
RADIUS Wi-Fi Security Benefits
The presence Wi-Fi networks everywhere these days has made them a popular target for hackers. Numerous types of attacks have sprung up designed to target users on wireless networks, such as Man-in-the-Middle attacks. With the right defensive measures, such as a robust authentication system, though, organizations can protect their Wi-Fi from such attacks.
A Remote Dial-In Authentication User Service server (RADIUS server for short) protects your networks by ensuring only authorized users can access them. RADIUS servers are seeing an increase in use across all types of businesses due to the wide array of security benefits they offer. In this article, we’ll closely examine what a RADIUS server can do for a Wi-Fi network, how it works, and why organizations on the fence should consider deploying them.
What is a RADIUS Server?
A RADIUS server is an authentication server built upon the RADIUS protocol used for network security. It ultimately prevents unauthorized access to wired and wireless networks as well as VPNs. They are sometimes also called AAA servers because they have authentication, authorization, and accounting capabilities.
RADIUS provides authentication services when a user or device initially requests access to the network. Because it needs a directory of user information to reference, RADIUS servers can also verify the level of authorization individuals should be granted once they’ve been verified. Finally, they provide accounting in the form of RADIUS event logs that provide a detailed snapshot of the devices accessing a networking resource.
There are many authentication protocols that can be used alongside RADIUS. These typically determine how an end-user or device authenticates, and the most popular options include credential-based authentication (username and password) or certificate-based authentication.
The Key Components of RADIUS Authentication
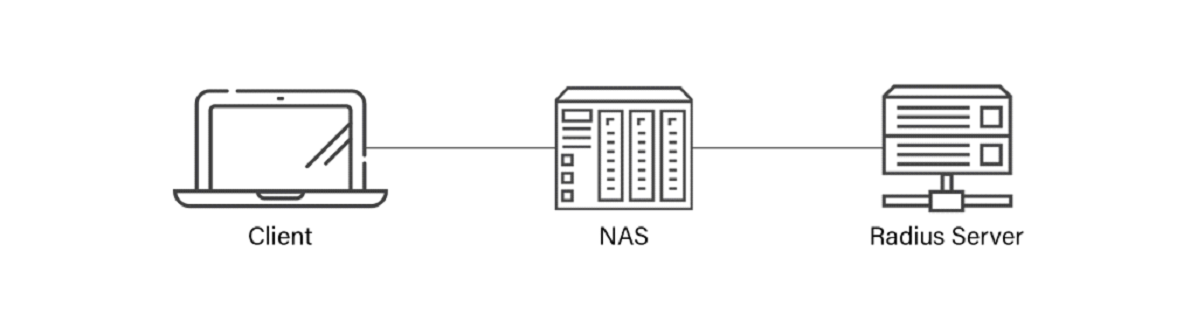
To work successfully, RADIUS authentication requires a few components beyond the standard password-based Wi-Fi authentication you see in home networks. It requires an enterprise-grade wireless access point, the RADIUS server itself, and a shared secret that keeps interactions between the client and server safe.
As we mentioned previously, you’ll also need to determine what kind of authentication protocol you want to use in tandem with your RADIUS. The authentication protocol dictates what method users and devices will use to prove their identities when they request access. We commonly see businesses use PEAP-MSCHAPv2, EAP-TLS, or EAP-TTLS/PAP.
