MAC vs Router Mode For RADIUS Authentication
Our dependence on internet connectivity spans work and leisure, necessitating safeguarding our confidential information from unauthorized access. Implementing authentication protocols is a highly effective method for a secure network. Various authentication protocols exist, such as RADIUS and modem/router-based authentication. Both methodologies provide a degree of protection but vary in efficacy and user-friendliness.
This blog post aims to analyze and compare RADIUS MAC authentication and modem/router-based authentication to assist you in selecting the optimal secure network solution for contemporary times and its execution. Also, it offers valuable insights into the authentication world for business owners, IT professionals, and network security enthusiasts.
Let us delve into the intricacies of RADIUS MAC Authentication and Modem/Router-Based Authentication.
What is a RADIUS Server and How Does it Work?
Overview of Certificate-Based RADIUS Authentication
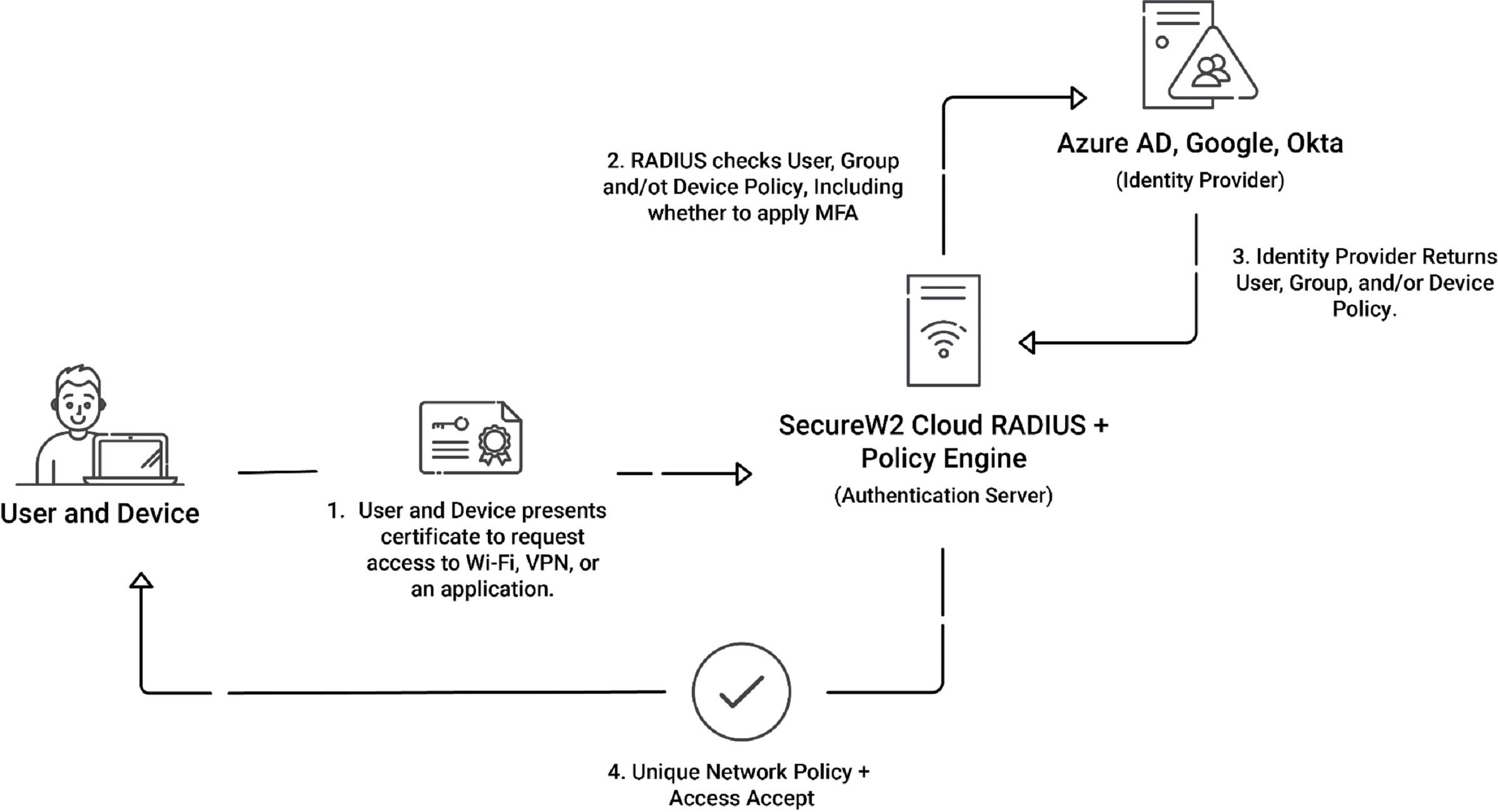
RADIUS certificate-based authentication is a strong security method that improves access to network control by using digital certificates to validate users. Certificate-based authentication, as opposed to standard both the username and password authentication techniques, is based on digital certificates given to both the RADIUS client and the authentication server. These certificates, frequently created using a public key infrastructure (PKI), create a safe and encrypted communication channel between the user and the network. As a centralized authentication and authorization protocol, RADIUS is critical in storing and validating these certificates, ensuring that only authorized users with valid credentials can access the network resources.
