How to View RADIUS Event Logs
You need to prove that your network is secure, your data stays private, and unauthorized access is never an option. RADIUS ensures authentication, guaranteeing access is locked down to only trusted users. A RADIUS event log contains comprehensive information on the devices and users trying to gain access to your network.
If you encounter connectivity issues or suspect unauthorized access, the RADIUS logs should be your primary information source for troubleshooting. In addition, RADIUS event logs can be tied to a SIEM tool to create alarms during connection issues and help with any authentication issues during client-user connections.
What is a RADIUS event log?
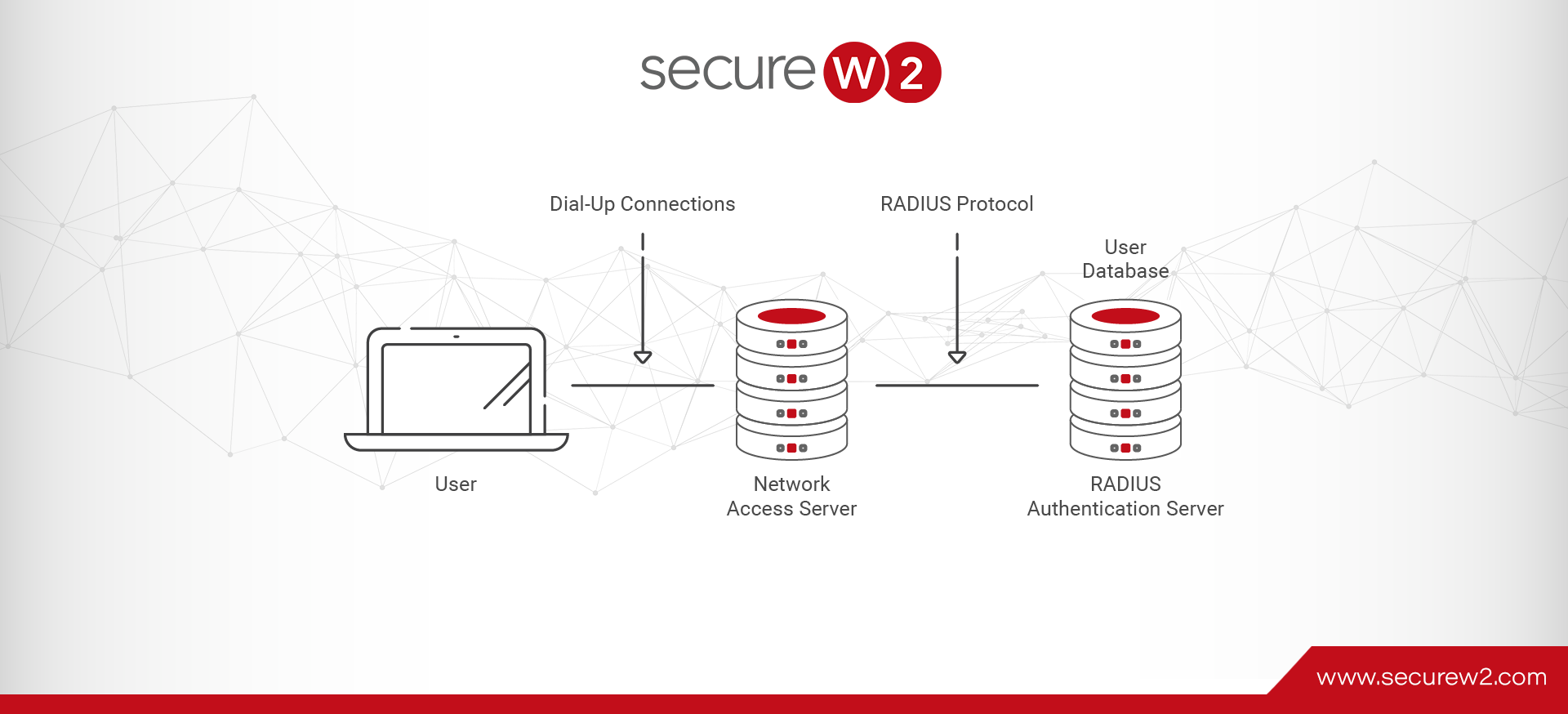
A RADIUS server is responsible for Authorization and Accounting in addition to its primary role of Authentication, hence its alternate name: “AAA server.” Given the importance of these tasks, it should come as no surprise that one function of a RADIUS server is to log and store a record of all the requests it receives. A RADIUS client communicates with a RADIUS server using the RADIUS protocol to enforce network access for users.
An event log records all the events when a RADIUS client is required to connect to a network. Event logs are used to troubleshoot issues, track all the users and devices that request authentication, and generate reports for compliance purposes.
RADIUS event logs may be used for:
- Compliance audits
- Troubleshooting authentication issues
- Troubleshooting VPN issues
- Tracking use
- Tracking users
- Tracking devices
RADIUS event logs are a powerful tool for managing your 802.1x network and users.
What information is included in a RADIUS Log?
The data contained within a RADIUS event log varies from RADIUS to RADIUS, but there are some standard fields that you’re likely to find regardless of your RADIUS provider.
