How To Protect Your Network From Wi-Fi Spoofing Attacks?
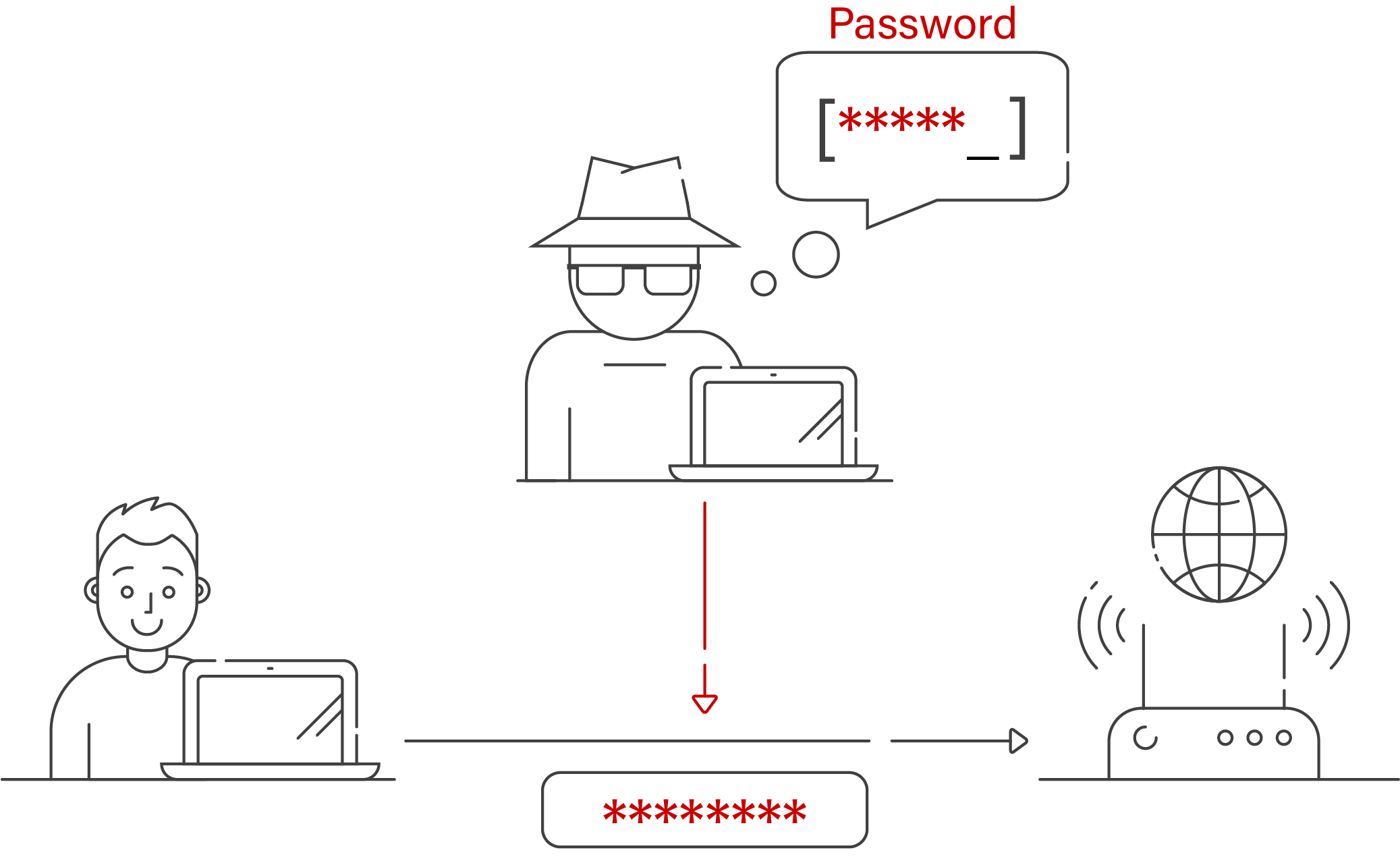
In today’s world, Wi-Fi is more important to our daily lives and is a major factor in how connected we are. Notwithstanding, a considerable number of users remain oblivious to the security vulnerabilities inherent in Wi-Fi utilisation. The act of Wi-Fi spoofing poses a significant risk to the integrity of your internet connectivity, ranking among the most severe security threats. The aforementioned scenario describes a type of cyber attack known as a rogue access point, wherein a malicious actor creates a counterfeit wireless network that appears legitimate, yet is designed to surreptitiously harvest sensitive information from unwitting targets.
An exemplar scenario is when affluent hotel patrons were subjected to the malevolent actions of cybercriminals who illicitly acquired data and conducted surveillance via the establishment’s wireless network. During the year 2017, a cohort of malicious actors directed their efforts towards compromising the security of individuals who were temporarily lodging at hospitality establishments located in the regions of Europe and the Middle East. The threat actors deployed rogue Wi-Fi access points to emulate legitimate hotel networks.
When users linked to the fake networks, the attackers were capable to intercept their internet activity. Then they collected confidential information including login information and credit card numbers. Since hotel Wi-Fi networks regularly go unencrypted and do not have the proper encryption tools, the assault proved effective.
