Cloud RADIUS Built for ABAC
With the advancement of technology, hackers have constantly upgraded their modes of attack and have penetrated almost every industry you can think of. Here’s a recent cyberattack reported by the Department of the Treasury’s Office of Foreign Assets Control (OFAC), sanctioning several individuals and entities involved in the malicious act.
It is pretty apparent that to counter these advanced cyberattacks, you must upgrade your network security infrastructure, and in doing so, you must evaluate the existing access privileges your organization practice on a routine basis. In this article, we will try to learn about the latest access management techniques and help you evaluate the one best for your organization.
What is ABAC(Attribute-Based Access Control)?
ABAC (Attribute-Based Access Control) is a modern access control technique in which attributes or characteristics are taken into account. In ABAC, access is granted not based on roles but on various primary attributes such as email-id, departments, locations, policies, etc. It is a smooth upgrade from the traditional Role-Based Access Control (RBAC), which was solely based on user roles within an organization.
Many organizations have used traditional access control policies like RBAC in the past to customize the access of resources to designated users based on their assigned roles, but ABAC has empowered these organizations to practice more granular control over their resources. They can now easily control network access without compromising security by using the advanced attributes that RBAC struggled to provide.
ABAC has been a vital cog in achieving Zero Trust Network Architecture (ZTNA) within an organization by defining a model for network access based on attributes and policies. Obviously, it primarily aims to eliminate unauthorized users and other suspects from the systems by using attributes that are hard to guess and penetrate.
How does ABAC work?
To understand how ABAC works, we first need to understand the historical context of RBAC and its evolution to ABAC over the years. Also, we need to have a clear understanding of various components that comprise ABAC and their correlation.
The Transition from RBAC (Role Based Access Control)
RBAC is the traditional mechanism in which separate users/devices are granted unique access levels, according to predefined roles, to effectively implement the organization’s security policies. A user’s “defined role” is given maximum priority over any other attributes in role-based access control.
ABAC, on the other hand, extended the scope of RBAC by adding various attributes to the existing roles that added extra layers of security to the enterprise. It further enhanced an organization’s data security by providing granular control over network resources with attribute values that otherwise were impossible to use within RBAC.
Let’s try to understand this with an example. In RBAC, an organization can provide access to employees based solely on their roles, such as a marketing employee being given access to a different set of resources from a sales employee.
While it’s true that a marketing employee may need access to different resources from a sales employee, granting the same blanket level of access to roles can lead to issues. For instance, if your marketing employees are located in different time zones, and you’ve stipulated that they can only access certain resources within a specific range based on one time zone, it may not apply well to your whole marketing department.
Also, if employees from different departments sometimes need access to the same resources, RBAC fails to cater to these needs as the only criteria it takes into account is “Role.”
But in ABAC, not only the designation of the employee but other characteristics such as location, time zones, designation, and many other simpler attributes are taken into consideration for providing access to resources. Here the limitations of RBAC are eliminated by using these attributes and enhancing the organization’s overall security.
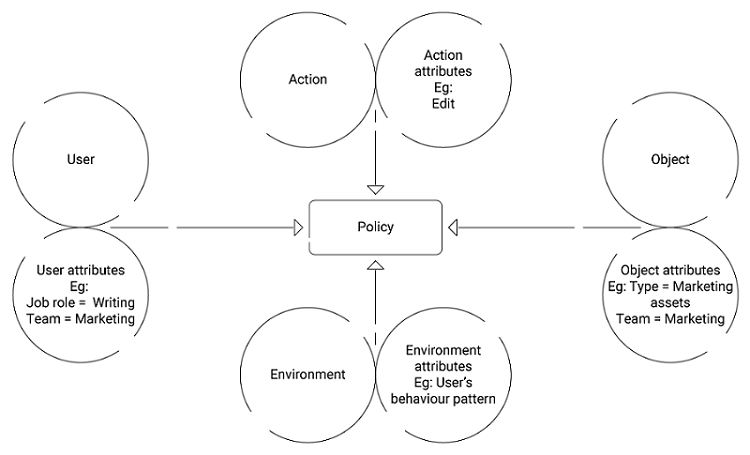
Components of ABAC
- Subject
- Object
- Action
- Environment
Subject:
The subject is the user or individual who demands access to the resource attributes within an enterprise. The attributes used to describe the subject or user include roles, locations, membership, designation, security ID, and so on.
