
How to Configure RADIUS over TLS (RadSec)
As strong as the RADIUS protocol is, there are several vulnerabilities that attackers can and have used to infiltrate your network and farm credentials. These vulnerabilities lie with RADIUS’s reliance on the MD5 message algorithm, which has been exploited in the past.
Although that can be overlooked by just investing in stronger network security around RADIUS, the increasing use of roaming services calls for a stronger security measure to protect data shared over the internet.
Nowadays, organizations need a strong Public Key Infrastructure (PKI) that supports RadSec capabilities to protect their networks. Luckily, there are plenty of low-cost PKI solutions out there that any organization can integrate.
What is RadSec?
RadSec is an 802.11x protocol that allows RADIUS servers to transfer data over TCP and TLS for increased security. With RadSec capabilities, you can transfer RADIUS packets through public networks while still ensuring end-to-end security through the transport layer.
Enabling RADIUS communication over TLS increases the level of security for authentication carried out across the cloud network. When configured, this feature ensures that the RadSec protocol is used for safely transmitting the authentication and accounting data between the Instant AP and the RadSec server.
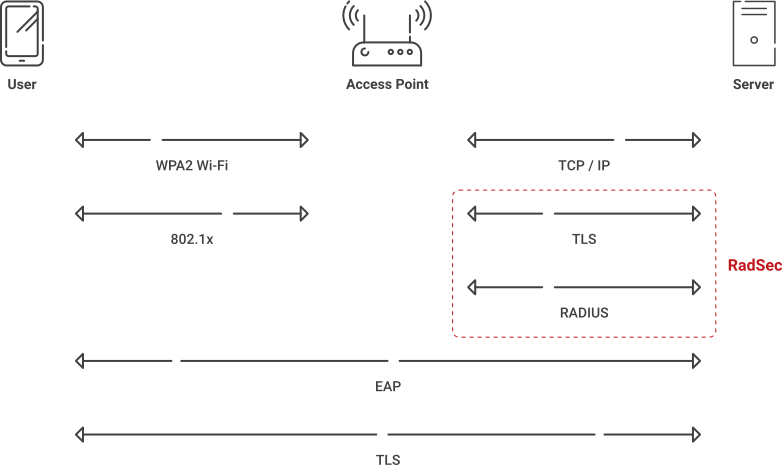
RADIUS vs RadSec
RADIUS relies on UDP (User Datagram Protocol) to transfer information. UDP has been determined as less secure because messages are sent without being required to set up communication channels. UDP is acceptable if package loss is not a concern, but it makes RADIUS communication more vulnerable because important data packets could be lost. Attackers can exploit this vulnerability to infiltrate your network and farm credentials.
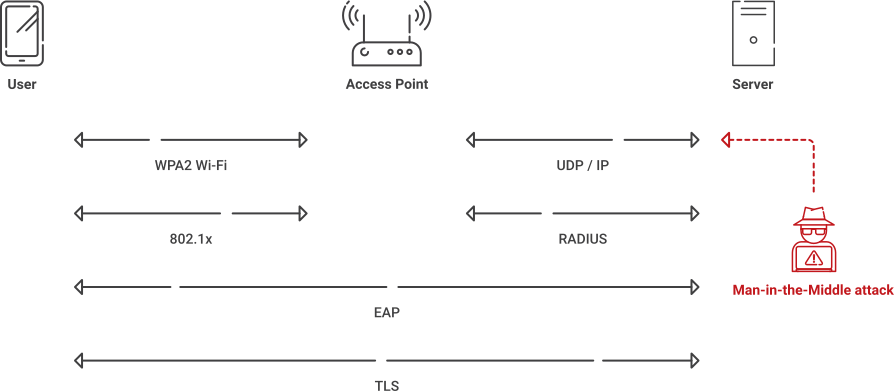
RadSec is imperative when it comes to OpenRoaming. OpenRoaming traffic is sent over the internet, meaning most of the time you won’t know where it will end up or if it will end up in the correct order. The transfer of RADIUS packets over the internet involves breaking them down and reassembling them at the destination. Usually, admins aren’t concerned with some date being lost over UDP, but it can cause frustration or even security issues. A quick Google search of “lost RADIUS packets” shows how frustrating it is for admins to lose packets.
OpenRoaming causes an issue with the RADIUS protocol because RADIUS relies on the client and server sharing IP addresses and using a shared secret to establish a connection. A roaming solution, like eduroam, requires a large amount of coordination that normal RADIUS isn’t equipped to handle.
With RadSec, the connection is limited within the PKI. One organization issues certificates to both the client and the server. The PKI serves as a trust anchor so the RADIUS server and client can safely communicate and no prior knowledge has to be established.
