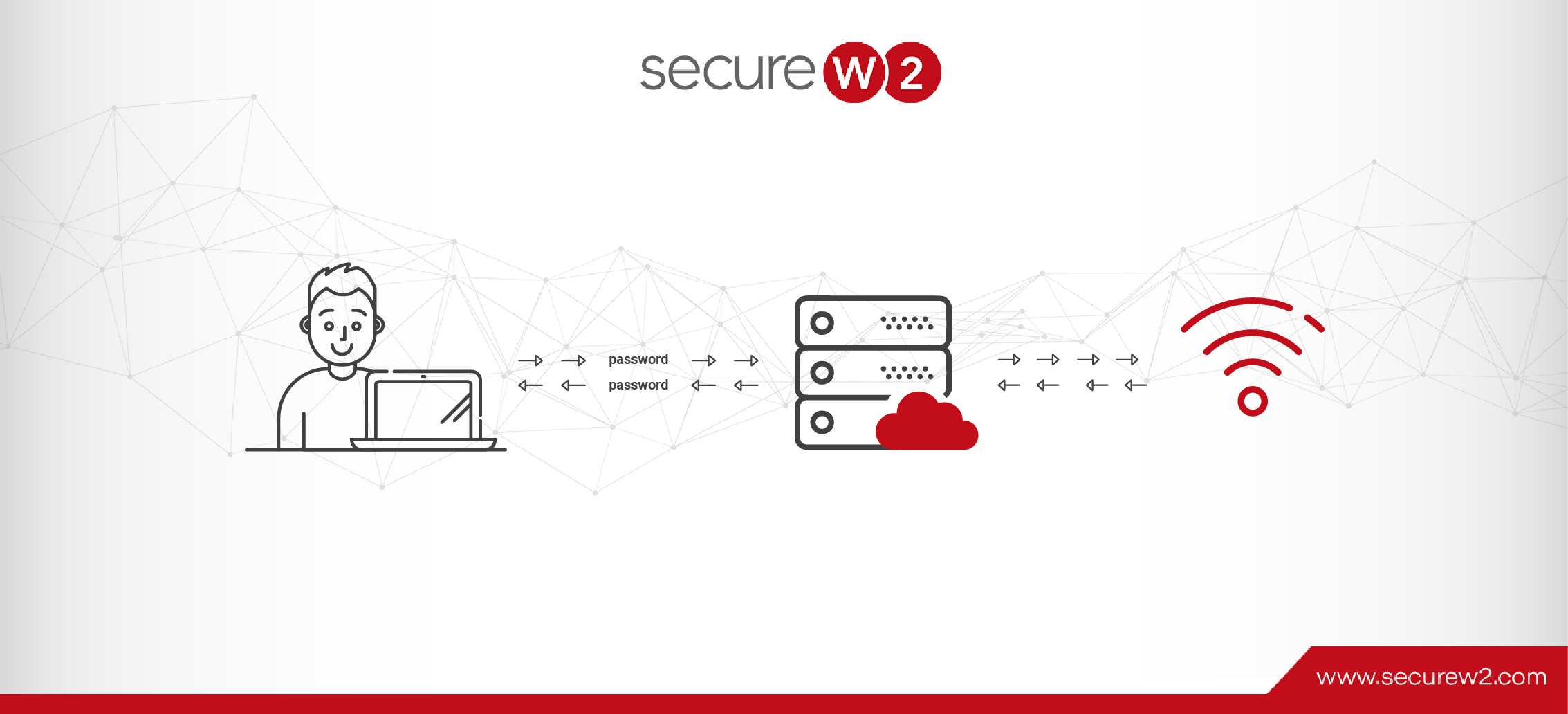
We’ve shown Azure customers how they can leverage digital certificates to tie Azure AD to network security. Users/devices will perform a one-time enrollment process with their Azure AD credentials to get an ultra-secure X.509 Digital Certificate. This certificate can now be presented to the RADIUS Server as a more secure way to validate active users in your organization.
How Certificates Enable RADIUS Authentication with Azure AD
Apart from being an easy way to tie RADIUS Authentication to Azure AD, certificates have many benefits that passwords lack. They improve user experience, over-the-air security, decision-making context, and are future-proof. Microsoft has recommended organizations move toward a passwordless authentication method, such as certificates.
Setting up a Public Key Infrastructure (PKI) allows you to easily issue and manage certificates for all your users and devices. You can integrate a Managed PKI to directly communicate with your Azure AD provider to enroll the appropriate certificate to each user based on their standing in your organization.
