The Stages of 802.1X Authentication
The 802.1X authentication protocol is a state-of-the-art cryptographic network technology that provides protection for both wired and wireless networks. The fundamental concept behind the implementation of security protocols is rooted in the necessity to safeguard confidential data and authenticate individuals endeavoring to illicitly infiltrate the system.
Upon network enrollment, devices must undergo authentication, which is facilitated by the IEEE 802.1X standard for both LAN and WAN connections. The IEEE 802.1X protocol is enveloped by the Extensible Authentication Protocol (EAP) over LAN, which is commonly referred to as “EAPOL” or “EAP over LAN,” in order to facilitate communication during the authentication procedure.
A thorough understanding of this protocol is imperative for entrepreneurs to make an informed decision regarding its compatibility with their network’s security needs. The objective of the analysis is to gain deeper insights into the underlying mechanisms of an 802.1X implementation within a network and to ascertain the relative significance of each constituent element.
802.1X Authentication Protocol
802.1X is utilized for the following reasons:
- Network access identifier and credential-based authentication
- Authentication, authorization, and accounting are centralized
- Security for the public network
- Distribution of keys for dynamic encryption
802.1X Authentication Components
The following are the components of the 802.1X network authentication:
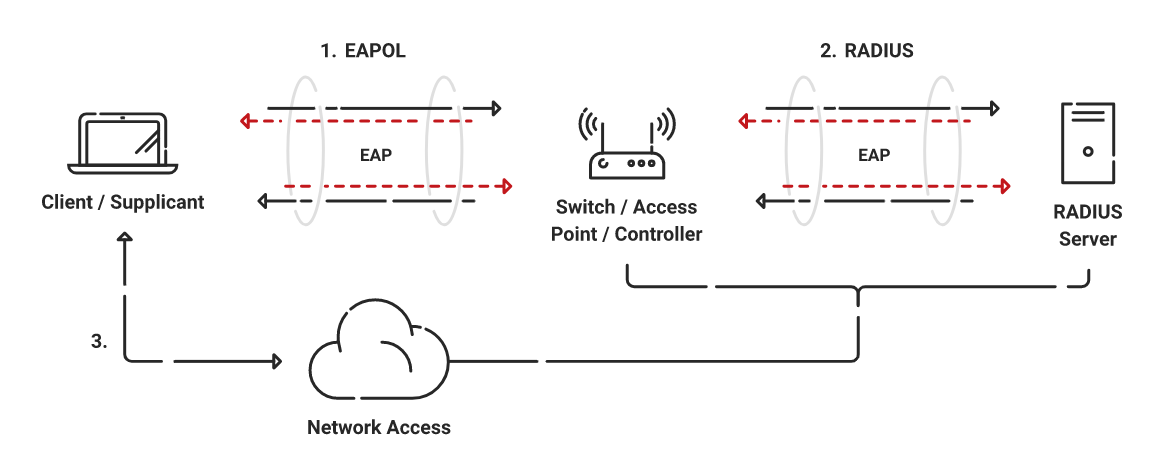
- Extensible Authentication Protocol (EAP): This is an 802.1X transport technique used to authenticate supplicants (hosts/PCs) against a backend server (RADIUS) via an authenticator (Switch).
- EAP over LAN (EAPoL): This is used for authentication across a network and is part of the 802.1X standard (Port-Based Network Access Control) Supplicant and Authenticator’s encapsulation protocol.
- RADIUS Protocol: The AAA protocol that EAP uses.
