What Is 802.1X Port Security?
Securing your network is helpful for both keeping your information secure and building a good reputation in the market. After all, information is the most crucial asset of any business.
In a business environment, who has access to your network and how much visibility you have over the users and machines in your network, to a great degree, determines the quality of your network security.
Modern Identity Access Management (IAM) solutions help you protect your network by giving you better control over all connections in your network. However, what sometimes get ignored are the ports in your network. If not secured, they could be the gateways through which hackers infiltrate and maybe even take control of your network.
This article will explain what port security is and how 802.1X port security can help you improve your network access control. First, let’s take a look at what a port is and what the different types of ports are that an enterprise network has.
What Is a Port?
A port is a designated space in a network that allows specific kinds of communication to take place. Ports can be both physical and virtual. Every network will have thousands of ports for different functions.
Each port is assigned to perform a specific task, and they are the medium through which computers can distinguish between different types of traffic. For example, there will be different ports for email, web pages, or applications despite their connecting through the same internet connection.
What Are the Different Usages of Ports?
In computing, there are three main categories of ports:
- In networking, a port is a set of unique numbers (pre-defined) assigned for a specific communication. This port is on your device, and each port allows communication by receiving and transmitting packets for a specific service. One example is a port for email communication.
- In computer hardware, a port is a socket or a jack that you plug your hardware into to establish a connection for a specific task. Examples include a USB port or Ethernet port, mostly Layer 2.
- In computer software, a port is assigned by converting a particular software to operate on a hardware or operating system (OS) different from what it was initially developed for.
What Is Port Security?
Port security is the feature that allows you to restrict access through the port by placing some regulations to control or limit the MAC addresses that can get access through a particular port. Port security can help reduce the risk of unauthorized access to your Layer 2.
A media access control address (MAC address) is what a port uses to recognize a device. Enabling port security allows you to set restrictions on the number of MAC addresses a port communicates with, as well as to define penalties for each port in the case of violating these restrictions or allowing access to unauthorized MAC addresses.
The two ways to enable port security through a switch are:
- Defining the number of MAC addresses for each port so that if it exceeds the defined limit, the port will raise the alarm. This can help identify any unauthorized MAC address trying to connect using a particular port.
- Define settings to terminate any unauthorized access identified, as well as record the log of each access to observe the behavior for any suspicious activity.
Using MAC addresses to identify devices for allowing access, however, is not the most secure way because MAC addresses can be easily manipulated. Attackers can steal a valid MAC address, use it to gain entry through a port, and carry out cyberattacks by spoofing MAC addresses.
MAC address spoofing is a fairly common attack that may impact your network, leaving it compromised. In this attack, an attacker will try to access the network by stealing a valid MAC address authorized to access the network. Once they gain access, attackers can carry out multiple Layer 2 attacks on your network, such as MAC Spoofing, switch spoofing, an STP attack, and double tagging.

How Port Security Impacts the Overall Security of Your Organization
In network security, port security is a basic or foundational concept. Ports are the gateways through which your users access the information in your network, and keeping them secure is one of the most important aspects of network security.
An open port is like a direct invitation to hackers, as you cannot control who can access your network. In that case, it can leave you vulnerable to Layer 2 attacks, such as different types of spoofing and man-in-the-middle (MITM) attacks that can compromise your network and may even leave it crippled if they manage to move to other Layers.
Port security helps you in network segmentation and in defining role-based network access control for your organization. Port security will allow you to define who can access what information. We’ll take a closer look at how port security can help streamline network access control.
As explained in the previous section, port security using just a MAC address is also not enough. Implementing 802.1X port security is a better way to ensure optimal security of the ports in your network. Let’s dive into what 802.1X port security is and how it can help enhance cybersecurity.
802.1X Port Security
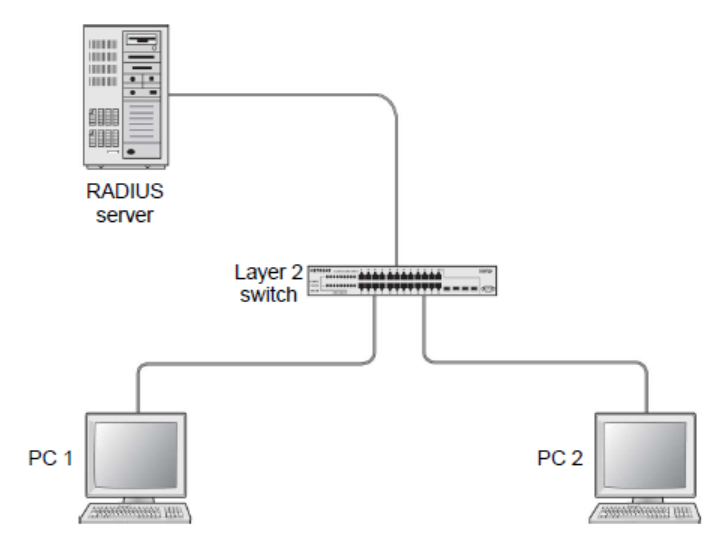
802.1X port security is an IEEE standard for Port-Based Network Access Control (PNAC) that enables authentication protocol for any devices trying to connect through LAN or WLAN. The major difference between home networks and 802.1X networks is that authentication happens through a RADIUS server in the latter.
