Adaptive Authentication With Cloud RADIUS
Risks in any business are given, and how they are managed can make or break your business. The success of a company depends on how adaptive it is in mitigating risk factors. The biggest threat modern businesses face is the threat of data breaches or cyber-attacks. Information is the biggest asset for any industry and has always been the target of attacks.
As businesses transition to the cloud environment, managing network security becomes more complex. Anyone can connect to a network using any device, from IoT to BYOD. With users logging in remotely, it is even more difficult to confirm their identity with absolute certainty because it could be anyone behind the device trying to connect.
Add to that the ever-evolving cyber-attacks that are getting more brutal. The traditional security system of password-based authentication is no longer enough to keep your network secure.
There is a need for an intelligent solution that can not only authenticate a user but also determine their identity with absolute certainty. It should also determine what level of access they can be provided with after analyzing the corporate risks. In order to do that, it has to be able to complete 2FA (two-factor authentication) or MFA (multi-factor authentication), depending upon the risk each access request carries.
Adaptive authentication, a form of multi-factor authentication, has gained popularity. Adaptive or context-based authentication is increasingly integrated with identity and access management platforms for better access management.
What Is Adaptive Authentication?
Adaptive authentication considers the security risks and user behavior to determine the right type of authentication for every access request. It uses 2FA and MFA, depending upon the scenario and the risks involved, to ensure the right authentication method is deployed for every authentication request.
For example, a financial specialist logging in using a VPN to their office desktop (a managed device) will have access to the sensitive information they need to perform their role and have a certain authentication protocol.
However, when they log in from their mobile phone, from a different country and time zone, they might be asked to go through an additional authentication step such as OPT. They will have limited or blocked access to specific applications or information, such as their email account, but may not be able to access the files with company financial information.
Risk-based authentication, context-aware authentication, and attribute-based access control are often used interchangeably with adaptive authentication. They all mean the same thing, and the architecture is based on the zero-trust network architecture that says that authentication alone is not enough. To minimize security risks, it is important to continually monitor user activity and behavior to create a better identity context that, with the help of machine learning, can be used to determine the most appropriate authentication method.
How Adaptive Authentication Works
Adaptive authentication, with the help of artificial intelligence, learns behavior patterns to ascertain the risks involved in every access request. It uses behavioral learning to capture and identify user behavior and geo-velocity to create user profiles with more accurate identity context.
For any deviation from normal behavior, adaptive authentication will ask for an additional set of authentication as per the defined company policies. The way it does this can roughly be divided into the following categories:
Behavioral Learning-Based Authentication
Adaptive authentication monitors user behavior and history to learn behavior patterns and user risks involved continually. This can be further divided by:
- User Behavior: Includes the time they log in, the typing speed, websites, and applications accessed. This information is derived from studying the user interaction with the device. For any deviation from normal behavior, adaptive authentication will ask for an additional set of authentication.
- Geo-Velocity: Is determined by analyzing the information related to which location(s) the user logs in from typically versus which location they are currently asking for access from. The different modes of transportation and time taken to travel are considered in calculating this. For example, a user logging in from Seattle asking for access from India after a short period of time will be considered suspicious behavior. They will be asked to complete additional authentication steps, or the session might be terminated depending on how risky and implausible the request seems.
Device-Based Authentication
In device authentication, the security level of authentication is determined based on the device from which the request is made. Device-based authentication is further divided by:
- Device Recognition: There is an additional security level introduced in case the device profile used for requesting access is different from the profile history. If the device is recognized as stolen, the system terminates the access request. For example, a user requesting access from a new device will be asked to complete an additional authentication step.
- Device Context: Uses operation system configuration such as security levels and OS version. Depending on the company policies and risk level, decisions are made about the authentication method needed and the degree of access.
Granular Admin Policies or Role-Based Access Control
Adaptive authentication platforms allow defining risk levels based on factors like the defined role of the user, the location from where the request is made, the time of the request, and more. These are done by defining attributes as per company policies. Users with the same attributes are usually categorized under the same groups. They have the same authentication steps and access level defined per identified security risks.