802.1X Authentication Roles
802.1X network devices can employ the following roles:
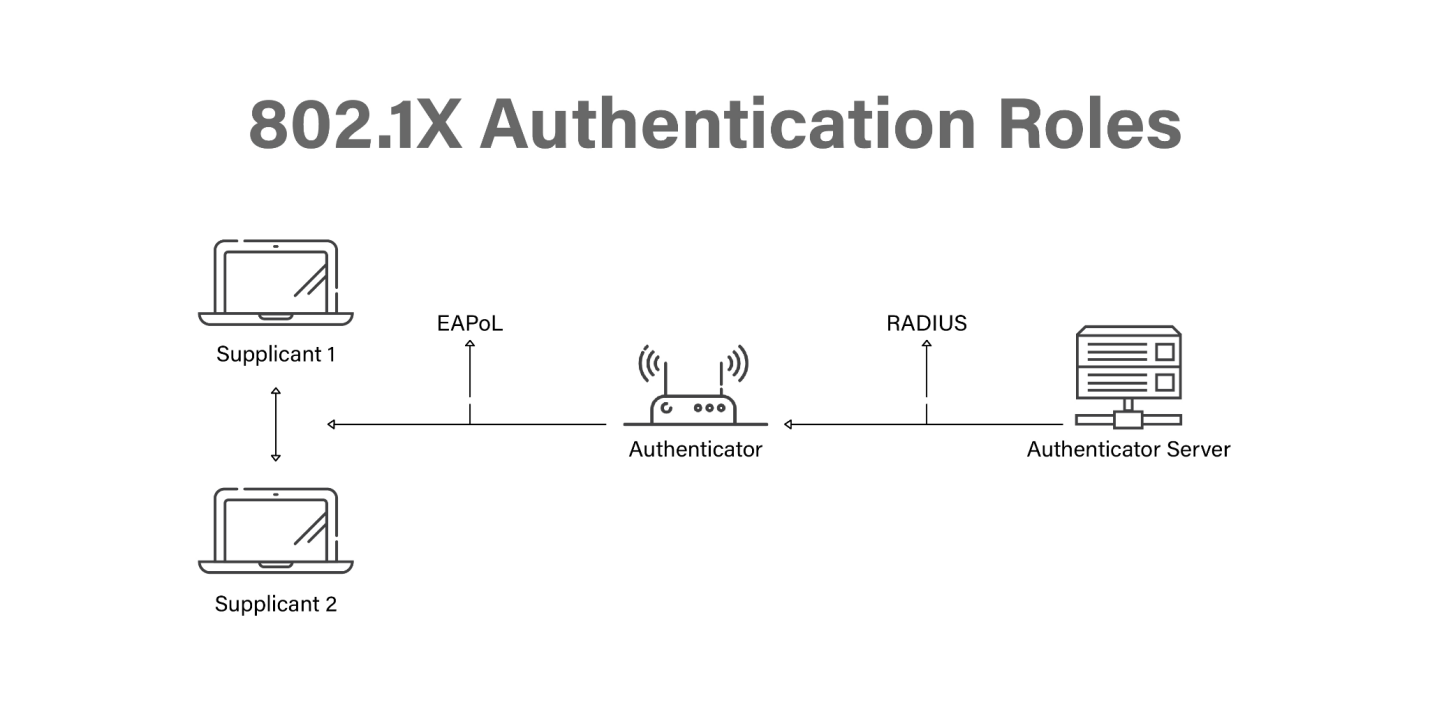
- Supplicant: This is the application running on the endpoint or the client’s device. It exchanges messages with the authenticator over EAPoL and issues authentication tokens. Various clients such as Windows, macOS, and Cisco AnyConnect are all examples of supplicants. These supplicants are compatible with 802.1X, which allows for machine and user authentication.
- Authenticator: This is a network access device (NAD) such as a switch, wireless access point, or wireless LAN controller that serves as the authenticator (WLC). It limits network access depending on the authentication state of the user or endpoint. The authenticator also works as a liaison, transforming Layer 2 EAP-encapsulated packets from the supplicant into RADIUS packets for transmission to the authentication server.
- Authentication server: This is responsible for authenticating clients. Authentication servers check the legitimacy of the endpoint and report back to the authenticator with approval or denial.
802.1X Authentication Process
Let’s take a closer look at the 802.1X authentication process.

