Breaking Down the 802.1X Protocol
The 802.1X protocol is a pivotal authentication protocol in network security that is widely used. Its foremost aim is to enhance the security of the network by transitioning from WPA2-PSK networks, which are deemed less secure due to their dependence on a solitary shared password, to the more dependable WPA2-Enterprise/802.1X standard. The implementation of this modification enables individual users to possess unique login credentials, thereby significantly bolstering network security measures.
In this article, we’ll take a closer look at the components of the 802.1X protocol, with particular emphasis on the utilization of cloud infrastructure, such as Azure AD (Identity Provider) and SecureW2’s Cloud RADIUS (RADIUS Server).
Understanding the 802.1X Protocol
The 802.1X protocol comprises three fundamental components: the supplicant, the authenticator, and the authentication server. We will carry out an in-depth analysis of each of these components.
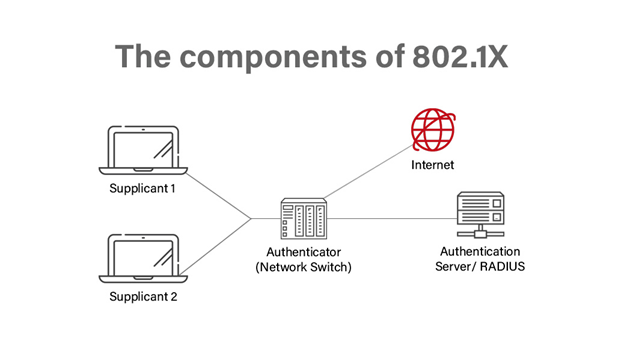
Supplicant
The term “supplicant” pertains to the endpoint device that triggers a solicitation for network admittance, encompassing a variety of network-capable devices such as laptops, smartphones, and other analogous gadgets. The offering is accessible in both wired and wireless arrangements.
The supplicant triggers the authentication process by sending an initial request to the authenticator. The identified entity demonstrates its authentication and identification protocols to verify its legitimacy and gain access to the network.
Authenticator
Between the supplicant and the authentication server, there is an intermediary device called the authenticator. It controls access to the network resources as a gatekeeper. The authenticator acts as the supplicant’s point of entry into the network and is frequently a network switch or wireless access point (WAP). It enforces access control restrictions and transmits the supplicant’s authentication requests to the authentication server.
The authenticator utilizes the Extensible Authentication Protocol over LAN (EAPOL) to establish communication with the supplicant. The process involves the interrogation of the supplicant’s identity and credentials, followed by the transmission of authentication requests to the authentication server, culminating in the return of the authentication outcome to the supplicant.
Authentication Server
The authentication server must verify the credentials provided by the supplicant. Authentication of users is enabled through the verification of the applicant’s identification and credentials. The deployment of the authentication server can be either on-premises or as a cloud-based service.
In the cybersecurity domain, it is standard practice for an authentication server to gain entry to a user directory, which could encompass Active Directory, LDAP (Lightweight Directory Access Protocol), or Azure AD. The network access authorization process involves scrutinizing the provided credentials against the stored user data to determine the eligibility of the applicant.
The authentication server responds to the authenticator with an authentication result that states whether the applicant’s credentials are legitimate or not. The authentication server delivers an access-accept message, allowing the applicant to access the network if the credentials are legitimate. An access-reject message is delivered in the event that the credentials are false, preventing network access.
Authentication Flow
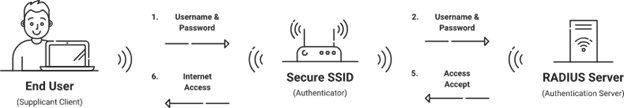
A series of communications between the supplicant, authenticator, and authentication server take place throughout the authentication process of the 802.1X protocol. The flow is summarized as follows:
- Supplicant Initialization
- Authenticator Challenge
- Supplicant Identity
- Authentication Exchange
- Credentials Verification
- Authentication Result
Supplicant Initialization
The supplicant initiates communication with the authenticator by sending an EAPOL Start frame, expressing its intention to authenticate and acquire access to the network.
Authenticator Challenge
The authenticator sends an EAP Request/Identity frame in response to the supplicant’s EAPOL Start frame. The supplicant is asked to confirm their identification in this frame.
Supplicant Identity
The supplicant sends an EAP Response/Identity frame in response to the authenticator’s challenge. Information about the supplicant’s identity is contained in this frame.
Authentication Exchange
The authenticator sends the applicant’s identity to the server for authentication. The authentication server assesses whether extra credentials are needed by comparing the identity to its user directory.
Credentials Verification
The supplicant may be asked for more information, such as a username and password, a digital certificate, or a one-time password (OTP), depending on the authentication server’s answer. The authenticator receives the desired credentials from the supplicant.
