
The Best RADIUS For IAM On Your Network
IAM, short for Identity and Access Management, is a broad concept that covers an array of tools, strategies, and DevOps practices that enable systems administrators to identify, track, and monitor digital users in their networks. Sound a bit too complicated? Let’s first try to understand what IAM is and how it works for us.
Identity and Access Management Breakdown
Let’s take the example of Azure AD, Okta, and Google. We know that they are cloud-based directories that work as Identity Providers (IDPs), storing our organization’s identities, including their roles and permissions, for access management. We rely on these directories to verify a user trying to access our network is indeed active in our organization.
Now let’s look at another example, managed Cloud-based RADIUS servers. A RADIUS server first checks the credentials of the user or machine trying to access the network, then validates if they are still active by checking them through a revocation list and then with an Identity Provider (IDP) like Azure, Okta or Google and finally decides if access can be provided to the user, the level of access depending on the role defined and doing a final check to verify the user is not on the revocation list.
What IAM does is automate and log the process of identifying, authenticating, and authorizing users with digital identities like login passwords. The goal of IAM is better insight into your network activity and the tools to manage users and devices and their various permissions. With the right IAM solution, network administrators can monitor, manage, address, and report any network activity making the network more secure and visible.
One might think that it would be easier to manage your own RADIUS servers since you already have an IT department in place that is already handling access management. That might be a bit more challenging than it may seem.
Cyber attacks are getting more brutal, and to secure your network, you need an identity access management solution that is impenetrable. A server that can detect and prevent any form of security threat to your network. Building such an infrastructure needs a lot of careful planning, an in-depth understanding of the process flow, and running multiple proofs of concepts before implementing it. This involves a lot of time and expenses.
Let’s first look at how a self-hosted RADIUS, as an IAM solution, comes with both pros and cons that vary depending on the implementation of the solution. We will also take a look at the advantages of a managed RADIUS in alleviating your network security.
Self-Hosted RADIUS Explained
Self-Hosted RADIUS or a DIY RADIUS refers to the RADIUS solutions that are installed and managed by the organization or a user on their own, so the responsibilities of maintenance and problem-solving lie on the organization. In the self-hosted environment, the entire infrastructure is developed from the ground up, starting from making decisions like which combination of IAM solutions and what protocols to be implemented to designing the entire environment as well as maintenance of the server.
Also, self-hosted RADIUS is traditionally on-prem which means there has to be a server set up for every location if your organization is spread across multiple locations. Developing and maintaining a self-hosted RADIUS, which can be an effective solution for network security, requires the following key components in terms of skills.
- Sound knowledge of IAM solutions and their protocols.
- Technical expertise to design and implement the solutions.
- Technical expertise to manage and maintain the RADIUS server.
- Physical Infrastructures like hardware for every location for on-prem RADIUS.
- Recurring training on advanced and up-to-date technology to develop an IT team.
- Physical Security to monitor the on-prem servers.
All the above-mentioned requirements would be needed for each location which makes the process of setting up self-hosted RADIUS servers expensive and time-consuming. Let’s take a look at the pros and cons of self-hosted RADIUS to understand the concept better.
Pros of Self-Hosted RADIUS
A Centralized Authentication & Access Management Solution
With hybrid and remote work adding to the number of BYOD devices that connect to your network, it becomes even more crucial to keep an eye on who is accessing your network and when. RADIUS manages all these devices logging in to your network from multiple locations through one centralized authentication server. A well-designed RADIUS server is the foundation of a very effective IAM solution that allows network administrators to manage their network access and security dynamically.
Improved Network Security
RADIUS supports multiple authentication protocols. In an enterprise environment, authentication done using certificates can make your network more secure. Unlike passwords, certificates cannot be stolen or transferred, so they are better for security. Also, the pains of password management, like account lockout and setting a new password, are practices that are time-consuming and frustrating.
RADIUS servers are also useful in applying network policies and role-based access management. When set up the right way, RADIUS servers help you manage your network security with greater efficiency.
The Cons of Self-Hosted RADIUS
Traditionally implemented on-prem
The initial setup for a self-hosted RADIUS server can be difficult for IT admins to implement and integrate into an existing IT landscape, especially if the organization already supports on-premise, legacy services like Active Directory.