A user wanting to enter the network under this architecture offers a digital certificate rather than a username and password. The RADIUS server, equipped with a certificate authority (CA) or has access to an external CA, validates the provided certificate and compares it to its database of authorized users. Based on the successful validation of the digital certificate, the server authorizes or denies access. This method greatly improves security by removing the risks associated with password-based systems, such as credential theft and unauthorized access via compromised passwords. RADIUS certificate mac based authentication is particularly useful in contexts requiring greater security, making it a favored option for companies, financial institutions, and organizations prioritizing rigorous access control mechanisms.
Overview of RADIUS MAC & Modem/Router Authorization
The authentication process plays a vital role in ensuring the security of your network. There exist multiple methods for user authentication, but two frequently used ones include RADIUS MAC Authentication and Modem/Router-Based Authentication.
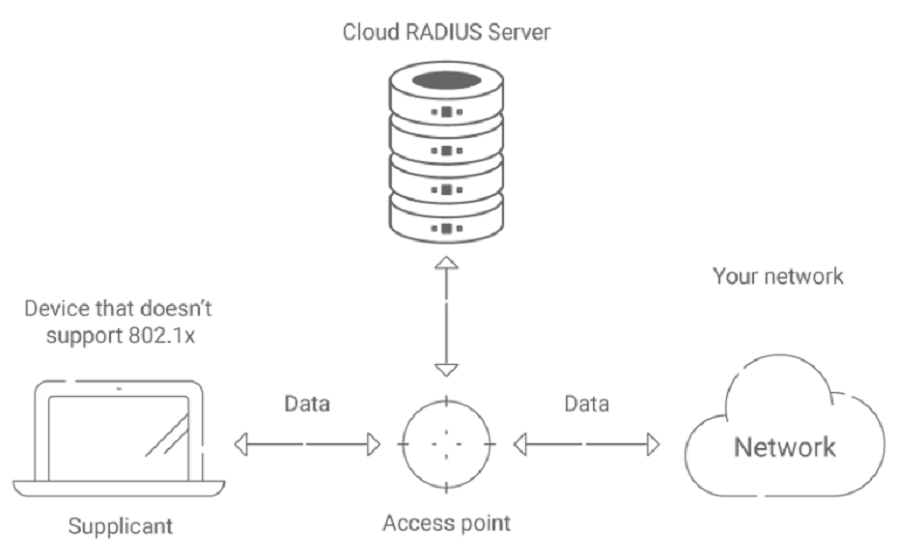
RADIUS MAC Authentication is a technique for authenticating users using RADIUS servers to establish them based on their MAC addresses. For example, a game console is a particular device that might not support 802.1X or certificate-based authentication. Hence this method is sometimes utilized in specific scenarios. This approach is also frequently employed in enterprise-grade networks where authentication of a substantial number of users is required.
Modem/Router-Based Authentication is an authentication technique integrated into the modem or router. This technique is frequently employed in domestic networks with limited users requiring authentication.
Although the authentication objectives are similar, multiple distinctions exist between the two approaches. RADIUS MAC Authentication offers enhanced security compared to Modem/Router-Based Authentication by leveraging a dedicated server for user authentication.
Moreover, implementing RADIUS MAC Authentication enables enhanced precision in regulating user access and authorizations. At the same time, Modem/router authentication boasts a lower hardware requirement and offers a more budget-friendly solution for small-scale networks.
Let’s discuss specific use cases for both protocols to substantiate the above claims further.
RADIUS MAC Authentication Use-Cases
RADIUS server MAC-based authentication is a powerful tool that can be used in many different use cases. A general application is in a corporate or enterprise environment where network security is paramount. In this scenario, implementing a RADIUS server is recommended for device MAC address authentication of authorized network devices. This can include laptops, desktops, smartphones, tablets, and IoT devices such as smart cameras and thermostats.
RADIUS MAC-based authentication can also be applied in the hospitality sector as a use case. In hospitality settings, seamless connectivity to the Wi-Fi network is a guest expectation for particular device integration. The implementation of RADIUS MAC authentication enables the hotel to guarantee that solely authorized guests can gain entry to the network while simultaneously delivering a user-friendly and streamlined login process.