Authentication Result
The authentication server verifies the applicant’s credentials. Depending on whether the credentials are legitimate or not, it replies to the authenticator. The authenticator grants the supplicant access to the network if the authentication is successful. Otherwise, access is prohibited.
By abandoning common passwords and establishing individual user authentication with the help of the 802.1X protocol, organizations can improve network security by ensuring that only authorized users can access the network’s resources.
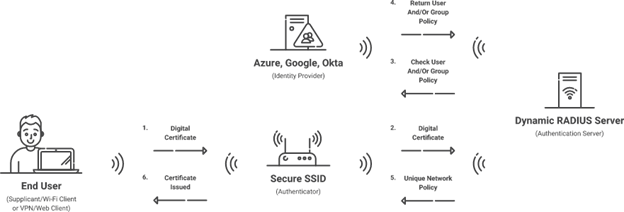
How Does the 802.1x Protocol Work?
The implementation of the 802.1X protocol leverages the flexible and versatile Authentication Protocol (EAP) to furnish an adaptive and versatile authentication infrastructure. The implementation of EAP enables the utilization of diverse authentication methodologies, including but not limited to passwords, electronic certificates, smart card technology, and biometric verification.
Three different EAP methods are employed in 802.1X authentication:
- EAP-TLS (Transport Layer Security)
- EAP-PEAP (Protected EAP)
- EAP-MSCHAPv2 (Microsoft Challenge-Handshake Authentication Protocol version 2)
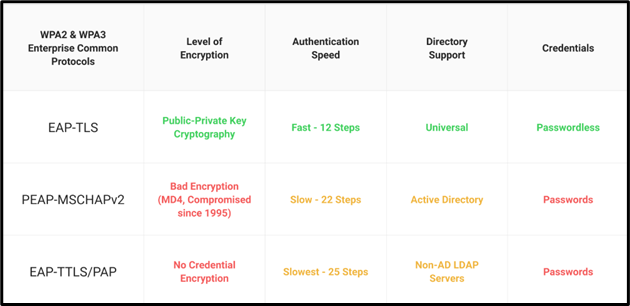
EAP-TLS (Transport Layer Security)
The implementation in question utilizes digital certificates for the purpose of authenticating both the supplicant and the authentication server. Mutual authentication has been implemented to facilitate the validation of identities for both parties involved. The implementation of digital certificates on both the supplicant and the authentication server is imperative for the utilization of the most secure EAP method, EAP-TLS.
PEAP MSCHAPv2
PEAP MSCHAPv2 (Protected Extensible Authentication Protocol with Microsoft Challenge Handshake Authentication Protocol version 2) is a wireless authentication protocol. It shields the authentication procedure from eavesdropping and tampering by enclosing it behind a secure tunnel. It makes use of the password-based MSCHAPv2 protocol for authentication.
EAP-TTLS/PAP
EAP-TTLS/PAP (Extensible Authentication Protocol) -Tunneled Transport Layer Security/Password Authentication Protocol) is an authentication mechanism that combines the benefits of EAP and TTLS. It creates a secure tunnel using TLS and permits the use of several authentication techniques, including the PAP technique. PAP is a straightforward password-based authentication mechanism. However, because the password is transmitted in clear text, it is less secure than alternative approaches.
Implementing the 802.1X Protocol
The deployment of the 802.1X protocol necessitates a series of procedures, such as setting up the network architecture, configuring the RADIUS server, and configuring the network devices. Let’s dive deeper into each phase for a comprehensive analysis.
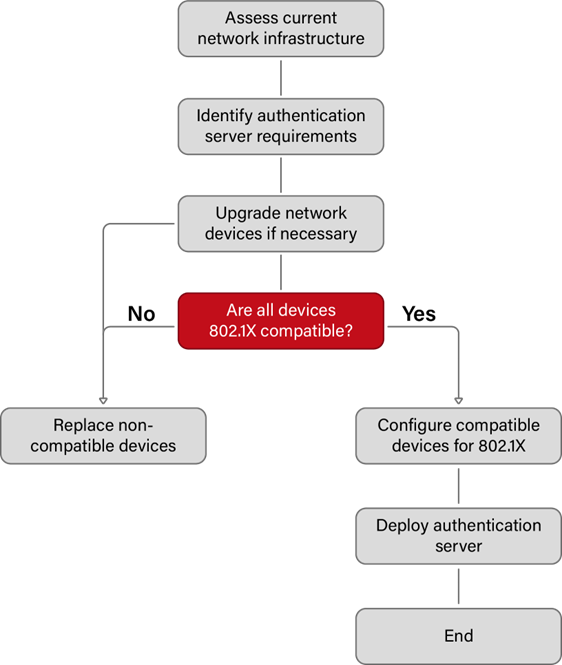
1. Preparing the network infrastructure
- Determine which network devices will be supporting 802.1X by identifying them. This typically includes switches, wireless access points, and routers.