Self-hosted RADIUS is traditionally implemented on-prem, so it involves developing the physical infrastructure that is expensive and difficult to scale since every location would require on-prem infrastructure. This needs both hardware and skilled manpower resources (that may need extensive training to understand the design of the self-hosted RADIUS) for every location.
Also, on-prem solutions are susceptible to physical threats like stealing and damage caused by either man-made or natural disasters. They, therefore, require physical security to protect the infrastructure and need experts to be present on-site for the maintenance of these servers. Disaster management with on-prem servers is not a tedious process that can be time-consuming, too, since these servers depend heavily on physical infrastructure and skilled manpower onsite.
Arguably the most important drawback of on-prem servers is that they are not compatible with cloud servers. With almost everything moving to the cloud, the inability to integrate well with the cloud services makes on-prem servers almost redundant.
Security vulnerabilities, if not implemented correctly
Like any other technology, RADIUS can introduce new threats to your organization if it’s implemented incorrectly. Misconfiguration is an easy way to create vulnerabilities that hackers look for.
By definition, a self-hosted RADIUS is one that you will DIY. Some RADIUS vendors deliver you the tools to unpack and build out into your own authentication server. Some, often marketed as RADIUS-as-a-Service, set you up with an online portal to which you can tie all of your infrastructures. Ultimately, all of these options leave the burden of building and managing a RADIUS on you.
But not every organization is a cybersecurity company, and not every IT team has cryptography experts. That’s why it makes sense to choose a Managed Cloud RADIUS like the one offered by SecureW2.
Advantages of Managed Cloud RADIUS as an IAM solution
Cloud RADIUS helps you safeguard your network by providing you with automated identity management and network access control to help you get better control over your network. Let’s look at how a managed cloud RADIUS server can be the best solution for business continuity and disaster management, as well as network security, to help you become more compliant with your regulatory boards.
1. Passwordless Authentication
Authenticating a user with a password can never be considered 100% accurate because they can be easily stolen both physically and through cyber attacks. Certificates, on the other hand, cannot be stolen, replicated, or transferred, making them a better context for identity management. The user experience with passwords is not considered the best because of password management-related issues like the need to reset passwords periodically, remembering the different passwords, and accounts getting locked out because of using the wrong password multiple times.
With certificates, the process of authentication is automatic, with no need for any interaction between the user and the server, nor is there any need to remember or store any authentication credentials, thus making for a better user experience. IT department’s workload related to password management gets almost eliminated because certificates, once issued, are valid for years and so do not require any work for maintenance. With the right PKI solution, the entire lifecycle of certificates can be managed with minimal to no effort.
Safe VPN & WiFi Authentication with 802.1X certificates can do away with the vulnerabilities of password management, and your network vulnerabilities are better mitigated.
2. Scalability & Flexibility
Cloud-managed RADIUS solutions are more economical than on-prem solutions, primarily because the hardware setup and maintenance are expensive. They take a lot of time to build and are more vulnerable to theft and damage. For any issues with an on-prem, an expert has to be physically present or go to the location, making it very time-consuming too. You can instantly scale your network up or down to meet the needs of your organization using the redundancy of the cloud.
3. Technical Expertise & Proof of Concept
Setting up a network security solution that has the best possible cryptography needs technical expertise, time in testing multiple proofs of concepts, and an exhaustive amount of planning. With a managed server, you get the added benefit of technical expertise from inception to implementation. The solutions provided by a reputed network security company are well constructed, and their customers are a great proof of concept.
Most importantly, you have access to a team of dedicated RADIUS support specialists 24/7. Unlike your in-house team, these people are already experienced with managing and troubleshooting RADIUS.
4. Implement Zero-Trust Network Policy with Role-Based Access Management
Zero trust as a security philosophy at its core follows the principle, “never trust, always verify.” It is not enough to just authenticate a user or a machine before allowing them access to the network because you go by the assumption that all users that are authenticated are to be trusted with the information within your network. This assumption may be dangerous as it does not take into account factors like someone might be infiltrating your network or one of your employees might abuse the information that is within your network.
With zero trust, network security doesn’t stop at authentication. When a zero trust policy is implemented, both users and devices are monitored constantly, and the access level of every user and machine is defined well to limit access to only the resources and applications that are necessary to perform their defined roles. This is usually referred to as network segmentation, which involves segregating network users into different groups with identical access levels to the network and assigning these groups to specific virtual LAN networks (VLAN) through RADIUS. Also, zero trust requires verification for every access request by any user or machine trying to access the network. A managed cloud RADIUS like SecureW2 can help enforce network policies more effectively by native integration with cloud identity providers like Azure AD, Okta, and Google.
