Types of WPA2 Authentication
Wireless encryption standards have developed to account for shifting network needs, emerging security threats, and discovered flaws in older encryption methods.
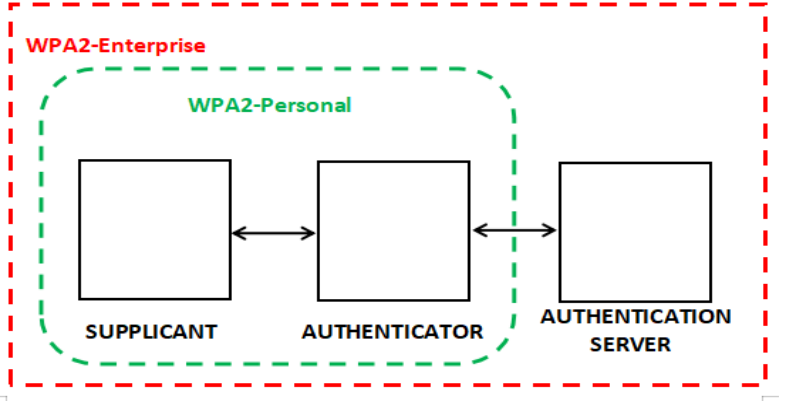
WPA2-PSK/Personal and WPA2-ENT are the two variants of the WPA2 protocol that are in use today and provide different levels of security. WPA2 Enterprise uses IEEE 802.1X to deliver enterprise-grade authentication, and it was created specifically for use in businesses. WPA2-Personal is designed for use within the home and uses pre-shared keys (PSK).
But many organizations find themselves asking which one is more secure for their own use. In this article, we’ll be examining both types of WPA2 authentication, including their use cases and security.
What Is WPA2 Authentication?
Wi-Fi Protected Access 2, or WPA2, is the next iteration of the Wi-Fi Protected Access security standard and offers a higher level of protection than its predecessor, WPA.
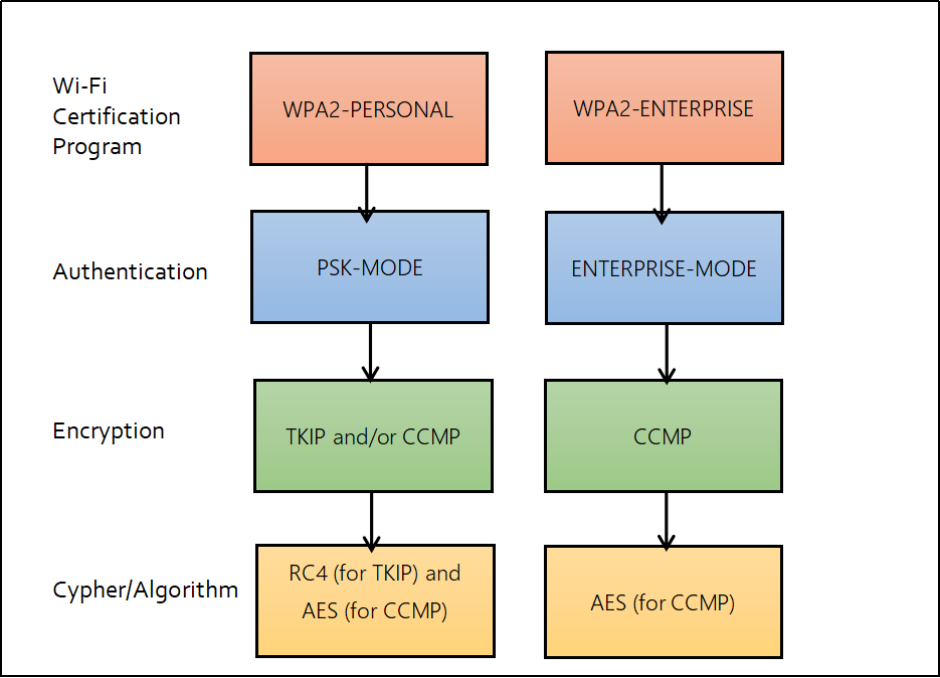
WPA2 was chosen over WPA because it uses the more secure Advanced Encryption System (AES) instead of the less secure Temporal Key Integrity Protocol (TKIP). AES provides strong encryption that keeps private information safe.
However, WPA2 has a couple of different authentication protocols of its own that are used commonly. Pre-shared key (PSK) and Enterprise (ENT) see wide use in homes and businesses alike. These authentication protocols come into play when a user connects or reconnects to the network.
Wi-Fi Protected Access-Pre-Shared Key or WPA2-PSK
Since WPA2-PSK was developed in 2004, it remains a popular protocol for securing wireless networks using a predetermined security key. Every wireless client’s encryption key is generated using the passphrase and the network’s service set identifier (SSID) via a TKIP protocol. In addition, WPA2-PSK requires a router password to be between 8 and 63 characters extended to encrypt network traffic.
WPA has a more robust encryption technique than WEP, making transmitted data more challenging to decipher. As a result, the only way a hacker could crack the password would be via exhaustive trial and error.
However, using a PSK is less secure since everyone uses the same password. Anybody who distributes the password too freely might jeopardize everyone’s security. Using passwords also leaves your network vulnerable to many Layer 2 attacks.
Moreover, due to password leaks, the cumbersome roll-out of updated passphrases follows. Also, brute-force attacks may be used to decipher passcodes.
What Is a Layer 2 Attack?