- Date
- Time
- Name
- Client Type
- Record Type
- Authentication Type
RADIUS vendors with a robust management and reporting suite, like our SecureW2 Cloud RADIUS, can add and remove data fields from event logs. Custom RADIUS event logs can be handy for compliance audits.
In addition to event logs for authentication and authorization requests, RADIUS servers usually log other event types, such as server startups, shutdowns, or service interruptions. These make up a small fraction of the overall logs but are particularly useful for investigating outages.
RADIUS For Compliance Purposes
Every organization is responsible for securing its data, maintaining compliance, and ensuring full visibility into access events. Your network and access protocols are critical—determining who gets in, what they can access, and how their activity is tracked. IT teams must demonstrate that controls are strong, every access attempt is logged, and no gaps exist.
A RADIUS server talks to an organization’s directory that’s stored on-premise or tied to an identity provider for unique user identification at the time of authentication and providing access to the network.
Admins can use RADIUS to enforce access controls on a VPN, segment users and devices into VLANs, and apply granular security policies to ensure the right access for the right users.
It also enables users to access the network by authenticating themselves with their identities and subsequent applications.For compliance, RADIUS covers audit log requirements when it ties to a tool for event logging.
How to view FreeRADIUS logs
FreeRADIUS is an open-source framework for implementing your DIY RADIUS. Configuring and maintaining it requires extensive technical expertise and hardware (or cloud server space), but it’s powerful and infinitely customizable.
During the configuration process for a FreeRADIUS server, admins are required to designate a folder for RADIUS event log output. FreeRADIUS doesn’t do anything with the logs, so you’ll need to manually process the raw data to a more human-readable form if you use the logs extensively.
How to view NPS logs
NPS is Microsoft’s pseudo-RADIUS that has seen widespread adoption due to its tight integration with the rest of the Microsoft environment. In particular, it plays well with Active Directory (AD), the IdP of choice for many organizations.
Viewing event logs generated by an NPS RADIUS is easy, if unintuitive. Rather than finding them in NPS, check the Windows Event Viewer (another system part of the larger Windows Server package).
However, neither AD nor NPS has leapt into the cloud. Some workarounds allow you to use them in a limited capacity. Still, organizations using cloud directories like Google, Azure, or Okta should not use stopgap measures for network security. Limited support and antiquated systems leave your network vulnerable.
How To View RADIUS Logs in Securew2s Cloud RADIUS
SecureW2s Cloud RADIUS is cloud-based and can be deployed anywhere, unlike an on-premise RADIUS. It provides detailed logs and extensive information for every log request, along with ACCESS_ACCEPT and ACCESS_REJECT responses in the management portal. You can view the event logs under the Data & Management by selecting the RADIUS Events option.
Cloud RADIUS Event Log Fields and Meanings
Cloud RADIUS event logs were designed to give administrators a clear snapshot of each authentication attempt. As such, we’ve incorporated numerous fields into them, including the following:
⦁ Region – Origin of the connection request.
⦁ Timestamp – Recorded time of the connection request.
⦁ Identity – Username used during the authentication.
⦁ Subject/Common Name – Name of the user using the certificate or token.
⦁ User Principal Name – Email ID of the user trying to connect to the network.
⦁ Device – Information related to the device, such as a serial number.
⦁ Certificate serial – The serial number of the device’s certificate when trying to connect to the network.
⦁ MAC Address – Media Access Control Address of the device trying to connect to the network.
⦁ Client Public IP – IPv4 address of the device needed for the network to reach the device.
⦁ Operating System – Software that supports the device trying to connect to the network.
⦁ User Role – The user role is designated by the administrator to which the user belongs.
⦁ Network Policy – This shows the network policy that applies to the user.
RADIUS Reply – Status of the RADIUS Authentication (ACCESS_ACCEPT/ACCESS_REJECT)
⦁ Error Message – If applicable, the reason why the remote access authentication attempt failed.
Cloud RADIUS Event Log Search Filters
You can also apply filters for specific searches, like a particular user if a single person is experiencing problems connecting to the network. Filters are also used for OS, MAC addresses, and other fields to narrow your search and troubleshoot quickly.RADIUS logs are an excellent tool for troubleshooting when you get reports that users can’t connect to your network.
Leverage SecureW2’s Cloud RADIUS As A RADIUS Event Logging Tool
SecureW2 Cloud RADIUS offers a comprehensive solution for network traffic monitoring through its advanced authentication, authorization, and accounting capabilities. By leveraging certificate-based authentication, Cloud RADIUS ensures that only trusted devices and users can access the network.
Our Cloud RADIUS provides detailed event logs that give information on every login attempt, whether successful or failed attempts. As an IT administrator, you can filter logs to know the exact error and troubleshoot faster. Event logs are essential to modern network security as they allow you to be vigilant and facilitate efficient network monitoring. Our CloudRADIUS also lets you export data to an SIEM provider and Syslog servers and monitor connectivity issues with real-time intelligence.
We have affordable solutions for organizations of every size.
Check out our pricing page here.