A cloud-managed RADIUS (that authenticates using certificates) can be a great role-based access control solution. Assigning security groups on the basis of roles can help limit access to only specific data or information in the network. This is great in implementing a zero trust network policy as the users will be able to access only the information that they need to perform in their roles.
5. Faster Deployment
Managed cloud service providers ensure faster deployment since they already have an established deployment process with proof of concepts. Post-deployment regular performance analysis is done by the network operations center (NOC) to identify and fix any problems to ensure the client has a fully optimized environment.
6. Secure SSO Platform with certificates
Single sign-on (SSO) platforms are one of the most critical gateways to your network. Using passwords to authenticate for these platforms can leave your whole network and security risk because passwords can be easily compromised. With the recent attacks on uber, it has become very clear that multi-factor authentication (MFA) alone is not sufficiently secure.
Using 802.1X certificates as your login credential is the safest way to protect using SSO. Digital certificates also allow you to extend your SSO to more applications and services, as well as create more secure connections for the federated identities being shared.
7. Device-Based Access Control with Certificates
One major security risk that sometimes gets ignored is that of personal devices like mobile phones or tablets. With credentials, anyone can log in to the company network from their personal devices. These devices may carry malware or viruses that can then spread to the network and comprise network security.
With certificate authentication, only the device equipped with a certificate can connect to the network. Personal devices or BYOD can be issued certificates with access levels pre-configured. The best part is that certificates can’t be removed or stolen from a device, so you’ll always know exactly which device is accessing the network.
Device-based access control can help improve network visibility as well as e useful in managing conditional access policies.
8. Eliminates Network Downtime
With a managed cloud RADIUS, you do not have to worry about network downtime. There are multiple redundant servers provided as backup to ensure you never lose productive hours due to unplanned outages. The backup servers also come in handy when there is a need to divert traffic for segmentation or as a buffer against DDOS attacks. Don’t allow your entire business to grind to a halt because of a lack of network access.
Additional RADIUS Features with SecureW2
Along with the above advantages, SecureW2 solutions come with some additional benefits that are unique in the market. Here are some of the features that make our solutions cutting-edge in the industry.
Native Integration to cloud identity providers like Google, Azure, and Okta
SecureW2 cloud RADIUS server comes with native integration with cloud identity providers (IDPs). Our RADIUS can natively communicate with cloud IDPs like Azure, Google, or Okta to look up the identity of the user and the machine at the time of authentication. That makes us the only RADIUS server that can do a lookup from IDP directly for the most up-to-date user info and permissions.
Complementary PKI Solution
A Public Key Infrastructure (PKI) is the building block of a trusted certificate. Our RADIUS solutions have an optional inbuilt PKI that can manage the entire lifecycle of certificates from issuance of certificates, monitoring network access activity, and creating custom certificate templates, to renewal and (or) revocation. You can create your own Certificate Authority (CA) or easily integrate with other CAs like Google Workspace.
SecureW2 Cloud RADIUS
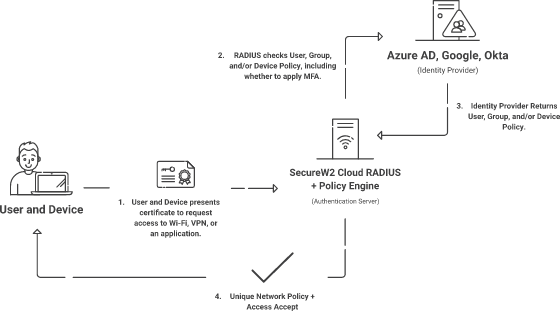
RADIUS servers are undoubtedly one of the most effective IAM solutions that can help alleviate your network security. However, the efficiency of this solution is determined by the way the solution is designed. At SecureW2, our industry’s best team of experts has designed solutions that use digital certificates to verify a user or a machine eliminating the risk of unauthorized access to your network through credential theft.
Our cloud RADIUS servers are natively integrated with Azure AD, Okta, and Google environments for more effective and efficient policy enforcement and role-based access management, thus creating an ideal environment for the effective implementation of zero trust network policy. Connect with our experts to know more about our solutions.