We’ll discuss Wi-Fi spoofing in this post, including what it is, how it operates, and why it poses a severe security issue.
What Is Wi-Fi Spoofing?
Wi-Fi spoofing is the creation of a fake network connection that masquerades as an authentic one. By deceiving individuals into joining this phoney network, hackers may obtain sensitive information such as login credentials, financial data, along with other important details. Hackers might further compromise the target’s safety and privacy by installing malware on their device through the phoney connection.
Wi-Fi spoofing poses a significant threat to consumers and enterprises alike. The increasing number of Wi-Fi-enabled devices, like cell phones, tablets, laptops, and IoT devices, has increased the likelihood of Wi-Fi spoofing attacks. Next, we will examine in depth how Wi-Fi spoofing operates.
How Does Spoofing Work?
Depending on the attacker’s situation, spoofing may be done in a variety of ways utilizing a variety of routes and methods. Social engineering is required for a spoofing assault to be effective. With social engineering, attackers gather users’ sensitive data, which they subsequently use on those targeted to harass, extort, and humiliate them. The victim must deal with the attacker’s demands as a result.
Spoofing functions in line with an attack situation where a foe can target particular users. For example, because his identity would be revealed, the criminal is unlikely to send messages to users via his own email server. Therefore, he is going to take advantage of the hacked mail server. He will additionally send messages to users of public Wi-Fi in an effort to avoid being discovered.
Types of Wi-Fi Spoofing Attacks
There are numerous forms of Wi-Fi spoofing attacks, each with its own techniques and objectives. These are examples of prevalent Wi-Fi spoofing attacks:
- Evil Twin Attack
- Man-in-the-middle Attack
- Neighbor Spoofing
- IP Spoofing
Evil Twin Attack
The creation of a fake Wi-Fi network that has the same identity along with various configurations as a real Wi-Fi connection is referred to as an Evil Twin assault. The hacker creates a rogue wireless access point (AP) and assigns it the identical SSID as the legitimate connection.
Once the device used by the victim joins the fake network, the hacker may spy on the individual’s online activity and obtain confidential information. Wi-Fi Pineapple, an established wireless tracking system, serves as one of the instruments and techniques that may be employed in this type of attack.
Man-in-the-middle Attack
An MITM attack involves inserting oneself among the device being attacked and the internet so as to spy on and capture private information from the individual’s internet traffic. An attack using MITM employing Wi-Fi spoofing might be carried out by creating a bogus Wi-Fi network to which the device being targeted connects.
Once the victim is connected to the phoney network, an intruder may monitor their internet traffic and obtain confidential information. A number of methods and tools, like spoofing of ARP, DNS forging, and HTTPS tampering can be used to carry out this sort of attack.
Neighbor Spoofing
This involves a spoofing attack in which a hacker pretends to be someone you recognize or who resides nearby and gains exposure to every bit of your private information. The assailant, on the other hand, will disguise his identity and act as your neighbors, providing them an advantage. Several callers may impersonate bank officials at the branch in which you maintain an account and then approach you to request private or sensitive data, such as an online password (OTP).
IP Spoofing
The technique of establishing an IP address using bogus Source IP information is known as IP spoofing. This type of spoofing attack is used when an attacker wishes to mask their Internet Protocol (IP) address when making requests or seeking information.
The false internet protocol (“IP”) will seem to be from a trustworthy source, while the genuine source will remain operational. In order to mask the true source, hackers will use this spoofing method to perform attacks such as DDoS on the intended device or targeted organization.
Due to the fact that this attack happens at the network’s surface, the user will remain ignorant that their IP address has been modified. Botnets make IP spoofing attacks straightforward for attackers to execute.
Signs of a Spoofed Wi-Fi Network to Look for
Here are several signs that indicate that a Wi-Fi connection has been spoofed:
- The Wi-Fi connection’s network name (SSID) is unexpected or different from what you expected.
- Unlike in the past, the wireless internet connection is now requiring a password to access.
- The Wi-Fi connection is of poor quality, or the signal is feeble.
- On the internet connection with the same name, there are several “Free Wi-Fi” networks.
- The Wi-Fi connection is either unprotected or does not have a lock symbol.
- The network using Wi-Fi requests personal details before authorizing a connection.
- The URL of the login page being prompted by the Wi-Fi network is not congruent with the authentic website.
- It appears that neighboring devices are experiencing difficulty in establishing a link to the wireless fidelity signal.
- The wireless network is experiencing intermittent or periodic disconnections.
- The Wi-Fi connection is running slow than usual or has abnormally high traffic.
If you observe any of the above alert signs, steer clear of linking to the Wi-Fi connection and substitute a network that is safe. In the event of a suspected network breach, it is imperative to promptly alert the appropriate network administrators or designated personnel. It is highly advisable to employ a Virtual Private Network (VPN) in order to safeguard against Wi-Fi spoofing endeavors and fortify the security of your online information.
Do’s and Don’ts for Protection Against Wi-Fi Spoofing Attacks
Wi-Fi deception attacks pose a significant risk to your privacy and online safety. Do the following to safeguard yourself from these attacks:
Do’s:
- To avoid Wi-Fi spoofing assaults, secure your web browsing activity using a reputable VPN.