Eduroam: RadSec Deployment in Action
Eduroam has quickly become the standard 802.1X network in higher education and works by allowing students/staff members to use credentials from their home university directory to access Wi-Fi at a remote campus that is also part of the eduroam federation.
Eduroam is a shared SSID that is commonly broadcasted in educational institutions around the world, which makes it a target for attackers to exploit as an imitation network. This is one of the primary reasons thousands of universities provide onboarding solutions—to ensure devices are being properly configured with server certificate validation enabled so credentials are only provided to the institution’s proper RADIUS server.
However, this service requires a large amount of coordination, top-down management, and admin work. Broadcasting eduroam worldwide requires governmental bodies and institutions to coordinate with one another, but only a select number of locations have been approved for eduroam access. Only time will tell what advances will be made to RadSec.
RadSec Configuration Process
The RadSec Configuration Process can be broken down into a couple of high-level steps: configure the RadSec destination and the TLS Connection. You need to specify the RADIUS server transferring the data and define the RadSec destination so the RADIUS traffic can be directed there.
- Import the server CA certificate that issues server certificates.
- You can cross import CAs if you have two separate CAs issuing server and client client certificates.
- This will establish Server Certificate Validation.
- Configure the destination hostname (server name)
- Optional: Specify the port you want to use if the default RadSec port (2083) isn’t ideal.
- Specify the TLS parameters
- TLS dictates how data will be transferred through RadSec
- The best practice is to use the EAP-TLS protocol (SecureW2 JoinNow comes pre-built for EAP-TLS).
Does RadSec Work with NPS/AD Setups?
At this time, it doesn’t seem like RadSec is possible with an Active Directory/NPS setup, unless you’re able to find a third-party extension. However, RadSec would be pretty unnecessary for most AD environments anyway.
It is possible to implement RadSec with a radsecproxy that converts legacy RADIUS into RadSec, but this only works for on-premise systems. In order to forward connection requests to a remote NPS or another RADIUS server:
- Create a Remote RADIUS Server Group.
- Configure a connection request policy that forwards requests to that Remote RADIUS Server Group.
With this configuration, NPS can forward authentication requests to any RADIUS server, and users with accounts in untrusted domains can be authenticated. This Windows forum post explains in more detail.
Enable RadSec with Cloud RADIUS
While RadSec is an open protocol that anyone can use, you need the right hardware in order to implement it. The Github link above allows you to implement RadSec if your current hardware doesn’t natively support it, but configuration can be a monumental task. Luckily, SecureW2’s CloudRadius license supports RadSec.
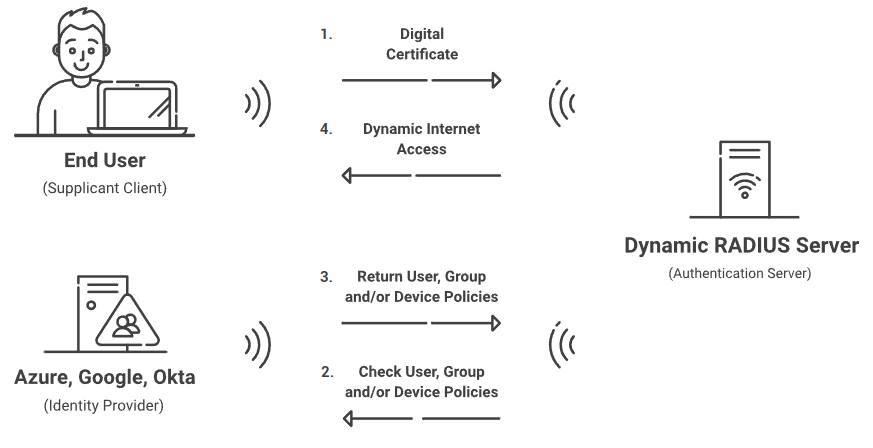
Cloud RADIUS is a turnkey RADIUS solution that can be implemented into virtually any environment because it works with all major SAML and LDAP Identity Providers like Google, Okta, and Azure. Designed from the ground up for certificate-based authentication, it eliminates both the risk of sending credentials over the internet and the risk for credential theft.
Our turnkey PKI solution easily distributes client and server certificates, including provisioning RadSec servers with a server certificate. And our JoinNow onboarding solution can be completed by users in minutes, or use API gateways to equip managed devices with certificates, all with no end-user interaction.
Everything you need for certificate-based authentication can be set up in under an hour! Check out our affordable solutions for bringing certificate-based authentication to your network resources.