
The Only Guide You’ll Need to LDAP Authentication
Your organization’s network is full of vital data you need to operate on a day-to-day basis. Chances are, you store information regarding sensitive customer details, financial documents, and even personnel files. Failing to have some sort of authentication process guarding your network is like leaving your house unlocked, and this is why protocols like LDAP authentication exist.
LDAP, which stands for Lightweight Directory Access Protocol, is a protocol or “language” that can be used to query directories for user and device information. Many use it to authenticate users and ensure only authorized people access a network. Read about how one of our customers uses Active Directory, an IDP that uses LDAP, along with our onboarding software to make it easy for users to self-enroll for digital certificates. We think it’s important to understand how these protocols work, so we’ll be dissecting LDAP authentication further in this guide.
What is LDAP Authentication?
Before we get into the meat and potatoes of LDAP authentication, let’s start with an introduction to it. As you know, LDAP is a protocol that allows users to search a directory for user information. Such information includes things like:
- Users
- Groups
- Devices
An LDAP server is a server that can contain the aforementioned information and is compatible with the LDAP protocol. It’s an integral part of the authentication process because it contains the information needed to verify that a user or device can access a given resource.
Imagine LDAP authentication this way: a user tries to log onto an application. That application “speaks” LDAP. To confirm the user has the right to log on, the application talks to the LDAP server and verifies the user’s username and password. We’ll go into more detail about how the authentication process works from start to finish next.
How Does LDAP Authentication Work?
With LDAP authentication, there are two critical components: the LDAP server and the client/application authenticating with the server. The process begins when a user logs into an application or resource that is compatible with LDAP. This is called the LDAP client.
Examples of potential LDAP clients are numerous. It can be a workplace application like a ticketing system, access to an email server, Wi-Fi access, or other common professional applications.
The user enters their username and password into the LDAP client. As the user attempts to log in, the LDAP client sends their credentials and an authentication request to the LDAP server. The LDAP server holds information pertaining to the validity of the user’s credentials, as well as what group they are in.
Assuming the user is authorized, the LDAP server grants them access. They are then able to complete logging into the application. If the credentials do not match what the LDAP server has on record, the user is denied access.
How to Configure LDAP Authentication
LDAP with Active Directory
Nowadays, one of the most common use cases for LDAP is with Microsoft Active Directory, which is an Identity Provider (IDP) that uses LDAP. Because these two things are used so commonly together that their terminology is sometimes used interchangeably, we’ll discuss the configuration of LDAP if you’re using Active Directory (AD).
The good news is that you don’t really have to do anything to make sure your AD is using LDAP. LDAP is a protocol naturally used by Active Directory.
What we will show you is how you can leverage this type of infrastructure for use with SecureW2 solutions to strengthen your network security.
LDAP with SecureW2 Cloud RADIUS and Managed PKI
LDAP authentication, despite its wide use, has many flaws. One issue is that the credentials are often sent in clear text, which means that hackers can easily intercept them and see exactly what the credentials are since they’re not encrypted.
SecureW2 has a solution that can combine with your LDAP server and strengthen your authentication: a vendor-neutral Cloud RADIUS server and managed PKI. Cloud RADIUS can heighten your network security by verifying users and administering role-based access depending on the groups in your Active Directory. A Public Key Infrastructure (PKI) like our MPKI can help you make the leap to secure certificate-based authentication so you can ditch the credentials.
Let’s take a look at how you can configure our Cloud RADIUS to work alongside our PKI and Active Directory while using LDAP.
- Navigate to the Identity Providers section under Identity Management.
- Click Add Identity Provider at the bottom of the panel.
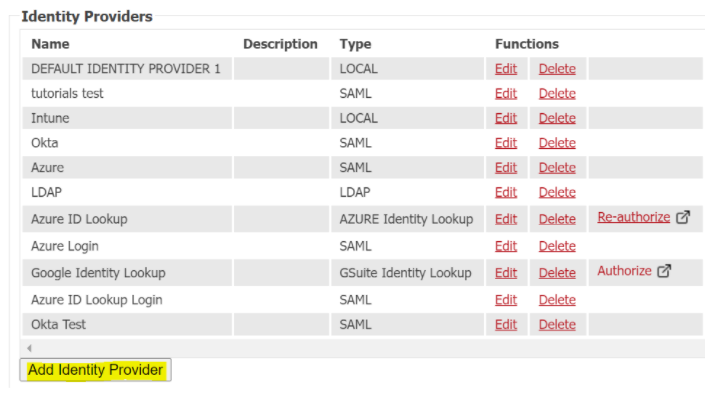
3. Enter the name you want to use for the server, a description, and choose the type from the dropdown. In this case, we’ll choose LDAP.