RADIUS MAC authentication is a viable option in educational environments for granting network access to students and faculty members who require it from multiple devices. By implementing a RADIUS server for device MAC address authentication, the educational institution can guarantee sole admission of sanctioned devices to the network while furnishing a user-friendly and secure login interface.
Modem/Router-Based Authentication Use-Cases
Modem/router-based authentication is a prevalent technique for user authentication within a local network. Small businesses typically employ modem/router-based authentication to manage network access.
Firms commonly provide guest networks to facilitate internet access for visitors and customers. Modem/router-based authentication is standard in regulating network access and guaranteeing that only permitted users can establish connections. Public networks, such as those found in coffee shops and airports, often use modem/router-based authentication to control access and keep the network secure.
Steps to Determine the Optimal Authentication Protocol for Your Network
Optimizing the authentication protocol for your network is contingent upon several variables. When selecting an authentication method for your network, it is essential to consider the following:
⦁ Network size
⦁ Desired security level
⦁ Necessary control level
⦁ Cost and complexity
Let’s explore each variable.
Network Size and Device Count
For networks with a limited number of devices with restricted access can be used in various scenarios, such as home networks; public Wi-Fi/hotspots; small office networks, etc. The access rights can be setup for specific users based on their login credentials.
However, RADIUS MAC authentication is a more suitable alternative for a network with multiple devices.
Security Level
RADIUS MAC authentication provides an elevated level of security compared to modem/router-based authentication. Instead of using a credential or a certificate to authorize a device, the RADIUS confirms the MAC address and authenticates.
Level of Network Control
MAC-based RADIUS authentication offers high control over user access to a network. It provides a layer of security that ensures only authorized users can access the network. Network administrators can create user profiles with specific access rights and permissions with MAC radius authentication. They can set up rules that dictate which devices can access the network and at what times.
Evaluation of Cost and Technical Intricacies
The utilization of modem/router-based authentication is typically more cost-effective and simpler to configure compared to RADIUS MAC authentication. If enhanced security and control are necessary, opting for RADIUS MAC authentication could be a viable solution despite the added expenses and intricacies.
RADIUS MAC Authentication: The Winning Standard for Network Security
In contemporary network security, RADIUS MAC and modem/router-based authentication have unique benefits. In our thorough assessment, RADIUS MAC authentication represents the optimal resolution for network security.
RADIUS MAC address authentication offers enhanced security measures, making it a highly advantageous option. This is due to using a distinct identifier for every device. Whereas Modem/router-based authentication relies on usernames and passwords susceptible to being guessed or stolen by hackers.
RADIUS MAC authentication is significantly convenient for large-scale deployment. It employs a centralized server with all device data and authentication credentials. It can seamlessly connect to any RADIUS MAC-authenticated network without further configuration. This optimizes time and resources.
SecureW2 is the top-tier provider of RADIUS authentication and WPA2-Enterprise provider. So you’ll have the ultimate, unbeatable combination to safeguard your network with multiple layers of bulletproof security and thwart the most daring cyberattacks! Take a look here.
RADIUS MAC authentication provides an optimal resolution for network security in the contemporary era. In addition, the technology offers enhanced security measures that are highly resistant to circumvention and can be seamlessly deployed across a vast network.
Master RADIUS MAC Authentication via Configuration Guide
This comprehensive guide provides a detailed walkthrough for those seeking to configure RADIUS MAC address authentication. It will give a complete guide on RADIUS MAC authentication, covering the necessary prerequisites and configuration procedures. We’ll also provide tips and tricks to help you get the most out of your RADIUS MAC authentication.
Prerequisites
For the successful implementation of RADIUS MAC authentication,
⦁ A RADIUS server is required to act as the authentication server.
⦁ Network devices such as switches, routers, and access points must possess RADIUS support.
⦁ A network-connected device must be configured to transmit its MAC address to the RADIUS server for authentication.
Below is a sequential set of instructions to assist you in configuring RADIUS MAC authentication:
Step 1: Deploy a RADIUS Server.
Deploy the Cloud RADIUS server software on your server. Then, proceed to establish a connection between your electronic devices.
Step 2: Establish a network connection for your devices and configure them to utilize RADIUS authentication.
Step 3: Initiate Configuration of RADIUS Server.
Some other steps must be taken to set up your RADIUS server first. Check out this blog for more details on the initial RADIUS setup with Cloud RADIUS.
Step 4: Initiate a connectivity test by trying to establish a network connection using an unauthenticated device.
Step 5: Monitor authentication logs for your system.