- It is imperative to verify the presence of 802.1X support within the firmware of all network devices. Ensure that the firmware is updated to a version that is compatible, if deemed necessary.
- Examine the network topology to comprehend how network devices are positioned and identify the 802.1X authentication points.
- It is essential to establish authentication protocols that dictate the permissible devices and users authorized to access the network, along with the corresponding authentication procedures to be enforced.
2. Configuring the RADIUS server
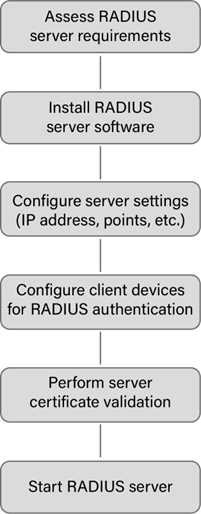
- It is highly advisable to implement the RADIUS server software on a separate and exclusive server for enhanced security measures. It is imperative to verify the compatibility of the selected RADIUS server with your system before starting the installation and configuration procedures.
- Ensure the RADIUS server is properly configured with relevant details regarding the network devices, also known as RADIUS clients, that are accountable for performing user authentication. It is crucial to ensure the accuracy and specificity of pertinent details, including IP addresses, shared secrets, and other relevant data.
- Integrate the LDAP/SAML or identity providers user databases, which will hold user credentials for authentication, with the RADIUS server.
- Create network policies on the RADIUS server to specify the unique access restrictions and authentication guidelines for various user groups or devices.
3. Configuring the Network Devices
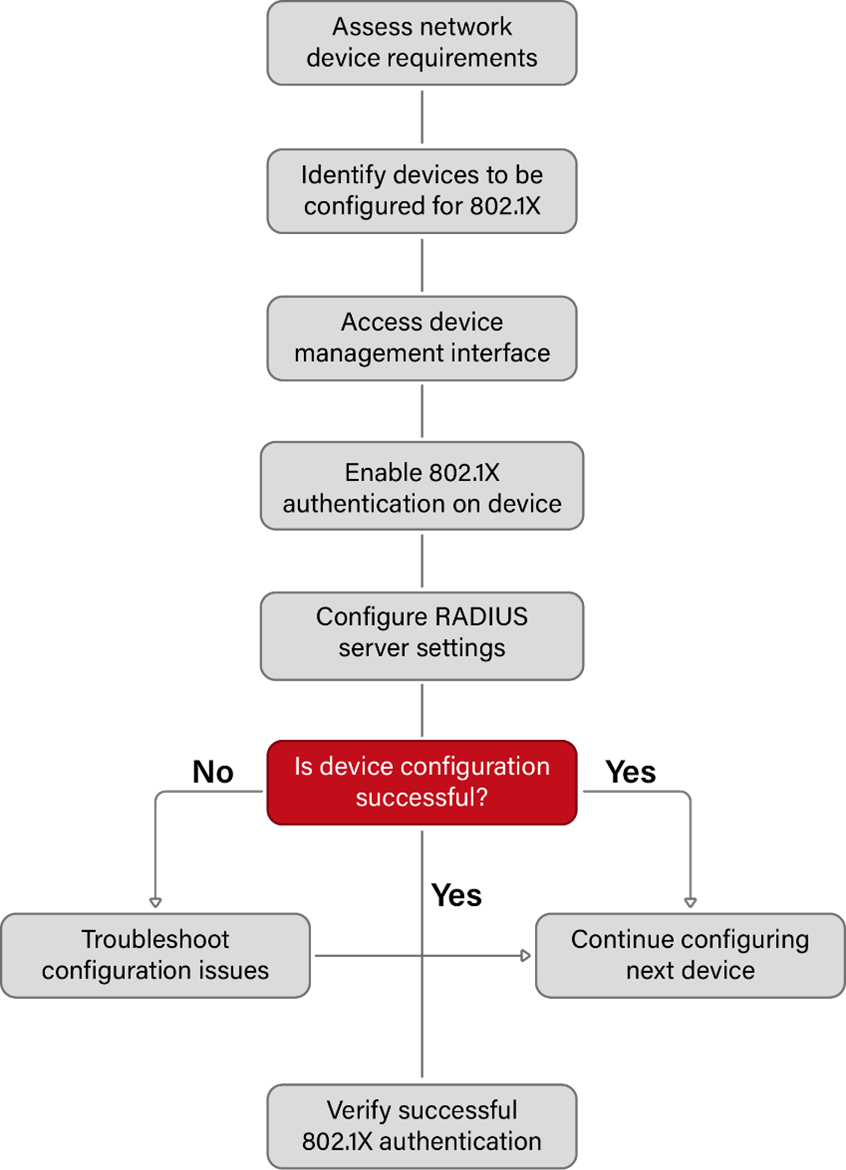
- Enable 802.1X on all network devices by logging into each device that will use the protocol. Usually, the administration interface or command-line interface of the device is used for this.