Once the device is enrolled with a certificate, Cloud RADIUS can be configured to authenticate users using their issued certificates. Certificates allow admins to segment users into separate groups. You can place your employees into different groups (HR, Marketing, IT, Accounts Receivable) and configure RADIUS to apply specific network policies to each respective user. This can be done at the time of authentication so users will be connected to Wi-Fi and given the correct amount of network access in seconds. Cloud RADIUS goes beyond perimeter security.
Leverage Endpoint Manager (or other MDMs) for RADIUS
For organizations with EM/Intune/GPO or other MDMs, you can push certificates, policies, and 802.1X configuration settings so you can easily control access for every managed device. Intune devices are guided through the certificate enrollment (+renewal) process. A Cloud RADIUS server can be configured to authenticate the user using their issued certificates. Cloud RADIUS can directly communicate with Azure AD in order to authenticate the user’s identity for Wi-Fi/VPN access.
Below is a high-level overview of certificate enrollment/renewal and the ongoing authentication process.
For a more detailed guide, check out how to use SCEP to enroll certificates on Intune devices.
What If I Need to Connect Unmanaged Devices?
Enterprises that need to onboard unmanaged devices can integrate modern onboarding solutions that direct users to download a dissolvable client onto their device and enter their credentials. The client then verifies the user against their Azure AD and assigns a custom certificate filled out with a user’s identifying information. The certificate will then be used by the RADIUS server to authenticate the user.
SecureW2’s self-service software [JoinNow MultiOS] allows users to configure their devices for 802.1X security. After downloading the JoinNow MultiOS Dissolvable Agent, users are redirected to an authentication portal where they enter their Azure AD credentials. The credentials are verified against your Azure AD and user/device information is applied to the issued certificate with the appropriate policies. The certificate is then installed in the device’s key store and as always the private key is generated and locked to the device.
Setting Up RADIUS Lookup in Azure AD
We’ve heard from many Azure customers that it’s difficult to set up RADIUS authentication because Azure AD is limited compared to AD when it comes to supporting WPA2-Enterprise and 802.1X. Plus, customers need to move away from passwords as a form of authentication and replace them with digital certificates.
Here’s a quick overview of what you need to do:
- Create an Azure AD Identity Lookup Provider
- Configure RADIUS Lookup in Azure Portal
- Configure Azure AD Attribute Mapping in SecureW2
- Configure Azure AD Policies in SecureW2
For the full documentation, head over to Configuring Dynamic RADIUS with Azure AD to Support WPA2-Enterprise.
Create an Azure Identity Lookup Provider
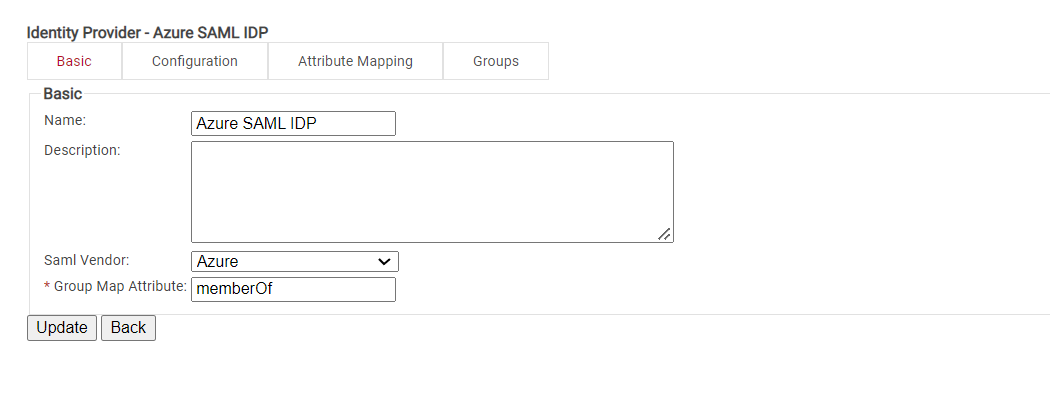
“Creating” your Identity Provider (IDP) in SecureW2 tells Cloud RADIUS how to connect to your Azure AD user database, verify user credentials, and issue certificates.
Configure RADIUS Lookup in Azure Portal
SAML applications provide a secure and efficient method for confirming the identity of valid users within the Identity Provider (IDP). By utilizing the SAML protocol, network admins can guarantee that only those users who are identified within the IDP are able to access the secure network. Their devices can also be enrolled for certificates, enabling highly secure passwordless authentication.
Configuring RADIUS Identity Lookup with Azure AD Attributes & Policies
Network authentication with Azure AD is powerful because admins can use identifying attributes from Azure AD in your network policies. By mapping Azure AD attribute mapping with SecureW2, admins can segment users/devices/groups into their own VLANs, ensuring no user can access resources which they aren’t allowed.
