2022 Security Analysis of PEAP-MSCHAPv2
The authentication protocol you use determines the strength of your organization’s security against the soaring number of cyberattacks these days. A protocol heavily dependent on passwords is always vulnerable to various cyberattacks. Even Microsoft Exchange has warned finance personnel to minimize the use of passwords as hackers easily target them during authentication for spray attacks.
Since you are here, the chances are fair that you are concerned about your company’s network security and looking to explore more robust defenses, and even if you are not, we suggest it’s high time you do so. While there are numerous protocols to choose from for your organization’s WPA2-Enterprise network security, the Extensible Authentication Protocols (EAP) are the most common.
Here we will thoroughly analyze the security mechanisms of one of the widely used authentication protocols, PEAP-MSCHAPv2, and help you evaluate the one best suited for your organization.
What is Extensible Authentication Protocol (EAP)?
The EAP authentication method uses an encrypted EAP tunnel to provide a safer path for communication between the client and server. In this tunnel, a chain of trust is established between the server certificate, intermediate certificate, and the client by validating the server with the help of the Root CA and the server certificate’s CN (Common Name).
There are many methods for authentication under the EAP protocol, but the most common methods used in modern wireless networking are:
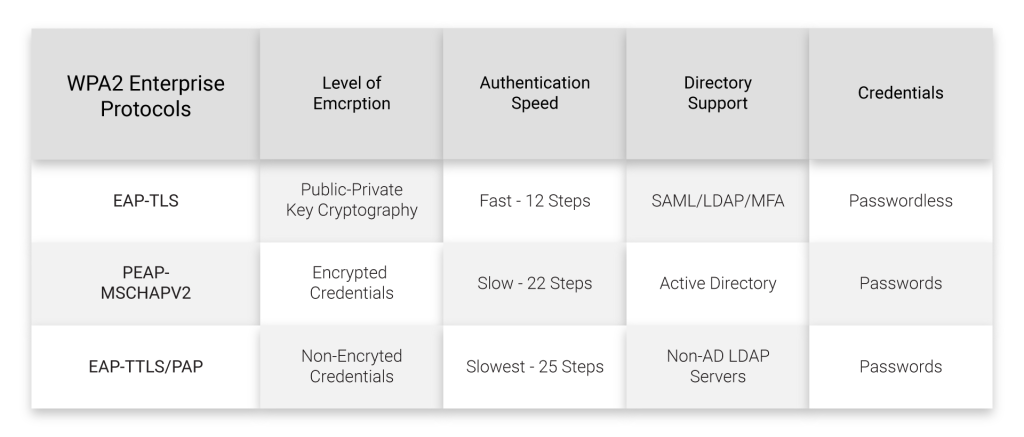
- EAP-TLS
- PEAP-MSCHAPV2
- EAP-TTLS/PAP
These protocols have varying levels of security, as illustrated in the table below:
High-Level Security Analysis of PEAP-MSCHAPv2
MSCHAPv2 is a Point-to-Point Protocol (PPP) that provides a standardized technique for moving multi-protocol datagrams across point-to-point links. For creating and setting various network-layer protocols, PPP offers an extensible Link Control Protocol and a series of Network Control Protocols (NCPs).
MS-CHAPv2 is basically the second iteration of the challenge-handshake mutual authentication protocol. Subsequent breakthroughs in encryption technology have rendered older versions like MS-CHAP-V1 obsolete. However, standard CHAP and MS-CHAP-V1 are both compatible with MS-CHAP-V2 except in some exceptional cases.
How does MSCHAPv2 work?
In LCP option 3, Authentication Protocol, MS-CHAP-V2 is activated by negotiating CHAP Algorithm 0x81. A peer challenge and an authenticator answer are overlayed onto the “Response” and “Success” packets to facilitate mutual authentication between peers.
The term “challenge-handshake” sums up how MSCHAPv2 functions. The remote access server challenges a user when they authenticate to the network. The client simultaneously transmits its own challenge to the server.
The server must demonstrate that it knows the user’s password by answering the client’s challenge. The client cuts off the connection automatically if the server cannot accomplish this.
The server concurrently authenticates both the user’s device and the server. Doing so ensures that the user only connects to the correct server and that all participating devices have mutual trust.