- It is imperative to configure the IP address and shared secret of the RADIUS server on all network devices to ensure optimal security measures. This measure guarantees the creation of a protected means of communication between the device and the RADIUS server to facilitate the process of authentication.
- It is recommended to implement per-port authentication options for the network device configuration. Based on the particularities of your network configuration, it is recommended to cautiously activate 802.1X authentication on specific ports instead of deploying it across the entire network. It is recommended to configure the reauthentication intervals and opt for the suitable authentication method, such as EAP-TLS or EAP-PEAP.
- To ensure segregation of unauthenticated or guest devices from the primary network, it is recommended to configure a guest VLAN on the network devices. In the event of unsuccessful authentication, the respective devices shall be assigned to this VLAN.
4. Testing and Deployment
- Test the configuration by connecting devices to the network ports and watching the authentication procedure to confirm the 802.1X settings. Authenticated devices must have the proper access privileges and unauthenticated devices must be limited to the guest VLAN or not allowed access at all.
- Keep an eye out for any problems or anomalies by continuously monitoring the network devices, RADIUS server logs, and authentication procedures. Investigate and fix any issues that surface.
- Following a successful test, all network devices in your infrastructure should have the 802.1X configuration installed. This can include going through the configuration processes on each device again.
Advantages of the 802.1X Protocol
The 802.1X protocol has various advantages over other authentication methods, including:
- Individual User Authentication
- Centralized Authentication
- Flexible and Extensible
- Improved Security
Individual User Authentication
The 802.1X protocol is utilized for individual user authentication, thereby guaranteeing that solely authorized users are granted access to network resources. The aforementioned approach confers a significant advantage over alternative authentication techniques such as WPA2-PSK, which mandates uniform password usage among all users and complicates network access monitoring.
Centralized Authentication
The process of user authentication is executed through the utilization of an authentication server, which provides centralized authentication services for the entire network. The consolidation of user authentication has simplified the management process by eliminating the need for individual authentication for each device.
Flexible and Extensible
The protocol supports many EAP techniques, enabling organizations to select the best authentication strategy for their requirements. This gives flexibility in selecting an authentication strategy that meets the security requirements of the organization.
Improved Security
The implementation of the 802.1X protocol fortifies the security of the authentication process by encrypting the communication between the supplicant and the authentication server. The implementation of robust security measures hinders malicious actors from obtaining confidential user data by guaranteeing the safeguarding of authentication information against interception.
Disadvantages of the 802.1X Protocol
The 802.1X protocol, however, also has significant drawbacks, such as:
- Complexity
- Network Infrastructure Requirements
- Compatibility Issues
Complexity
The protocol is more difficult to implement than other authentication methods since it necessitates extensive configuration and administration. To manage the protocol’s deployment and administration, you’ll need a knowledgeable IT team.
Network Infrastructure Requirements
The protocol needs assistance from network infrastructure elements like RADIUS servers and network switches. For smaller organizations, this may result in higher hardware and software expenses, which can be a big drawback.
Compatibility Issues
When used with outdated network devices that do not support the protocol, there may be compatibility concerns. This may restrict the protocol’s applicability in some settings and necessitate upgrading the protocol’s supporting network infrastructure components.
An effective onboarding solution assists organizations in overcoming the limitations of the 802.1X standard. The solution lessens the complexity involved with deploying the protocol by providing a user-friendly interface and streamlined configuration process. As a result, organizations without substantial technical know-how or dedicated IT staff can use it more easily.
Additionally, by handling authentication procedures and easily integrating with existing network devices, onboarding solutions minimize the need for expensive infrastructure investments. Because it guarantees compatibility with a variety of hardware, including older devices, organizations can use the protocol without having to invest in pricey updates.
Overall, an efficient onboarding solution makes it easier to adopt the 802.1X protocol, decreases the amount of equipment needed, and fixes compatibility problems, enabling organizations to make use of its security advantages more quickly and affordably.
SecureW2: Empowering Network Security with the 802.1X Protocol
In conclusion, the 802.1X protocol is a crucial security measure for any organization wanting to safeguard its network from unauthorized access. The protocol implementation process calls for careful network infrastructure planning, RADIUS server configuration, and network device configuration — all of which can be challenging tasks.
However, with SecureW2’s scalable and configurable cloud-based onboarding solutions like Cloud RADIUS, the process can be streamlined for both managed and unmanaged devices. SecureW2 is a suitable solution for network security because of its low price, direct interaction with major IDPs and MDMs, and simple device onboarding. To find out more about how we can assist you with implementing the 802.1X protocol and securing your organization’s network, get in touch with SecureW2 right away.