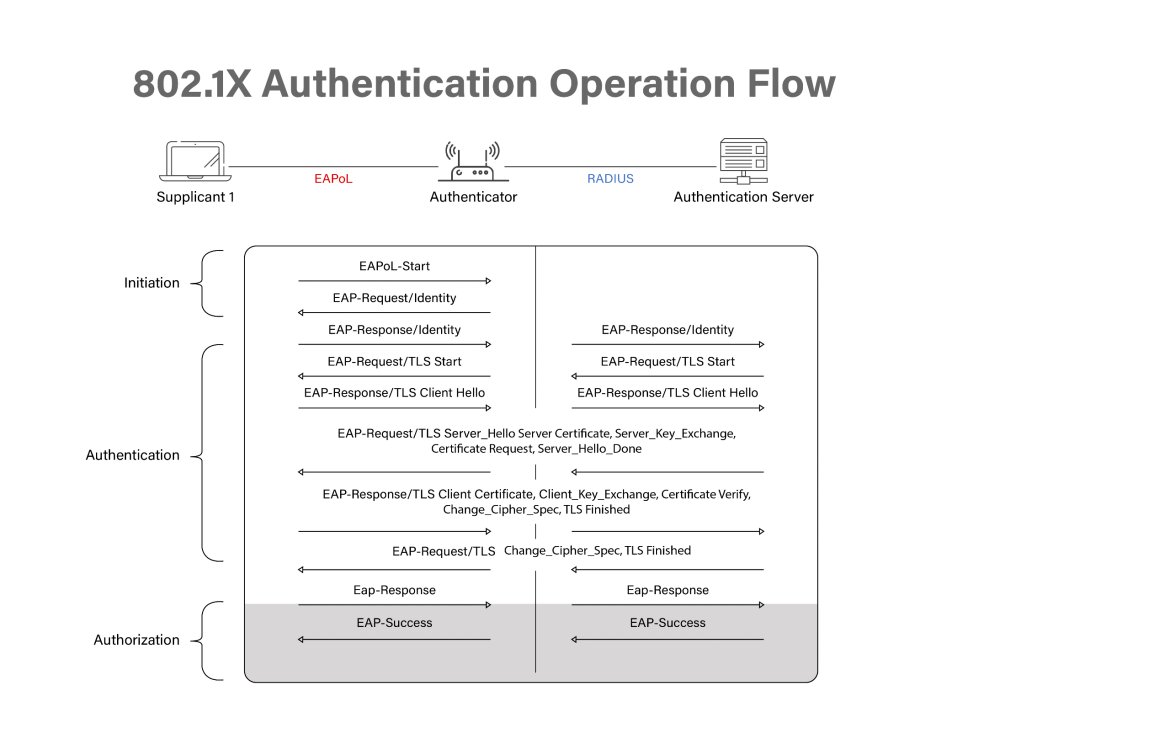
- For client authentication, the client/supplicant initiates an EAP session by sending an EAP-start message.
- The EAP-request identity message is sent from the access point.
- By responding with an EAP-response packet, the client divulges its identity to the authentication server.
- To ensure that the client is who they say they are, the server employs a particular authentication procedure.
- In response to the access point’s authentication request, the authentication server will either deliver an accept message or a refuse message.
- The AP will either deliver the client an EAP-success packet or a reject packet, depending on the outcome of the authentication process.
- With the client’s port now in an allowed state, the access point will continue to relay traffic once the authentication server has accepted the client.
802.1X Authentication Methods
The IEEE 802.1X standard offers a comprehensive structure for the authentication of wireless networks. During the authentication process, 802.1X utilizes the Extensible Authentication Protocol (EAP) to enable the transmission of messages between peers.
The 802.1X architecture enables support for multiple authentication protocols, including EAP-Transport Layer Security (EAP-TLS), Protected EAP (PEAP), and EAP-Tunneled TLS (EAP-TTLS). In addition to enabling client authentication, these protocols also enable network verification of the client’s identity. For additional details, it is advisable to consult this comparative assessment of enterprise authentication protocols leveraging WPA2 and WPA.
PEAP and EAP-TTLS are two EAP protocols that utilize a shared password for network authentication. It is feasible for an attacker to utilize a password guessing methodology by choosing a password from a catalog of probable passwords, such as a lexicon.
On the other hand, EAP-ultimate TLS’s objective is to just offer better network security by means of digital authentication; i.e., certificates.
802.1X Authentication Flow
Now let’s look at the 802.1X authentication flow in more detail.
EAP-TLS Authentication
Presently, the Extensible Authentication Protocol (EAP) is among the most widely utilized authentication mechanisms for transmitting client data wirelessly via 802.1X. Furthermore, it is noteworthy that EAP-TLS stands out as the sole EAP protocol that furnishes certificate-based authentication, which is widely acknowledged as the most reliable form of authentication. The subsequent sections detail the steps entailed in the 802.1X EAP-TLS authentication process and its implications for establishing a secure network connection.
Three parties are involved in EAP-TLS authentication: the supplicant (user’s device), the authenticator (switch or controller), and the authentication server (RADIUS server). Initialization, commencement, negotiation, and authentication are the four major categories that comprise the authentication procedure.