Evolution of MSCHAPv2 to PEAP-MSCHAPv2
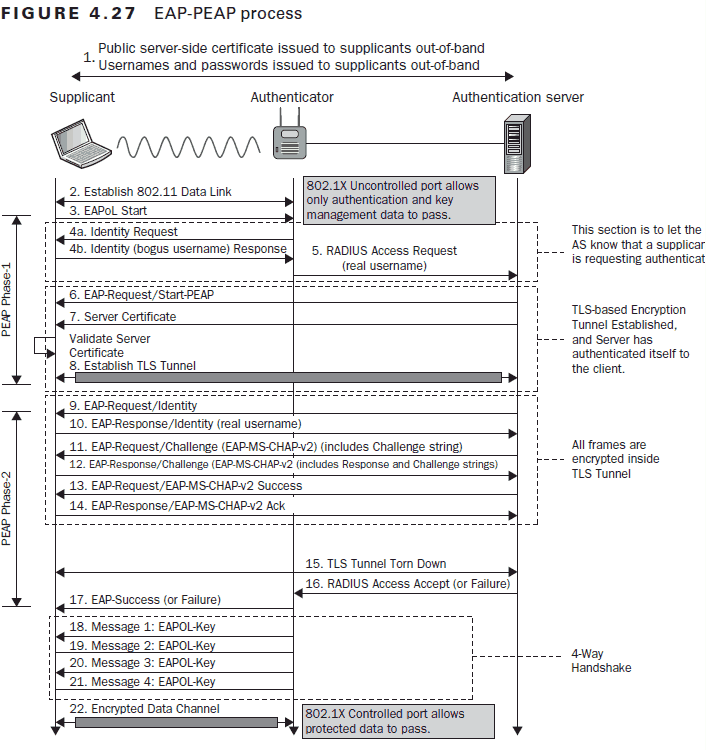
Since it was clear that MSCHAPv2’s encryption technique was insecure due to the usage of passwords, employing more secure encryption looked like a straightforward remedy. Thus, MSCHAPv2 became PEAP-MSCHAPv2 once transport layer security (also known as TLS) was added to it.
The TLS handshake is a process that involves communication and negotiation between the client and server in the sessions to perform the data exchange using encrypted keys. In this, both the peer and server must agree on the TLS protocol and cipher suite to verify digital certificates.
PEAP-MSCHAPv2 still uses the same vulnerable MD4 hashing algorithm as its predecessor, MSCHAPv2. However, TLS has been added to secure further the credentials sent during the handshake procedure.
Even with the addition of TLS, it is self-evident that PEAP-MSCHAPv2 is not a protocol one can rely upon in the long term. So let’s look at some of the drawbacks of PEAP-MSCHAPv2 and how they can be minimized in the subsequent sections.
Drawbacks of PEAP-MSCHAPv2
Microsoft’s advice for defending devices depends on the usage of server certificate validation. This protocol is active when a user tries to connect to the network. The RADIUS server possesses a recognized and trustworthy certificate created by the IT department or a public Certificate Authority. Server certificate validation is integral to security when using PEAP-MSCHAPv2.
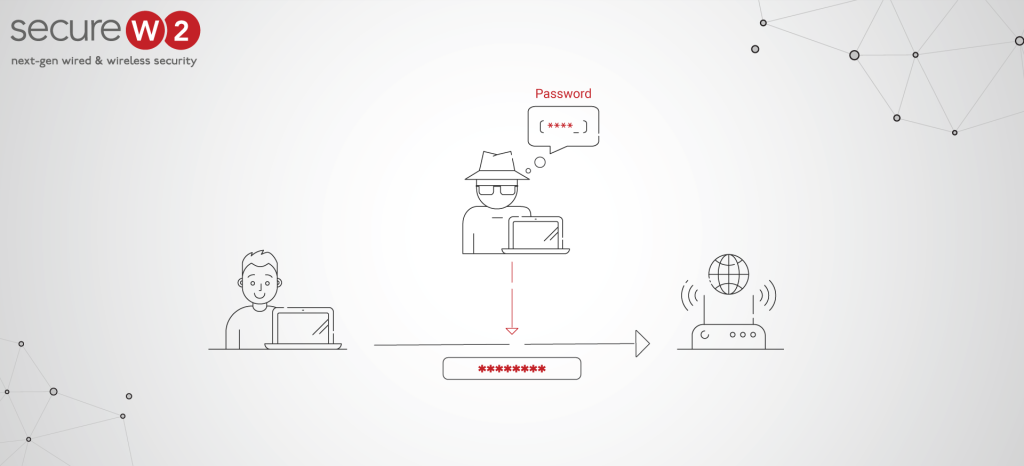
By confirming that the RADIUS server has the trusted certificate, which attests to the legitimacy of the network and will connect the device to the network, server certificate validation eliminates over-the-air credential theft. Users and devices can have their Active Directory or LDAP credentials stolen by a Man-in-the-middle attack if the server certificate is not verified.
