
How to Implement PAM With Cloud RADIUS
Improve the identity context of the devices in your network with SecureW2s pioneer solutions. Read to know more!
Read StoryRADIUS security news and updates from the Cloud RADIUS team.

Improve the identity context of the devices in your network with SecureW2s pioneer solutions. Read to know more!
Read Story
With the advancement of technology, hackers have constantly upgraded their modes of attack and have penetrated almost every industry you can think of. Here’s a recent cyberattack reported by the Department of the Treasury’s Office of Foreign Assets Control (OFAC), sanctioning several individuals and entities involved in the malicious act. It is pretty apparent that […]
Read Story
The importance of authentication security cannot be understated. Effectively controlling who has network access is key to operating a secure network. As a result, control over the authentication process is a primary goal for nearly all organizations.
Read Story
Looking to choose a Cloud RADIUS for IAM? Take a look at what are the key factors that goes into making a robust cloud RADIUS as an IAM solution.
Read Story
Here's how Cloud RADIUS improves the RADIUS protocol, securing Wi-Fi from outside threats.
Read Story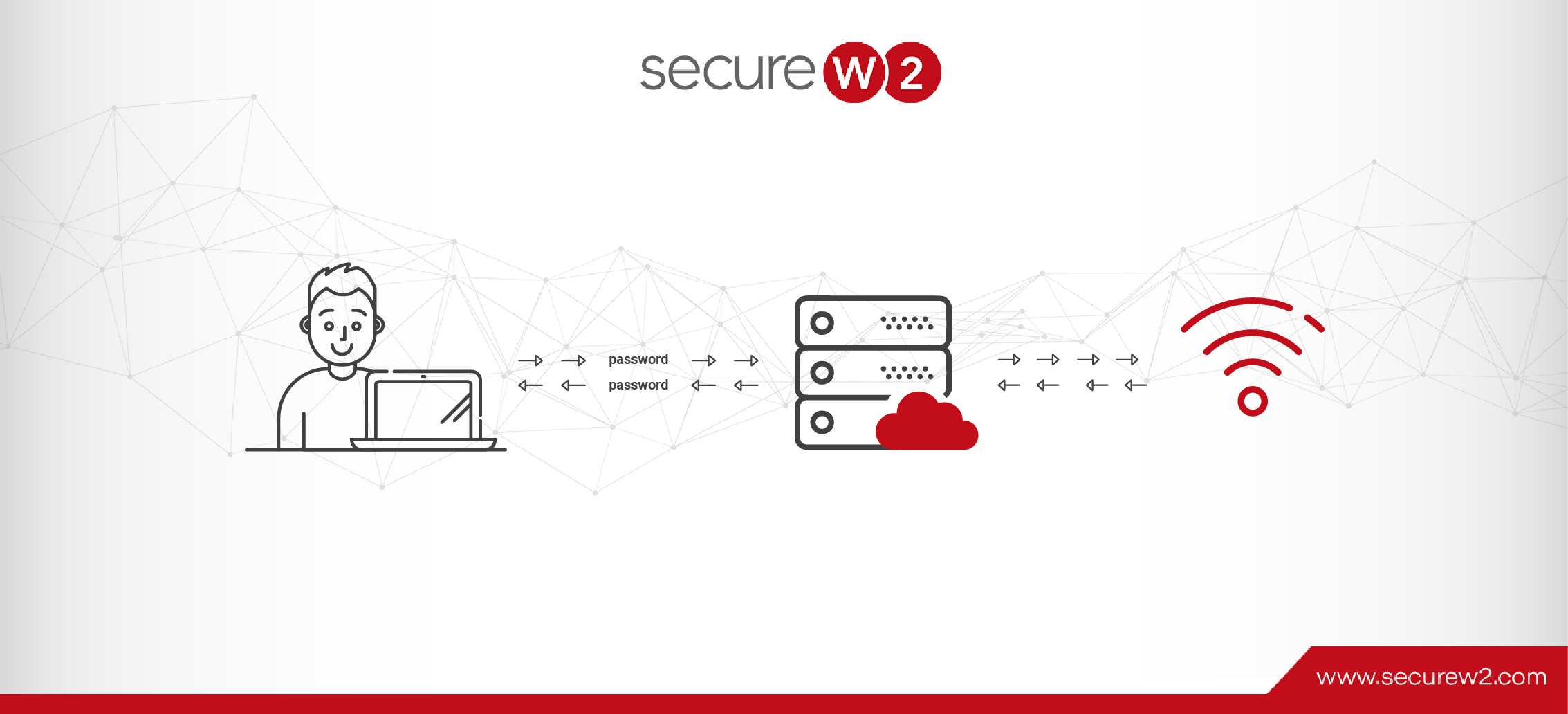
Want to know how passwordless authentication protocol (EAP-TLS) in cloud RADIUS servers provide a better user experience and improved cryptography?
Read Story
Cloud RADIUS is the best solution to walk the fine line of balancing User experience and Security. Here are some tricks you probably didn't know about.
Read Story
Mitigate your network risks with Cloud RADIUS Adaptive Authentication. Continue Reading to Know More.
Read Story
Forrester, an analyst firm’s report, suggests 80% of data breaches occur due to weak credentials. There were simpler days when data on a network was believed to be safe, but it is not so in the present. The stakes are higher now with more and more threat factors and Layer 2 attacks. Organizations are constantly […]
Read Story
What Is Cloud 802.1x? An 802.1x network is unique in one major way; it uses a Cloud RADIUS server as a means of authenticating users. The Cloud RADIUS checks a user’s credentials to see if they are an active member of an enterprise and grants users varying privileges of access depending on the network policies […]
Read Story