Let’s take a look at each of these categories:
- Initialization: The authenticator detects a supplicant attempting to access the secure network.
- Initiation: Essentially, this is a way for the supplicant, authenticator, and authentication server to say ‘hello’ to each other.
- Negotiation: When a user requests access to a network, the supplicant and the authentication server trade identifiers.
- Authentication: Now the verified user may join the 802.1X network and begin browsing in a secure mode.
EAP-TLS authentication is often quicker than authentication based on credentials because it happens automatically without user intervention. When the device is within range of the secure network, it will automatically establish and finish the connection.
Deep-Dive Into EAP-TLS Authentication Flow
The visual representation presented depicts a comprehensive and sequential dissection of the 802.1X EAP-TLS authentication mechanism.
- Public key infrastructure (PKI) certificates are issued to clients on the client side, while PKI certificates are distributed to clients off-band on the server side.
- As a first step in establishing a secure connection, both the supplicant and the authentication server exchange ‘Hello’ and then prepare their certificates for the authentication process.
- Establish 802.11 Data Link
- The supplicant establishes a connection to the authenticator. This will allow for a secure exchange of information between the two parties.
- EAPoL Start
- The acronym EAPoL (Extensible Authentication Protocol over LAN) denotes that data may be transmitted between all three parties through a secure LAN connection. This is also where the authentication technique — in this example, EAP-TLS — is decided.
- Identity Section
- 4a. Identity Request
- The supplicant requests the identity of the authenticator to ensure it is sending the client certificate to the correct place.
- 4b. Identity (anonymous) Response
- The authenticator requests that the supplicant identify itself.
- 4a. Identity Request
- RADIUS Access Request (anonymous)
- The information that identifies the supplicant and authenticator is sent to the RADIUS to confirm their identity and allow for authenticating information to be sent.
- 5a. Server Certificate
- The RADIUS sends its server certificate to confirm its identity through server certificate validation.
- 5b. Client Certificate
- The supplicant validates the identity of the authentication server certificate. After validation, the supplicant sends its client certificate.
- RADIUS Access (or Reject)
- The RADIUS authentication server accepts the client certificate and verifies the client’s identity as an authorized network user. RADIUS delivers an Access or Reject message to the authenticator based on the user’s certificate.
- EAP Success (or Failure)
- According to the RADIUS Access or Reject message, the authenticator either grants the supplicant access to the network or denies access. If the reply is “Success,” a port on the switch is opened so the supplicant may communicate directly with the authentication server.
- Message 1: EAPOL-Key
- Message 2: EAPOL-Key
- Message 3: EAPOL-Key
- Message 4: EAPOL-Key
- Subsequently, a sequence of communications referred to as the EAPOL-Key exchange ensues. The process involves a series of four steps wherein the authenticator and supplicant engage in a handshake to establish a secure connection and generate encryption keys. The aforementioned keys are utilized for the purpose of encrypting data that is intended to be transmitted via wireless means, thereby guaranteeing that all active network communications are encrypted and impervious to outside parties.
- Linked here is a detailed list of keys that are generated during this handshake.
- Encrypted Channel
- The end result of EAP-TLS authentication is an encrypted channel of communication. The user is ready to access the secure network and utilize all resources available to them.
Cloud-Based RADIUS Authentication

The proliferation of cloud computing and telecommuting has resulted in the transmission of sensitive passwords outside of corporate networks, where they are exposed to Over-the-Air attacks. The adoption of certificate-based network authentication over passwords has been recommended by prominent organizations such as Microsoft and CISA, due to its numerous benefits.
With SecureW2’s Cloud RADIUS, network access can be managed based on various parameters, including user type, time of day, and device type. Additionally, our Cloud RADIUS solution is agnostic to vendors, allowing for seamless integration with any Identity Provider (IDP) of your choosing. By leveraging Cloud RADIUS, you can perform instantaneous user lookups against Azure, Okta, and Google Workspace. This grants you unparalleled control over rule enforcement, surpassing the capabilities of any alternative solution.
Through our various cutting-edge capabilities, such as Azure multi-factor authentication, Intune automatic revocation, Windows Hello for Business login, and many more, integrating with SecureW2 expands the range of customization possibilities available to you.
Click here to inquire about pricing.