The RADIUS server will authenticate if a device or a user requesting access is a current member of your organization by verifying the certificate or the unique credentials. Once authenticated, RADIUS will communicate with the switch and, as per company policies, ask the switch to:
- Open a port to let the user access the internet, and
- Which port to open
In 802.1X port security, the RADIUS is telling the switch to open a port and which port to Open
Assign a VLAN to the port. The user then uses the port to communicate with the internet.
The best part of 802.1X port security is that the responsibility of verifying is shifted to a RADIUS or an AAA server. These servers are designed to authenticate users or devices. The right RADIUS server can mitigate all the gaps in authentication to ensure that only authorized devices are granted access to the port.
Challenges With 802.1X Port Security
The strength of this PNAC is dependent on the authentication protocol used. Using a password-based authentication protocol such as EAP-TTLS/PAP and PEAP-MSCHAPv2 leaves room for attacks.
Passwords can easily be stolen physically or over the air. Verifying an identity with a password leaves room for ambiguity and is not a good identity context. Enabling EAP-TLS for digital certificate-based authentication can mitigate security risks.
Certificates are considered more secure because they cannot be stolen or replicated. Also, each certificate carries some unique information that helps verify the identity of the client with absolute certainty.
EAP-TLS: The Gold Standard of Network Security
Extensible Authentication Protocol-Transport Layer Security (EAP-TLS) is an IETF open standard defined in RFC 5216 and is deployed on WPA2-Enterprise networks to enable certificate-based authentication using X.509 digital certificates.
It is considered a gold standard in network security because of its simplicity despite it being the most secure. EAP-TLS authentication protocol is not based on any complicated encryption. Instead, it relies on public key cryptography, a type of asymmetric cryptography that uses public-private key pairs to establish symmetric cryptography. So even if someone manages to steal a certificate and get access to the public key, they will not be able to do anything without the private key that is attached to the device.
Arguably the best feature of the EAP-TLS protocol is that it is mainly based in the cloud and works well with SAML-based directories that provide an extra layer of security and negate the need for on-premise directories such as AD or LDAP that are expensive to both install and maintain.
EAP-TLS also helps lay the foundation to creating a zero-trust network as with certificates you get better identity context than in password based authentication especially server certificate validation that ensures that a user or device connecting to your network does not become a victim of a man-in-the-middle attack. In EAP-TLS, authentication is complete after the public-private key handshake is successful, not just with the device but with the server as well.
Validating both the client and server certificate before establishing a connection prevents any possible spoofing attack, as the onus to verify is not left with just the client but the server as well.
Cloud RADIUS for 802.1X Port Security
Cloud RADIUS is the only passwordless EAP-TLS RADIUS server in the industry. It is designed to work closely with your cloud infrastructure and can do real-time look-ups with your cloud identities at the time of authentication to ensure that only users you have authorized can access your network.
Cloud RADIUS gives you a single platform to monitor and control all the devices connected to your network. With Cloud RADIUS, you can dynamically manage network access control for better port security from a single pane.
Many organizations shy away from using certificates because of the complexity of setting up the Public Key Infrastructure (PKI). Cloud RADIUS has an in-built PKI that automates certificate management, making it a seamless passwordless authentication experience.
With Cloud RADIUS, certificate enrollment is automatic for managed devices. JoinNow MultiOS, for BYOD, eliminates the challenges of certificate misconfiguration and allows users to onboard unmanaged devices with just the click of a few buttons.
Implement 802.1X Port Security With SecureW2
The strength of a network depends on how secure every aspect of your network is. Securing your information in the cloud is not enough. For well-rounded security, securing every element, both hardware and software, on your network is important. That includes all the ports in your network, which are exactly like checkpoints to your network.
Secure your network with SecureW2’s Cloud RADIUS, which gives you absolute control over your network with greater visibility. It is vendor-neutral and can easily integrate with any major identity providers to do real-time look-ups at the time of authentication for network policy implementation. Cloud RADIUS supports MAC Auth Bypass for IoT devices that do not support 802.1X configuration, thus bringing these devices under network visibility that would otherwise have gone unmonitored. Click here to learn more about pricing.