Cloud RADIUS can be configured to check the user status every time the user requests authentication to the network so they can be segmented properly. Below, we provide a quick guide on how to use Azure AD attributes to create network policies.
Configure Azure AD Attribute Mapping
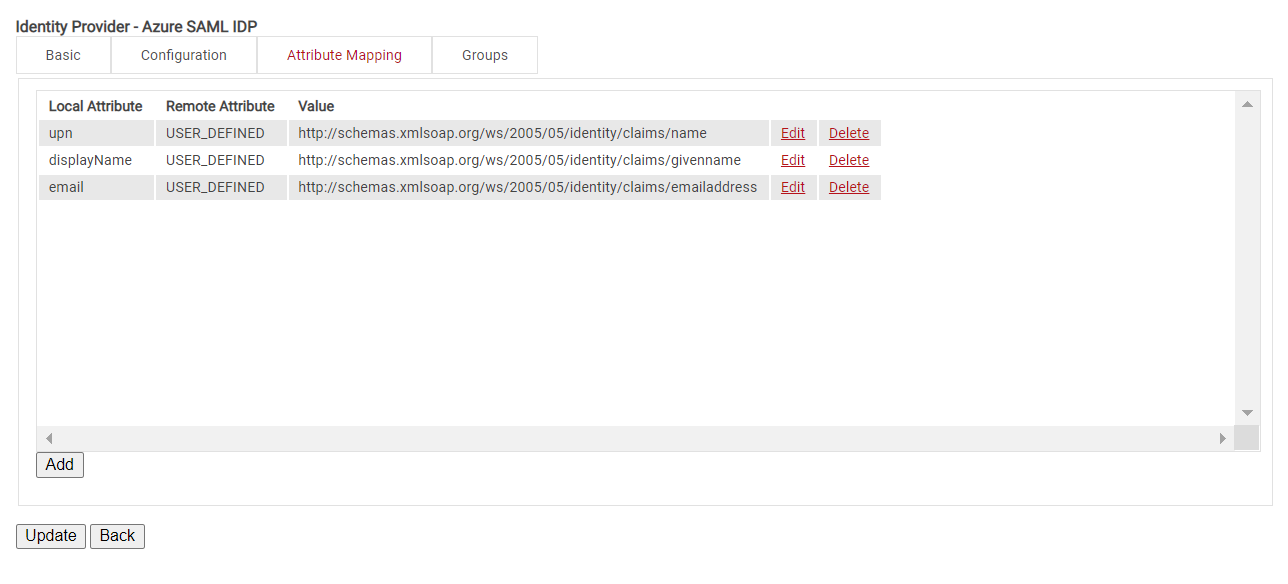
This is where you can map out the attributes sent by Azure AD and encode them onto certificates. Customizable attributes and schemas allow you to create “templates” for new objects that streamline the provisioning process. For example, a user assigned the “Marketing” department value can automatically be assigned new properties according to the synchronization rules when they are reassigned to the “Sales” department to reflect their new permissions.
Configuring Groups
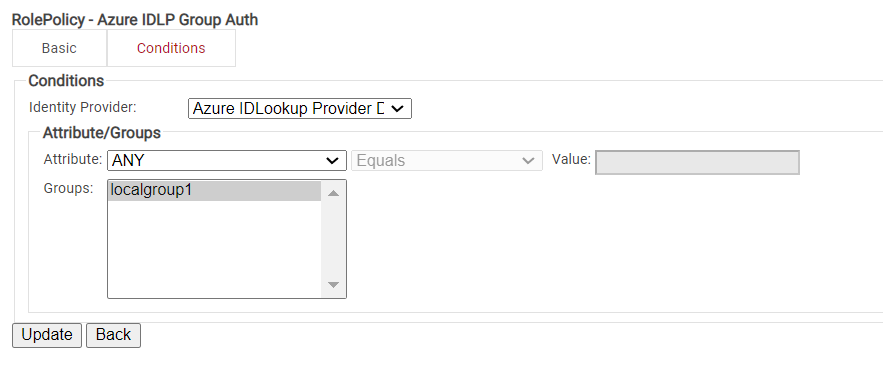
Cloud RADIUS can perform a User Group Lookup so we can create network access policies based on the Groups a user is in.