It is crucial to regularly monitor authentication logs to prevent unauthorized network access by devices. Performing periodic log reviews can aid in detecting any unauthorized access attempts and implementing necessary measures to safeguard your network.
RADIUS MAC Authentication Best Practices
Utilize a Robust Shared Secret
The shared secret between the RADIUS server and the access point or switch must be intricate and challenging to predict. Implementing this measure will enhance network security by mitigating unauthorized access.
Implement IP Address or Network-Based Access Control
Implementing this measure will strengthen the security of your server and reduce the risk of unauthorized access by malicious actors, thereby safeguarding your network from potential compromise.
Perform Periodic Reviews of Server Logs
Performing periodic reviews facilitates proactively identifying potential security concerns before their manifestation.
Utilize VLANs for Network Segmentation
Implementing VLANs with RADIUS MAC address authentication is critical for network segmentation, improving security, and increasing control. Organizations may isolate and manage network traffic more efficiently by assigning distinct VLANs to authorized devices. Restricting users to certain segments according to their responsibilities or access needs enhances overall network performance and also aids in avoiding unauthorized access and any security breaches.
Ensure Firmware and Software Updates on access points, switches, and RADIUS servers.
It is crucial to regularly check for updates to guarantee you have the most recent security patches and features.
Which RADIUS Server Protocol Is Most Secure?
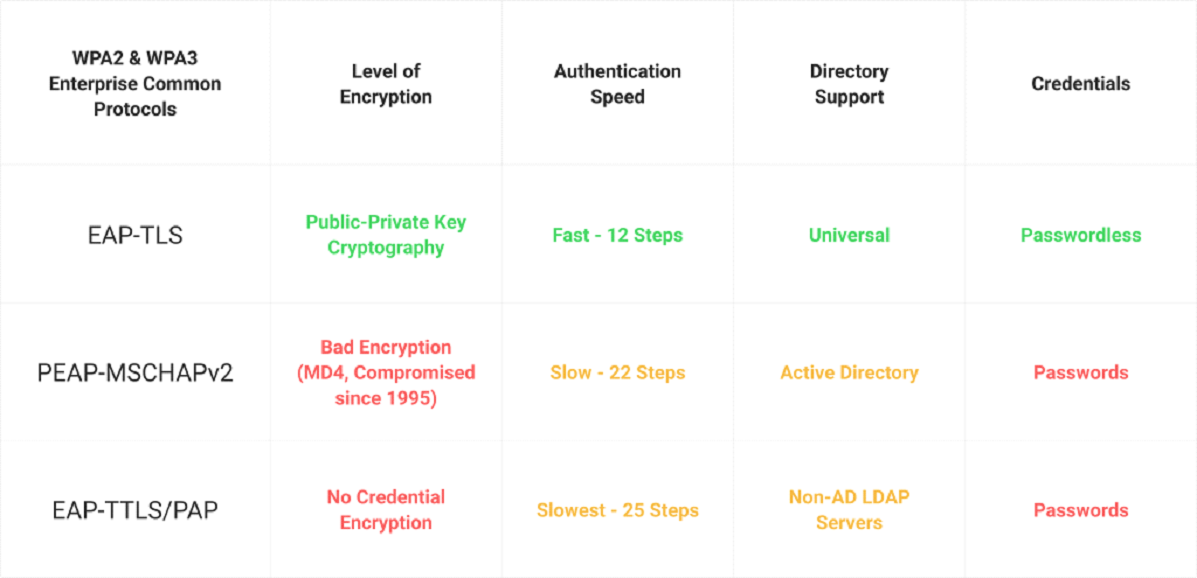
EAP-TLS (Extensible Authentication Protocol-Transport Layer Security) is one of the most secure authentication methods of RADIUS protocol options. EAP-TLS provides high security using digital certificates for RADIUS client and server authentication, resulting in a strong and encrypted communication channel. For RADIUS installations, EAP-TLS is an appealing choice for enterprises prioritizing robust and secure authentication methods since it provides an additional layer of security to network access.
Take Your Network Security to the Next Level with SecureW2
MAC address authentication effectively restricts network access by comparing a device’s MAC address to a list of enabled addresses the network administrator has set. While MAC authentication is successful owing to the uniqueness of MAC addresses, it is crucial to note that it can be faked and should not be depended on completely for network security.
Although offering MAC address authentication, Cloud RADIUS provides increased security with digital certificates, which provide cryptographic verification of both the device’s identification and the user. Unlike MAC authentication, digital certificates offer an additional layer of authentication, making them a more powerful option for safeguarding network access.
Contact us for more information on MAC authentication, digital certificates, or other security methods.