- Prior to joining to a Wi-Fi, particularly a public Wi-Fi network, verify the network’s name and details.
- Employ a Wi-Fi connection that employs WPA2 or other suitable security protocols.
- Utilize the most recent security upgrades to maintain the integrity of your software and hardware.
- Use two-step verification whenever possible to increase the security of your online accounts.
- To prevent your devices from joining to unsecured wireless networks by itself, deactivate automated wireless connections on the devices you use.
- Scan your bank records and online platforms frequently for any unusual activity.
- Utilize strong and unique passwords for each of your online accounts.
- Switch off Wi-Fi on your electronic devices when not in use, particularly in public places.
- Inform oneself and your loved ones on how to avoid Wi-Fi deception attacks.
Don’ts:
- Avoid using vulnerable or inadequately protected Wi-Fi connections.
- When connecting to a network, refrain from entering sensitive information such as your debit or credit card number or Social Security card number.
- Do not open files from shady recipients or visit shady URLs.
- Using a free Wi-Fi connection, you should never view sensitive information such as bank or health records.
- Do not utilize preset or easily guessed credentials for your wireless network or internet accounts.
- Do not keep your electronic gadgets unsupervised in public areas, particularly if they are connected to Wi-Fi.
- Do not assume that all wireless Internet connection secure and trustworthy.
Steps to Take if You Suspect a Wi-Fi Spoofing Attack
In the event that you suspect that you have fallen prey to Wi-Fi spoofing, it is imperative that you undertake the following measures to safeguard both yourself and your sensitive data:
Detach from the network: In the event of suspected Wi-Fi compromise, it is imperative to expeditiously sever the connection. It is advisable to modify your spot or network configuration in the event that you are connected to an unsecured wireless network.
Update your credentials: Every one of your Online accounts require fresh passwords, particularly those that you viewed via the questionable Wi-Fi network. Use a unique, robust passcode for each account.
Review your accounts: Examine your financial statements and online accounts for suspicious activity. In the event of detecting any anomalous behavior, it is recommended to promptly inform your financial institution and the relevant authorities.
Search for malware: It is recommended to conduct a malware analysis to scrutinize your device for any malicious applications that might have been downloaded and executed during the cyber attack.
Communicate with the vendor of the wireless internet network: If you suspect that a free Wi-Fi connection has been compromised, notify the Wi-Fi service provider.
Try out a credit monitoring service: In the event of suspected compromise of personal data, it is recommended to consider enlisting the services of a credit monitoring service to maintain vigilance against potential fraudulent activity.
Stay vigilant: Be aware of any suspicious activity on your online profiles or devices, and report it to the appropriate authorities.
Measures for Mitigating the Damage of a Wi-Fi Spoofing Attack
There are actions you may do if you’ve been the victim of a Wi-Fi spoofing assault to limit the damage and protect your sensitive data. Utilizing methods of authentication besides passwords for accessing your accounts, such fingerprints or an actual security key, is an approach called becoming passwordless. This may help keep your accounts safe regardless of your password is stolen.
Using an 802.1X certification, which authorizes both the wireless network and the user, is another option for creating a secure Wi-Fi connection. A powerful safety solution that may help lower the likelihood of future attacks and stop unauthorized network access is certificate-based authentication (CBA).
Extensible Authentication technology-Transport Layer Security (EAP-TLS), a password-free authentication technology based on certificates, is used by CBA. Since certificates can be kept in the cloud, EAP-TLS is largely cloud-based, which makes it a more feasible choice for consumers.
Along with the above-mentioned precautions, it is advised that you regularly back up your important data and make sure your software and security programmes are up to current. By doing so, you may mitigate the impact of any potential data loss and halt subsequent intrusions. You might safeguard your private data and yourself against the effects of a Wi-Fi spoofing attack by according to these recommendations.
Eliminate Wi-Fi Spoofing With SecureW2’s Cloud PKI Services
SecureW2 is a cloud-based security system that promises to decrease the danger of Wi-Fi spoofing attacks by providing robust encryption and secure authentication protocols. SecureW2’s Cloud PKI services encrypt all data transferred over Wi-Fi networks by using certificates and 802.1X EAP-TLS authentication.
In the event of an adversarial actor attempting to obstruct the data, the encryption mechanism in place will effectively prevent any unauthorized access or modification. In addition, it is recommended that network managers implement user partitioning based on access privileges, maintain a comprehensive inventory of network members and devices, and enforce strict access control policies to ensure that only authorized users can gain access to all applications, leveraging the robust onboarding services provided by SecureW2.
Organizations may dramatically reduce the risk of Wi-Fi spoofing attacks and protect critical data from unauthorized access by using SecureW2’s Cloud PKI services. Additionally, these security precautions aid in ensuring adherence to industry regulations and standards like HIPAA and PCI-DSS. With SecureW2’s solution, users may benefit from a smooth and secure Wi-Fi experience without worrying about the dangers of Wi-Fi spoofing attacks.
Contact us today to help protect your organization from Wi-Fi spoofing attacks.