When doing MITM, the attacker often configures an Evil Twin Access Point, and a RADIUS server spoofs the target SSID and broadcasts a potent signal to deceive victims’ devices into connecting to a malicious SSID.
When doing MITM, the attacker often configures an Evil Twin Access Point, and a RADIUS server spoofs the target SSID and broadcasts a potent signal to deceive victims’ devices into connecting to a malicious SSID.
You might struggle to accurately configure the server certificate validation procedure on your own since it is device-specific and complex. Users who manually configure their own devices run the danger of overlooking server certificate verification and unintentionally trusting malicious networks.
Best Substitute for PEAP-MSCHAPv2
EAP-TLS authentication is a certificate-based authentication system that utilizes X.509 digital certificates instead of credentials, providing an extra degree of cryptographic security. Asymmetric cryptography is an advanced cryptographic infrastructure that securely exchanges encrypted information publicly between two parties without the fear of interception.
Unlike symmetric encryption, where the exchange of private keys is mandatory to initiate communication between two parties, asymmetric encryption uses two pairs of public and private keys separately. The strength of the encryption makes it impossible to crack without knowing the hidden private key, so even intercepted communication is safe from prying eyes.
Benefits of EAP-TLS
The main advantages of EAP-TLS that stand out from the other protocols are:
- Improved authentication performance
- Modern cloud integrations
- Simpler user experience
Improved Authentication Performance
EAP-TLS is more suited for large organizations with many authentication events because its authentication flow is simpler than the alternatives. There are fewer chances for the RADIUS server to get overloaded and drop a connection, ultimately leading to a better user experience.
Having fewer authentication steps also means you can authenticate the network faster, leading to a better user experience.
Modern Cloud Integrations
One of the most significant benefits of EAP-TLS is that it can be extended to modern cloud infrastructures like Azure AD and Okta. Other auth protocols like MSCHAPv2/PAP were designed for on-premise environments and lack the support or rigor necessary for today’s cloud environment.
Simpler User Experience
Since EAP-TLS primarily deals with certificates, there is hardly any scope of downsides of passwords, like password reset policies. If you choose a proficient certificate authority, then even the certificate management will be fully automatic and hassle-free for your enterprise.
Why Isn’t EAP-TLS More Widely Used?
Despite the fact that EAP-TLS significantly increases network security, we have seen some reluctance to deploy it because of this uncertainty and its reputation for complexity.
Users may become frustrated if you need them to configure their devices for EAP-TLS all at once, even your help desk employees. An excellent strategy is to shift gradually, migrating user groups one at a time instead of everyone at once.
Also, While working to increase network security is a great aim, your network will be useless if your users cannot access it. Continue supporting PEAP/TTLS/PAP and EAP-TLS on a single SSID to ease the transition.
You also need a high level of specialized knowledge while configuring a PKI, and connecting them to multiple platforms for last-mile distribution might be challenging. These PKIs seem to have problematic management on a per daily basis.
Each of these problems is addressed by the JoinNow suite. You don’t need specialized knowledge to utilize the JoinNow Connector PKI because it is a SaaS platform. In fact, integrating your infrastructure and configuring our PKI can easily be done in as little as 90 seconds.
Smooth Onboarding to Superior EAP-TLS
You must have realized that passwords have been a primary attack vector for cyberattacks in recent years. Moving away from password-based authentication may be the most impactful decision toward enhanced security for any enterprise.
EAP-TLS protocol, with its certificate-based authentication, is a notch above the others with its superior cryptographic protection. You just need a capable PKI and a reliable RADIUS solution to ease the entire EAP-TLS onboarding process. Securew2, with its managed cloud PKI, has helped many organizations switch to digital certificates with EAP-TLS.
Additionally, we provide several cutting-edge onboarding options for managed and unmanaged devices for businesses of all sizes. Our dedicated support team is always eager to assist you in this journey of going passwordless with the EAP-TLS protocol. Trust us when we say that they are incredibly knowledgeable in what they do.
You can book a call with us or check out our pricing page to see if SecureW2’s onboarding solutions fit the authentication needs of your organization.