Risk-Based Authentication
In risk-based authentication, access is granted after calculating the risk score of each access. The risk-calculating algorithm determines the risk score after considering factors such as the sensitivity of the resources requested and device statuses such as its configuration, firewall status, anti-virus software in the system, geolocation, and IP addresses.
Adaptive Authentication With Cloud RADIUS
Cloud RADIUS is a RADIUS server hosted on the cloud. It is natively integrated into cloud identities like Azure, Okta, and Google for real-time look-up at the time of authentication.
It can provide seamless authentication for your enterprise network through Wi-Fi, wired, and VPN connections, to name a few.
Just like an on-prem RADIUS server, Cloud RADIUS works as the gatekeeper but in the cloud, making it one centralized network access control platform for any user or machine logging in from anywhere.
It can perform both user-based and device-based authentication by real-time lookup of policies and identities in your cloud identities. These features help you to implement adaptive authentication with greater effectiveness.
The most important feature of Cloud RADIUS, however, is passwordless authentication. It uses certificates for authentication that are better for identity context. Identity context is at the crux of adaptive authentication, and certificates provide some unique information to the RADIUS at the time of look-up that helps verify the identity of the certificate holder with greater certainty.
Let’s look at how Cloud RADIUS helps implement adaptive authentication with the help of certificates.
Implementing Adaptive Authentication With X.509 Certificates
With the help of machine learning and artificial intelligence, adaptive authentication learns user behavior to build a user login pattern profile. These attributes are used along with company policies to determine the risk level of each request.
One of the most effective methods of implementing adaptive authentication is using X.509 certificates. Certificates are considered better for context-based authentication because, unlike in password-based authentication, there is no human interaction needed at the time of authentication, which happens automatically within seconds. It has a far better user experience because the user no longer has to remember complicated passwords.
What Is an X.509 Certificate?
X.509 is a cryptography standard for public key infrastructure (PKI) that defines public key certificates. Each certificate carries unique identifiers like a user name or machine number, signature algorithm, and certificate issuer details that help verify a user or a machine with greater certainty. A certificate also includes policy information, such as security permissions, that govern the access level of the certificate holder.
Admins can create X.509 certificates through certificate authorities (CA) using certificate templates where they can assign and configure attributes as per user behavior and company policies around risk levels. These defined attributes ensure every user or machine has the right degree of access and follows the most appropriate authentication steps.
Benefits of Digital Certificates for Adaptive Authentication
The two key factors that make certificates great instruments for implementing adaptive authentication are PKI and certificate templates. A well-designed PKI ensures that certificates cannot be stolen or replicated, and certificate templates help with the better implementation of policies while storing vital information about the certificate holder’s identity. Let’s take a look at how they add value in implementing adaptive authentication.
PKI Makes Certificates More Secure
Public Key Infrastructure (PKI) manages the public keys used in public-private key encryption for identity management and the entire certificate lifecycle management process from certificate distribution and revocation to renewal. PKI certificates can be configured to authenticate for Wi-Fi, VPN, email, web apps, and more.
How it works is that the client first generates a public-private key pair. This public key, along with the unique information about the client, is then sent to the Certificate Authorities (CAs). The CA issues a PKI certificate that verifies that the certificate holder is the owner of the public key and includes the attributes that uniquely identify the certificate holder.
The CA, as the trusted authority, signs the certificate with its private key and distributes it to the user or the machine.
The private key of the public-private key combination is almost impossible to crack as at no point does it get transmitted over the air. Also, the unique number generated at the time of the handshake is a huge number generated from a complex combination of algorithms that are almost impossible to crack.
Traditionally, PKI was hosted on on-prem servers, making them expensive and difficult to manage and scale. With Cloud RADIUS, SecureW2 also offers turnkey PKI solutions that are the industry’s best PKI solutions. It’s very easy to configure and is completely in the cloud environment.
