
RADIUS Change of Authorization: Explained
RADIUS server authentication on its own greatly enhances network security by ensuring only legitimate users can access your Wi-Fi and VPN. It continues to see wide use today, and as network security advances in response to evolving cybersecurity threats, so, too, has RADIUS evolved.
New features and improvements are continuously being introduced, including the concept of Change of Authorization (CoA). CoA gives RADIUS a much more active role in your network’s security by giving it the ability to make authorization changes dynamically. In this article, we’re going to take a closer look at what RADIUS Change of Authorization means, and how it can impact the security of your Wi-Fi or VPN.
What is RADIUS Change of Authorization?
In a nutshell, Change of Authorization allows RADIUS servers to apply policy changes to devices that have already authenticated and are connected to your network.
To understand exactly what RADIUS Change of Authorization is and why it’s beneficial, you’ll need to have a grasp on how typical RADIUS authentication works. Because certificate-based authentication (CBA) is more secure than the alternative of credentials (usernames and passwords), we’ll give you a quick overview of the steps involved in RADIUS authentication when you’re using digital certificates.
At a high level, RADIUS authentication with certificates follows these steps:
- The device attempts to connect to your network and presents a certificate to the RADIUS server.
- The RADIUS checks that the device’s certificate is unexpired.
- If the certificate is unexpired, the RADIUS then checks to see if the certificate is on the Certificate Revocation List (CRL) to confirm whether or not it has been revoked.
- If the RADIUS supports Identity Lookup (such as our Cloud RADIUS), it will check your directory in real-time to confirm if any other policies need to be applied before authentication.
Once all the above steps are completed, and the device is connected to your network, it stays connected to your network until it disconnects and re-authenticates. Unfortunately, a lot can occur while a device is connected to your network. It can become infected with malware, it can fail to meet compliance standards, or the user’s status within the organization can change – just to name a few possibilities.
In all of the above scenarios, administrators would want either revoke network access entirely or change what the user has access to. Without forcing the device to re-authenticate, though, these necessary changes to authorization cannot be applied – unless your RADIUS is capable of Change of Authorization.
How Does RADIUS Change of Authorization Work?
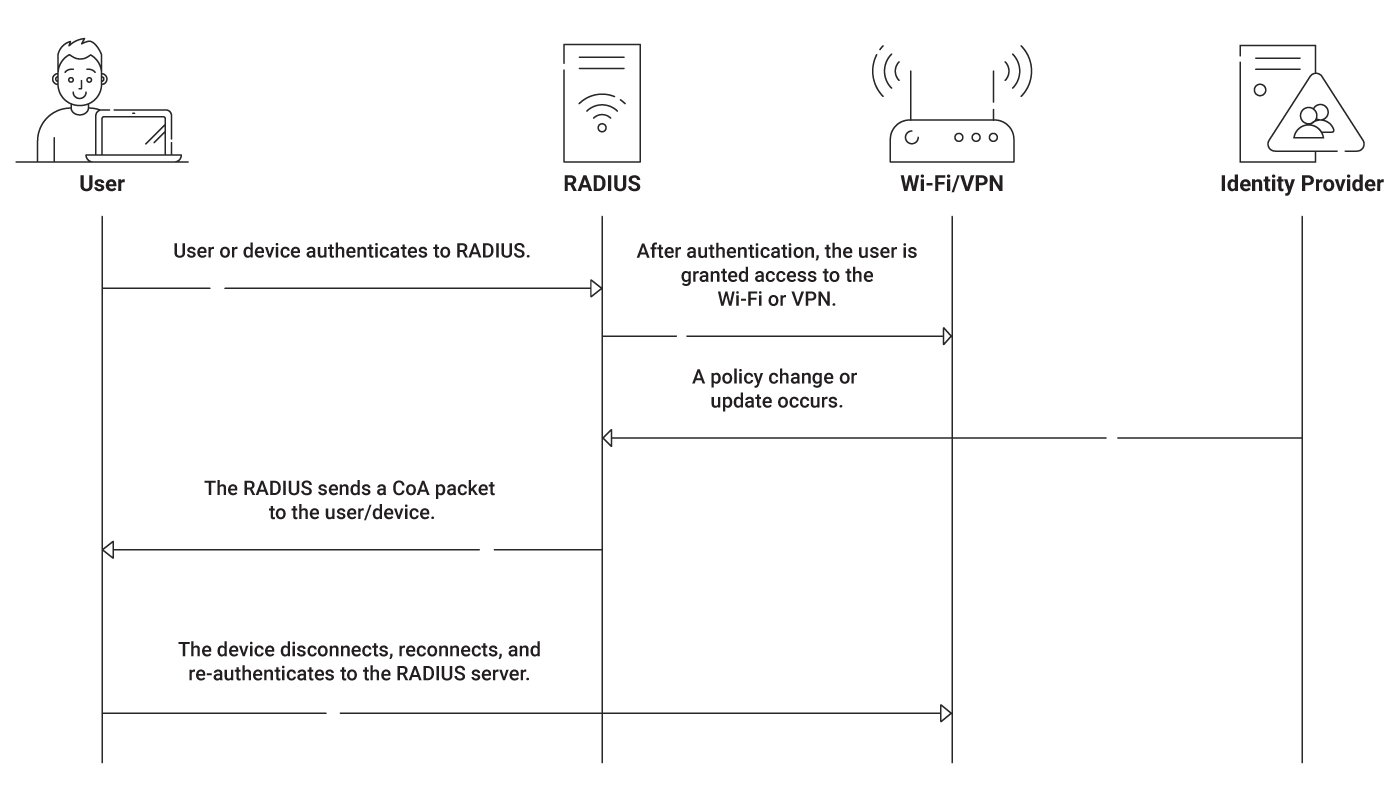
The actual process behind Change of Authorization is surprisingly simple. Once a device is connected to your network, CoA follows these general steps:
- Some kind of policy change occurs that impacts the connected device.
- The RADIUS server is notified of the policy change (commonly by infrastructure such as your MDM, your IDP, or even your CAs).