RADIUS Wi-Fi Authentication Protocols
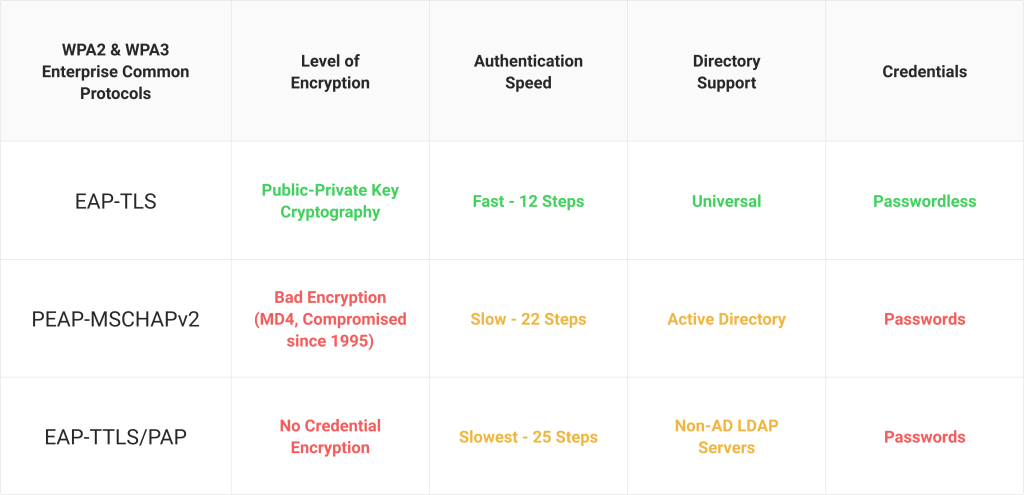
Before we get into how RADIUS authentication works with Wi-Fi, it’s important to understand some of the more popular authentication protocols in use. We see organizations typically use one of three protocols:
- EAP-TLS
- PEAP-MSCHAPv2
- EAP-TTLS/PAP
Extensible Authentication Protocol-Transport Layer Security (EAP-TLS)
EAP-TLS is a passwordless authentication protocol. Instead of logging into a wireless network through the use of a username and password, users and devices are issued digital certificates that are used for authentication. A digital certificate is a bit like a virtual photo ID; it’s made of a template that contains a lot more information about the individual using it. Additionally, digital certificates can’t be stolen or transferred, which gives administrators a much higher degree of certainty about who’s actually on their network.
One of the largest barriers to entry with certificate-based authentication is that it requires a Public Key Infrastructure (PKI) to maintain and manage those certificates. However, with the right tools, such as onboarding technology, modern PKIs are much easier to implement than they have been historically.
PEAP-MSCHAPv2 (Protected Extensible Authentication Protocol-Microsoft Challenge Handshake Authentication Protocol version 2)
PEAP-MSCHAPv2 is a common credential-based authentication protocol. It does make some improvements over previous iterations, such as using an encrypted EAP tunnel when passwords are transmitted over-the-air.
However, PEAP-MSCHAPv2’s biggest flaw is its dependence on passwords. Even with some improvements over its predecessors, it’s still a vulnerable authentication protocol based on a hashing algorithm that has been compromised for decades. Even Microsoft has recommended that organizations consider certificate-based alternatives to PEAP-MSCHAPv2, such as EAP-TLS.
EAP-TTLS/PAP
This protocol is similar to PEAP-MSCHAPv2 in that it also uses credentials for authentication. Using credentials means it carries the same disadvantages that we mentioned in the previous section.
EAP-TTLS/PAP requires devices to verify a server certificate before connecting to a network, ensuring they don’t connect to the wrong one. Once this is verified, the device then sends the user’s credentials through an encrypted EAP tunnel, much like with PEAP-MSCHAPv2. However, it’s easy to misconfigure devices for EAP-TTLS/PAP, and a single mistake can lead to end-users sending their usernames and passwords over-the-air in a cleartext format, easy for a hacker to intercept.
How Does RADIUS Authentication Work for Wi-Fi Security?
How RADIUS works in conjunction with Wi-Fi security varies depending on the authentication protocol your network uses. For credential-based authentication protocols, those credentials are sent to the RADIUS (generally through a protected tunnel) and then the RADIUS verifies them in the directory before granting access. The directory is usually an Identity Provider, such as Azure AD (Entra ID), Active Directory, Google, Okta, or more.