Object:
An object is a resource or asset that the subject/user wants to access within an enterprise. For example, Object attributes could be access to a particular application like Grammarly for the employees belonging to the Content Marketing Team. While the other Marketing Team Members not belonging to Content niches might not need its access.
Action:
Action is what the subject or user performs with the object/resource. The common “Action” attributes include reading, writing, editing, deleting, viewing, and so on. Sometimes more than one attributes combine to form a single Action.
Environment:
The context of the access requests in the broader spectrum is defined as the Environment. The common attributes include the location and status of the devices, IP addresses, time zones, and so on. The Environmental attributes also consider various risk signals associated with the organization, such as the authentication strength and protocols followed by the organization.
Advantages of ABAC
As opposed to RBAC, which relies on a static method that eventually seems redundant, ABAC is more of a dynamic authorization model that employs various contextual criteria for access requests. For example, ABAC can define the policies based on multiple attributes and provide access based on these policies that might include users with different roles.
ABAC uses a more targeted approach to grant access to users/devices compared to RBAC, as the attributes it takes into account are more fundamental in nature. For example, as we discussed earlier, there might be a possibility that the same resource might be useful for employees of different roles within a business unit, and RBAC might struggle to perform efficient access control in this case.
ABAC models are more adaptable in nature and user-friendly when it comes to using them for new users/devices. As in this case, you only need to create new policies allowing the new subjects to access the resources rather than modifying the object’s attributes or existing rules.
Last but not least, the most promising advantage that you might have guessed would be the superior security ABAC offers compared to RBAC. Due to its fine granular use of multi-dimensional attributes, ABAC provides an extra layer of security to the traditional access control and helps admin strengthen their network parameters.
Disadvantages of ABAC
One might argue that the advantages of ABAC far outweigh the disadvantages, and it’s true also, but not every organization really needs to implement it. You must evaluate the use cases and the requirements of your organization before making a switch to ABAC, as the complexities involved in the implementation can be tiresome.
Also, for organizations that do not deal with as much sensitive data and information, like small businesses with pre-defined roles for their employees, it is better to practice RBAC as compared to ABAC. Additionally, organizations not dealing with external vendors and third parties should prioritize RBAC over any other methods.
The biggest challenge that ABAC presents is its implementation and scalability, as it involves hundreds of attributes that make the final policies. The entire process can be time as well as resource-consuming if not performed by experts.
This poses a new challenge of identifying the network experts who are good at performing ABAC-based authentication and authorization while keeping your time and monetary investments as low as possible. We hope your search for reliable ABAC vendors ends here as we at SecureW2 exactly perform the same task of simplifying Attribute-Based Control Access.
How to Use ABAC Efficiently?
We at SecureW2 have been performing Attribute-based Access Control (ABAC) for such a prolonged duration now that it is hard to find an industry where we don’t have satisfied customers.
We have developed a lot of industry-defining products like JoinNow PKI and Cloud RADIUS to safeguard the interest of our customers belonging to vast horizons. These products have not only enhanced network security but have redefined the parameters of a safe and secure cyber environment.
SecureW2’s Managed PKI helps you generate certificate templates (for many different use cases), so misconfiguration isn’t a problem. Our GUI interface makes managing certificate templates incredibly easy because it allows admins to edit or delete any templates quickly. Also, our Cloud RADIUS can use these certificate attributes to perform Identity Lookup and apply the most up-to-date policies during authentication.
One of the most significant factors that contributed to such enormous success is that we have defined and practiced multiple customizable policies that take into account innumerable attributes for their implementation. We have policies defined for each step, from authentication and enrollment to the lookup, that has vastly contributed to improving access control rules.