4. Click Save.
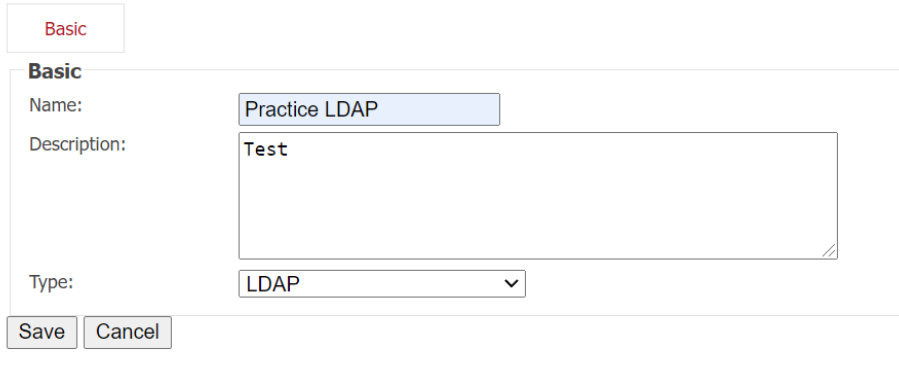
5. Now you’ll be brought to a screen with a few tabs across the top. We’ll need to connect to your LDAP server, so choose the tab that says Connections, then click Add Connection at the bottom of the panel.
6. For LDAP specifically, you’ll need to fill out several things: hostname, port number, subject and group base DN, admin DN, and password. Then click Update.
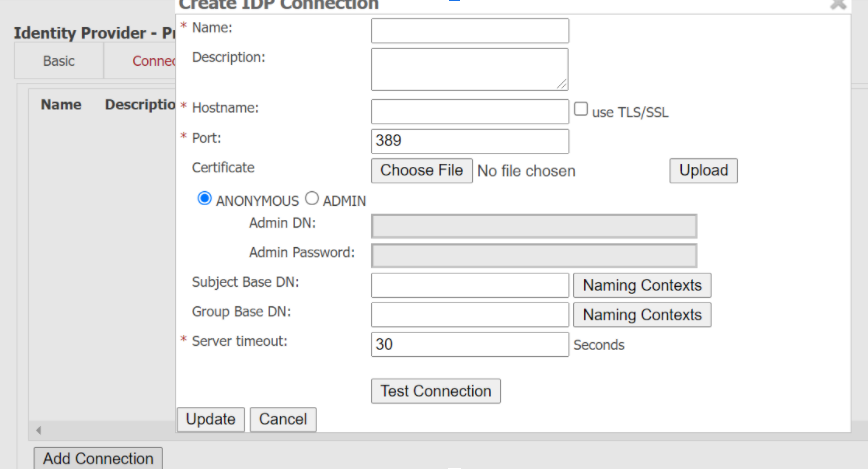
7. If you’re doing certificate-based authentication, you’ll need to complete attribute mapping. This is where you choose which attributes you want on your certificate template, such as the user’s email address. Click the Attribute Mapping tab to pop it open and add your desired attributes. You can click Next once you’re finished adding each attribute.
8. The final step is configuring your policy settings. This is where you segment users based on roles, such as by providing access to different resources based on which department a user is in. You can do this through the Policy Management panel in the management portal.
Is LDAP Still Relevant?
LDAP authentication has historically been used with on-premise servers and with the use of credentials as its authentication method. There are a few problems with this traditional setup.
The first one is the use of usernames and passwords. Although ubiquitous to this day, credentials simply aren’t secure enough to safeguard against hackers. There are an abundance of reasons why this is the case.
Usernames and passwords can be easy to steal through means such as social engineering or MITM attacks. Remembering passwords is also a frustrating experience for the end user, since they will need to regularly change passwords. Furthermore, password frustration leads to password mismanagement, which can be people reusing the same password or even sharing a password with friends, family, or coworkers.
LDAP’s second flaw is its ties to on-premise servers. As organizations migrate to the cloud, it’s becoming clearer that on-prem equipment just won’t cut it in the long run. It’s expensive, needs physical space, and needs physical security to prevent it from on-site threats such as people with malicious intent or power outages.
Regardless of the fact that traditional LDAP is simultaneously less secure and more outdated than many alternatives, there are still plenty of organizations using it to this day. If you’re a Windows-heavy business, chances are, you’re familiar with Active Directory and have used it in the past if you’re not using it now. And where there’s Active Directory, there’s LDAP – much like the proverbial smoke from the fire.
There are services available today that can help integrate LDAP with cloud-based infrastructure. Our Cloud RADIUS and managed PKI can communicate with LDAP servers like Active Directory to bring certificate-based authentication to your business.
However, our powerful RADIUS and managed PKI can also be used alongside more cloud-compatible alternatives, such as OAuth and SAML. Such protocols were made to be used in a cloud environment, which means they are more viable in what will surely be a cloud-based future.
Leave LDAP Behind and Step into the Cloud-Based Future with Cloud RADIUS
Although it’s still prevalent, LDAP has its share of flaws. If you want to migrate your infrastructure to the cloud, then you’ll need to leave LDAP behind at some point. This is something our unique Cloud RADIUS can help you with.
Even if you’re not at a point where you can abandon LDAP entirely, our Cloud RADIUS solution still applies to you. Cloud RADIUS can smooth your transition to the cloud by connecting your cloud-hosted infrastructure to your on-prem components. Check out how our solutions helped this customer bridge the gap between on-prem infrastructure and the cloud.