With EAP-TLS, which uses certificates for authentication, the process is a little different. The device will start by verifying the authenticity of the RADIUS server’s certificate first. That way, the user is prevented from authenticating and connecting to the wrong network, which commonly happens in Evil Twin AP attacks. After, the device sends its certificate to the RADIUS, and the RADIUS checks whether or not the certificate is expired.
With our Cloud RADIUS platform, there’s an extra step. Cloud RADIUS integrates with all major cloud Identity Providers. At the time of authentication, it can communicate directly with Azure AD, Okta, Google, or OneLogin to verify the existence of a user once their certificate’s validity is confirmed. This ensures that the most up-to-date access policies are applied; even if you haven’t revoked the certificate yet, the user will be denied access if they’re deactivated in your IDP. Credentials aren’t sent over-the-air at all during this process, protecting them from exposure.
The Security Risks of Credential-Based Wi-Fi Authentication
While using credentials for Wi-Fi authentication is typically one of the simplest routes to take, it’s far from the most secure. Organizations tying their Wi-Fi to passwords expose their networks to many risks, including the following:
- Vulnerability to Over-the-Air Attacks
- Password Mismanagement
- Poor End-User Experience
- Increased IT Workload
Vulnerability to Over-the-Air Attacks
Transmitting sensitive information over-the-air is always a risk, even with rigorous security practices in place. Tying your network access to these credentials and requiring users to send them over-the-air is a tremendous risk.
There are many attack vectors designed to intercept communications transmitted wirelessly. From the variety of Man-in-the-Middle attacks to Evil Twin AP attacks that trick end-users into sending their credentials to the wrong place, there are plenty of ways to target credentials through password-based authentication methods.
The best way to keep your credentials secure is to limit their use as much as possible. This means choosing a way to authenticate users that doesn’t involve exposing their credentials to unnecessary risk.
Password Mismanagement
One of the most challenging aspects of passwords is managing them. The average end-user understands password etiquette, such as avoiding reusing passwords and creating complex ones.
Unfortunately, the number of accounts using this authentication method has increased. Users have tons of passwords they need to maintain these days, and remembering them all is a hassle. Because of this, it’s common to repeat passwords or only vary them slightly between accounts. Some may even default to using extremely insecure, simple passwords that can easily be guessed in attacks such as dictionary attacks.
Another issue in mismanagement is the sharing of passwords. If you’re using a pre-shared key (PSK) network based on a single password, and that password has been shared with more than several people, you can be virtually certain they’ve shared it with others.
Poor End-User Experience
Aside from the security issues that come with managing multiple passwords, there’s the end-user experience to consider. Juggling dozens of passwords is frustrating. It becomes exponentially harder when organizations implement strict access control policies based on passwords, such as having to change passwords regularly and imposing specific complexity requirements.
Passwords make user access difficult. And if a user ever forgets their password or doesn’t change it in time before expiration, things become more complicated.
Increased IT Workload
One primary difference we’ve heard from organizations that implemented certificate based authentication is the unexpected drop in support tickets. End-users are bound to forget passwords once in a while, and when this happens, they need to reach out to your support team to regain access to their resources.
Besides being annoying for the end-users, who experience a drop in productivity while they wait, this is time-consuming for your IT department. Some surveys have shown that a single password reset can cost $2,700, which isn’t surprising when you factor in how long the ticket takes to resolve.
Benefits of Certificate-Based Authentication & RADIUS Servers for Wi-Fi
The alternative to password-based authentication is certificates. Using certificates for user authentication provides a range of benefits, especially when combined with the security of a RADIUS server:
- Improved Security Based on Cryptography
- Enhanced Ability to Enforce Granular Network Access Control Policies
- Easier End-User Login Experience
- Ability to Integrate with Your Existing Network Infrastructure
Improved Security Based on Cryptography
Implementing a RADIUS authentication server for your Wi-Fi access is already a step forward, but it’s enhanced when you bring in the cryptography offered by digital certificates. Certificates utilize robust asymmetric encryption to prevent the open transmission of sensitive data over the air. Each one is comprised of a private key and a public key, which are mathematically linked to one another.