- The RADIUS sends out a CoA request packet to the impacted device
- The device is forced to disconnect, re-connect, and re-authenticate to the RADIUS again.
- Updated authorization is applied at the time of the new authentication.
In short, CoA basically allows the RADIUS to force re-authentication. This means that you don’t have to rely on end-users to manually disconnect and reconnect their devices, nor do you have to manually do the same for IoTs on your network.
Do You Need RADIUS CoA?
Change of Authorization is a relatively recent feature for RADIUS servers, and it hasn’t yet seen widespread adoption. It’s true, however, that CoA would offer a range of benefits to organizations that have deployed RADIUS security. Here are just a few examples of use cases for the feature:
- Dynamically blocking non-compliant devices from your network.
- Reassigning users to different VLANs on the fly.
- Updating access and authorization levels whenever necessary.
Do I need a RADIUS Server for CoA?
Technically, almost any network access server should be able to perform a change of authorization. But if you are looking for change of authorization capability without first implementing a RADIUS server, you’re putting the cart ahead of the horse.
Deploying RADIUS server authentication alone is a huge advantage for your network security. It offers a secure authentication method for your Wi-Fi and VPN. When tied with digital certificates (like Cloud RADIUS was built for), it can help eliminate credential theft. If your RADIUS is cloud-based, all your locations can authenticate to it.
Cloud RADIUS is also an example of a RADIUS service that strives to regularly add new and innovative features. Identity Lookup allows Cloud RADIUS to authenticate users in real-time with your IDP, promoting the security of RADIUS even further and keeping your network up-to-date. The recent addition of RADIUS over TLS, also known as RadSec, to Cloud RADIUS makes it an excellent solution for roaming environments, too.
Change of Authorization can be beneficial for RADIUS. But it’s also more useful in scenarios where users and devices wouldn’t regularly be re-authenticating on their own.
Strengthen Your Network Security Today with Cloud RADIUS
The RADIUS protocol has a lot to offer any organization’s network security, and it continues to grow. SecureW2’s Cloud RADIUS exemplifies the evolving nature of RADIUS. It was designed for certificate-based authentication, it can integrate with any infrastructure, and its Identity Lookup feature makes real-time communication with your IDP at the time of authentication possible.
We also pride ourselves on keeping on top of current trends in cybersecurity, updating Cloud RADIUS accordingly. Recently, we implemented RadSec functionality to give Cloud RADIUS that extra layer of security. If you’re interested in deploying CoA with Cloud RADIUS, our engineers would be happy to work with you. We’d love to show you Cloud RADIUS in action; see what it can do in a free demo.