Configuring Policies
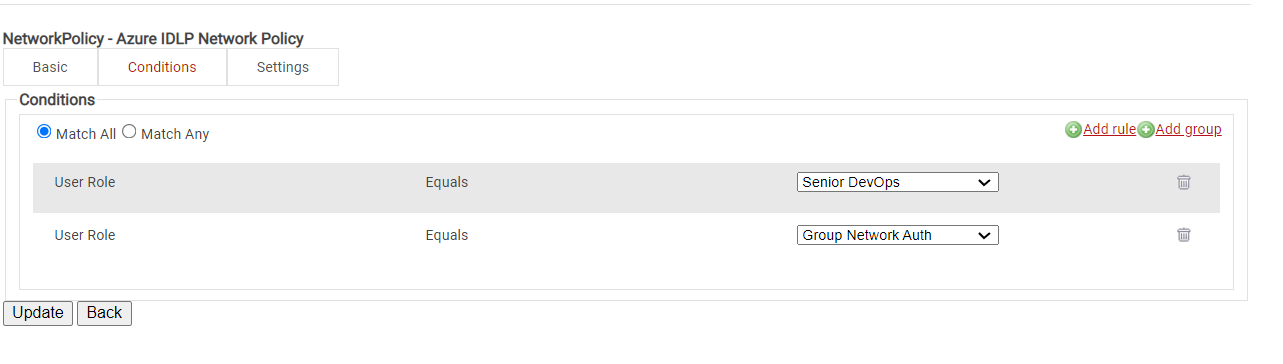
Cloud RADIUS can segment users and restrict/allow resources based on information stored in their directory entry.
The following policies need to be configured:
- Account Lookup Policy
- User Enrollment Role Policy
- Network Authentication Policies
- Default Fallback Role Policy
- Network Policy
To see the step-by-step process for each Policy, go to the Configuring Policies section on Configuring a Cloud RADIUS with Azure AD to Support WPA2-Enterprise.
Network Policies
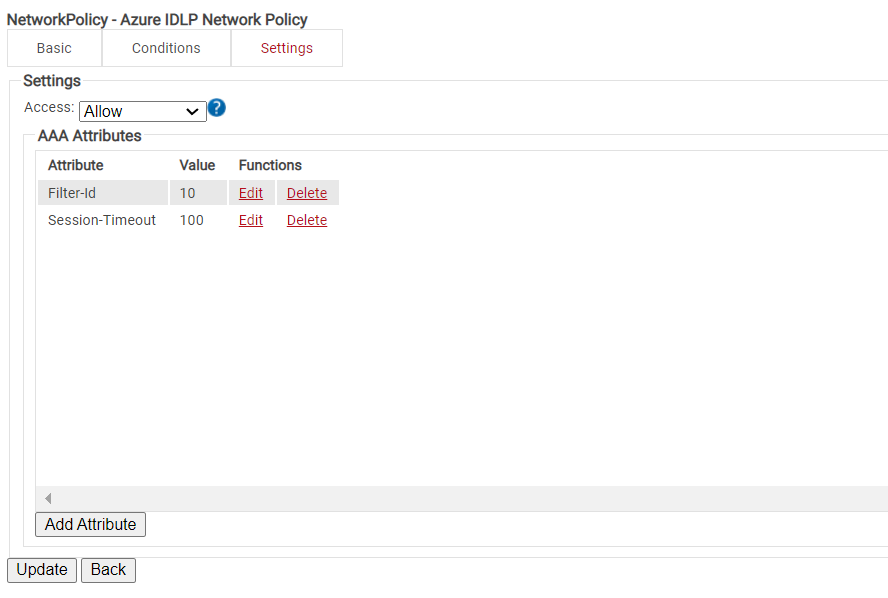
The purpose of a Network Policy is to specify how Cloud RADIUS will authorize access to a particular User Role. A typical Network Policy would say something like: “If User Role = Staff, authorize access and assign them to VLAN 2”. You can configure any RADIUS Attribute to be sent to the wireless controller. If you leave the attribute section blank, it will just send Access-Accept.
Passwordless RADIUS with Azure AD
Setting up a secure, RADIUS-backed network can be daunting, but with SecureW2, it’s remarkably straightforward. You can have your network up and running in hours, fortified with industry-leading security measures. Our dedicated support team is always on hand to assist with any questions or issues that may arise, ensuring that your setup process is smooth and stress-free. We pride ourselves on our seamless integration with all SAML identity providers, which means you can avoid the usual headaches and complications of connecting different systems.
At SecureW2, we understand that every organization has unique needs and budget constraints. That’s why we offer a range of affordable solutions tailored to fit organizations of all sizes. Whether you’re a small business or a large enterprise, we have a pricing plan that can work for you.
We have affordable solutions for organizations of all sizes; check out our pricing here to see if we can help. Let SecureW2 be your partner in achieving a secure, efficient, and hassle-free networking environment.