Because credentials are no longer being sent to your wireless access points, a number of attacks are prevented. Man-in-the-middle attacks can’t steal passwords. Even if they intercepted a certificate, it cannot be stolen or transferred, since the private key is never sent over-the-air.
Enhanced Ability to Enforce Granular Network Access Control Policies
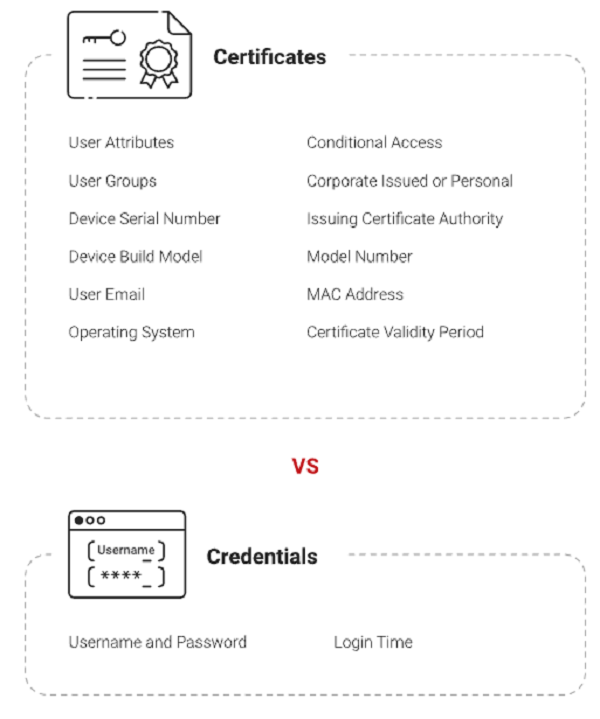
A Public Key Infrastructure (PKI) is necessary to manage and deploy certificates, but it along with a RADIUS server can be designed to leverage information from your infrastructure, including your directory services or mobile device management (MDM) platforms.
Certificate templates contain detailed information – much more detailed than anything you get from a username and password. Because templates can contain a range of information from your Identity Provider and MDM, you can apply that information to network access policies. For example, our Cloud RADIUS service can segment users into different VLANs based on their user group, such as segmenting HR employees from DevOps employees who may need more bandwidth.
Easier End-User Login Experience
Passwordless authentication offers a better experience for your end-users at the same time it enhances security. It saves users the time they would otherwise have to spend re-entering complex passwords. It also gives them one less password to worry about juggling in their repertoire; certificates allow them to connect automatically.
The authentication process with certificates is also slightly faster. This means faster connections for everyone.
Ability to Integrate with Your Existing Infrastructure
Both RADIUS and PKI can integrate with your network infrastructure, including with Identity Providers such as Microsoft Active Directory, Azure AD (Entra ID), Google, Okta, and more. Our RADIUS in particular leverages a seamless integration with your Identity Provider through the Identity Lookup process which verifies a user’s status in real-time during each authentication.
SecureW2 Makes RADIUS Server & PKI Security for Wi-Fi Accessible & Simple
While RADIUS server configuration and setup haven’t been too intimidating for organizations historically, implementing a PKI has. We often hear administrators say the more they’re involved with a PKI, the less they want to manage them.
Fortunately, with the right platform, deploying both a PKI and RADIUS doesn’t need to be challenging. Our passwordless authentication suite, which includes both JoinNow Cloud RADIUS and PKI, provides organizations with everything they need to deploy passwordless security for their wireless networks. Both were designed with vendor neutrality in mind, integrating with a range of vendors, as you can see in our detailed configuration documentation. Manage and automate the entire certificate lifecycle, as well as create granular network policies, all from a single, centralized location.
We’re confident in our solutions. Reach out to our knowledgeable solutions engineers today to see how our platform looks in action.