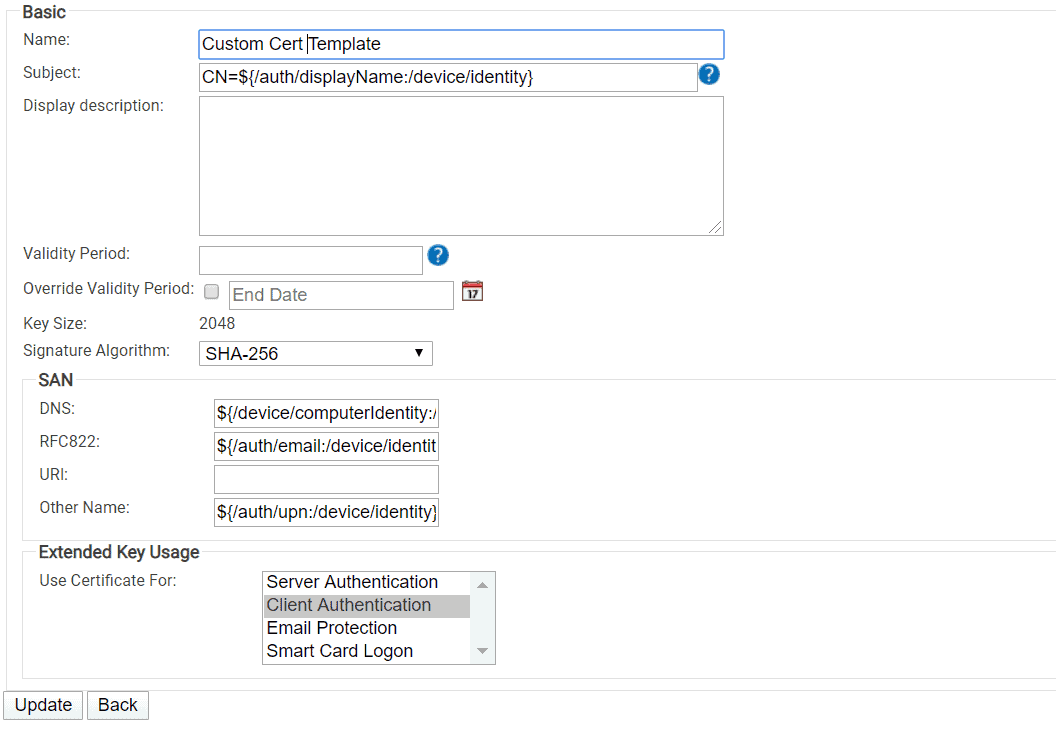
Configure Identity Context and Organization Policies With Certificate Templates
A certificate template allows you to define attributes for each certificate holder that can be instrumental in effectively implementing company policies. Certificate templates are also a great way to define identity context with greater precision that, in turn, boosts the precision of adaptive authentication.
The control to define what attributes a certificate carries gives you a greater degree of control over your network. You can do this by customizing certificate templates. Creating certificate templates in SecureW2 can be completed in a few simple steps from the GUI interface.
Many organizations are moving from AD CS to SecureW2 because it completely eliminates the additional step of duplicating templates that AD CS requires. It allows easy editing, deletion, and creation of new template options from the management portal within a few minutes.
SecureW2 Solutions for Adaptive Authentication
Network security environments are getting more complex with all types of IoT and BYOD devices connecting to your network from multiple remote locations. This substantially increases business risks that identity-based authentication alone cannot mitigate. To verify with absolute certainty that the person requesting access at the other end is really who they say they are, there is a need for an intelligent system that can decide the authentication method to best mitigate the risks.
Cloud RADIUS comes with a host of features that can improve your adaptive authentication game to a great degree. Certificate-based authentication with Cloud RADIUS is completely automated and can be set up within minutes. It is designed to integrate natively with cloud identities and can be deployed with your existing infrastructure to leverage Wi-Fi, VPN, and firewall infrastructure.
SecureW2 solutions help you implement role-based access control with a greater degree of efficiency thanks to adaptive authentication. Along with industry-leading technologies, SecureW2 has a great support team who are always available to provide you with all the help you need. Click here to learn more about pricing.