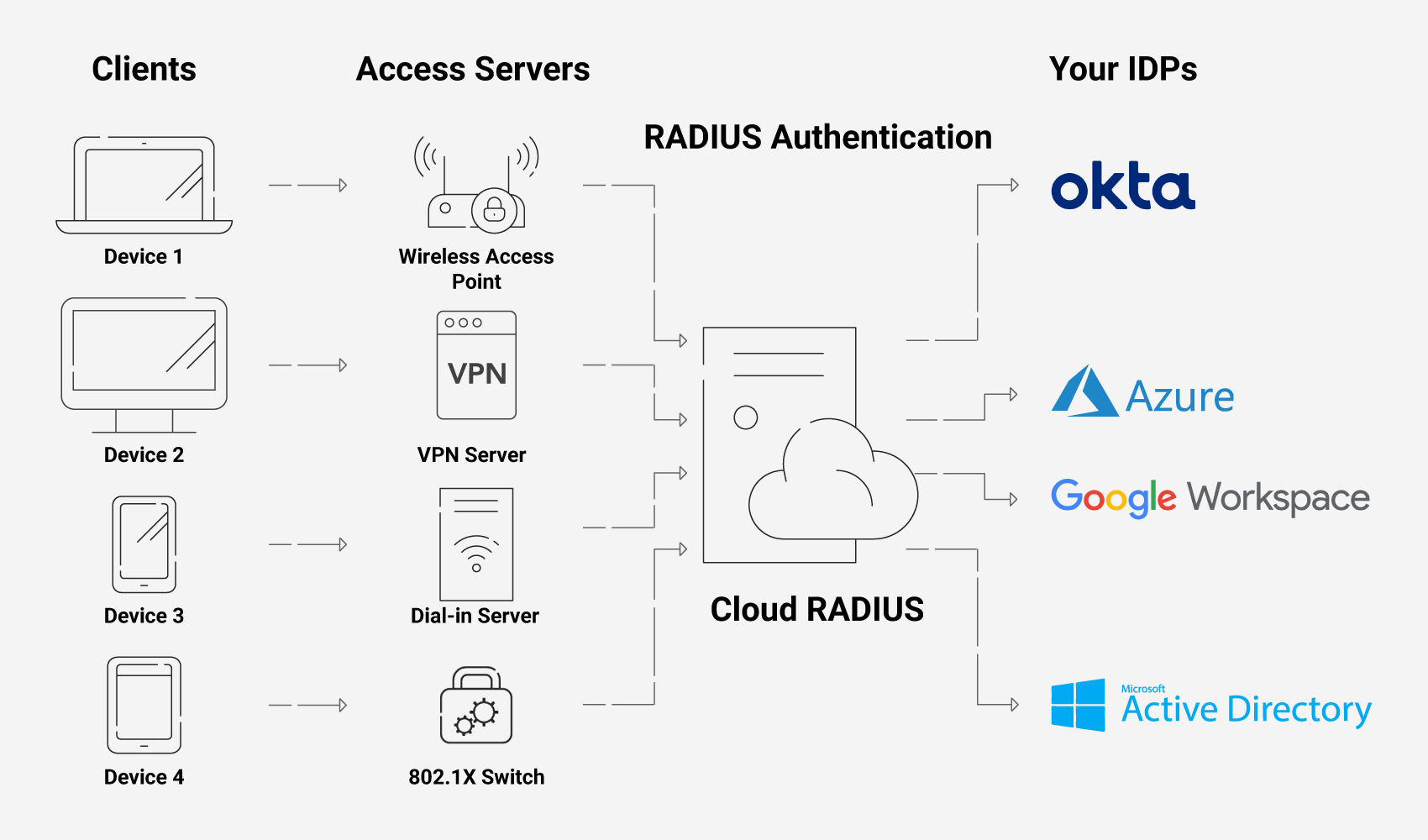
Our policies allow Admins to configure several security policies and set up a Cloud RADIUS server that dynamically authorizes users and devices into custom security groups. An ideal RADIUS deployment plan involves connecting with your identity provider to look up a user/device during the RADIUS authentication process. The RADIUS server then dynamically assigns the user to the appropriate security group based on your custom settings.
Simplify ABAC with SecureW2’s Solutions
Attributes are the building blocks of the policies, and diverse policies play a significant role in enhancing the “access control” within an enterprise. With its multidimensional attributes, ABAC has strengthened the traditional access control models, especially for organizations that can not afford to compromise on their security and are more vulnerable owing to their size and exposure.
Our Cloud RADIUS practice advanced policy-based access control using diverse attributes that can be easily customized to suit the needs of any organization. It also has built-in redundancy to provide easier integration into cloud applications such as Azure/Okta/Google that can securely authenticate remote users. We also have an experienced support team that is always available to assist you in configuring a RADIUS server in a matter of minutes, and believe us, they have excellent expertise in what they do.
You can book a call with us or check out our pricing page to see if SecureW2’s Cloud RADIUS solutions fit the authentication needs of your organization.