Open Systems Interconnection (OSI) paradigm layers are in constant contact. A network’s physical layer, or “Layer 2,” is responsible for moving data between devices. The host’s physical location is what is referred to here.
Layer 2 is responsible for transmitting the raw data from the physical layer to the network layer. Therefore, disabling the network or compromising network users to harvest critical information like passwords is a prevalent security concern in the Layer 2 domain. Regrettably, it also has one of the lowest probabilities of being discovered.
The following are some Layer 2 attacks that can occur on the network:
- Switch Spoofing
- STP (spanning tree protocol) attacks
- Spoofing of DHCP or Dynamic Host Configuration
- Spoofing of Media Access Control (MAC)
- A double tagging
- Spoofing of ARP (Address Resolution Protocol)
PSK Network Attack Scenario
As an example of the drawbacks of WPA2-PSK, imagine a small company with just WPA2-PSK protection in place. Everyone from the receptionist to the CEO uses the same password to access the company network. What exactly is the issue?
Using a passphrase becomes problematic when an insider threat exists, such as a disgruntled worker who hacks into other devices on the corporate network or a malicious outsider who gains access to the company’s intranet and attempts to steal sensitive information. Even worse, a hacker may get simple access to the network and inflict significant financial damage due to the theft of company secrets if WPA2-PSK is hacked.
Some business owners think WPA2-PSK network security is adequate since they migrate their sensitive data to the cloud. However, transmitting credentials over a cloud environment makes them more susceptible.
Wi-Fi Protected Access-Enterprise or WPA2-ENT
This protocol was introduced in 2004 and is regarded as a gold standard for wireless network security. WPA2 Enterprise often verifies network users using a RADIUS server or other authentication services. In addition, it uses 128-bit encryption keys and dynamic session keys to safeguard wireless networks and sensitive corporate information. Furthermore, it selects an authentication type that matches the authentication protocol used by the 802.1X server.
WPA2-ENT safeguards data by making passwordless authentication possible through digital certificates. Digital certificates prevent man-in-the-middle attacks from intercepting crucial information like credentials because credentials are not being used in the first place. This means that hackers cannot steal the password over the air and use it to access other resources.
Additionally, these authentication techniques may be extended to the wired network, and VLANs can be dynamically allocated. It also enables additional security to support Network Access Protection (NAP).
How Does WPA2-Enterprise Work?
RADIUS servers are required for the implementation of WPA2-Enterprise since they authenticate users gaining access to a network. The authentication mechanism uses the 802.1X policy as its foundation and is made accessible in a number of different systems that have been dubbed EAP. When the authenticity of each device has been confirmed, a private, encrypted tunnel is used to link it to the network.
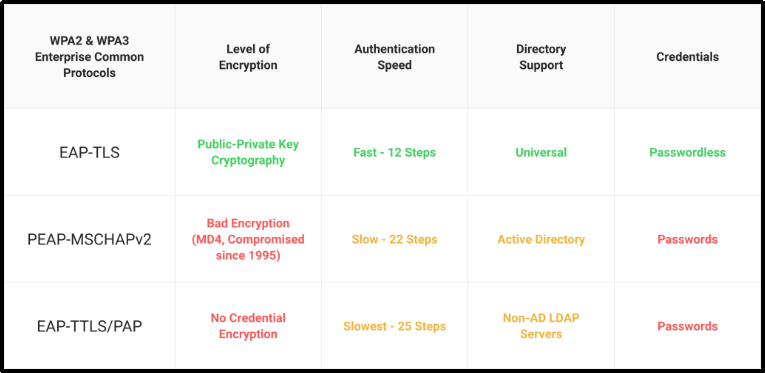
To authenticate, WPA2-Enterprise needs the usage of a secure EAP mechanism. PEAP-MSCHAPv3, EAP-TTLS/PAP, and EAP-TLS are the most often used. It may accept a broad range of identities and allow MFA for more secure authentication.
WPA2-Enterprise With Certificate-Based Security
A superior alternative to using passwords is distributing client certificates. Certificates are highly efficient and convenient for user authentication because the RADIUS can immediately identify the user and device requesting network access.
Using Certificates for authentication takes the burden off the user and simplifies setup. The need for a reset policy is removed when using certificates. Users are given temporary network access after obtaining a certificate, which has been verified.
EAP-TLS eliminates the possibility of over-the-air credential theft, so it is often considered one of the most secure EAP protocols. Furthermore, due to the elimination of password-related disconnects brought on by password-change laws, it also provides the best possible user experience.
Although certificate-based authentication has historically had a bad reputation for being difficult to implement and maintain, EAP-TLS has now been shown to be one of the most user-friendly authentication methods available. Authentication protocols are only as good as their implementation, so choosing a RADIUS solution that adheres to the zero-trust philosophy is crucial. Next, we will analyze and contrast the most popular RADIUS integrations for zero-trust authentication.
Move From Traditional PSKs to Certificate-Based WPA2 Enterprise
SecureW2 includes all the necessary tools for establishing a certificate-driven WPA2-Enterprise network. Our set-and-forget architecture is intended for speedy installation and simple lifetime administration. Furthermore, the given infrastructure is compatible with all major network infrastructure vendors, allowing users to build upon the current system instead of rebuilding everything.
SecureW2’s most valuable feature is its efficient certificate solutions. The launch of certificates is simplified for administrators and end-users. The administration site allows users to set up and receive certificates, while administrators may administer the network with tools. Check out SecureW2’s pricing page to discover your network requirements.