
Is PEAP Authentication Secure in 2023?
Authentication protocols play a critical role in wireless network security by protecting sensitive data and providing secure access. PEAP is a highly prevalent protocol for establishing specific authentication channels for wireless network users. In this article, we’ll evaluate different versions of PEAP, with a particular focus on PEAP-MSCHAPv2. Our primary objective is to highlight potential security weaknesses that hackers might exploit due to the rise in technological advancements.
Read this case study of one of our Fortune 100 customers moving their network to EAP-TLS authentication with digital certificates.
What is PEAP and How Does It Work?
PEAP is an authentication protocol that establishes a secure authentication channel for users connecting to wireless networks, providing fast access. PEAP is an acronym for Protected Extensible Authentication Protocol. It is an extension of EAP, which stands for Extensible Authentication Protocol. EAP is a widely used framework for implementing various authentication methods in network communications.
The PEAP protocol encapsulates the EAP authentication process within a TLS tunnel secured through encryption. Employing encapsulation, a protected pathway is created to facilitate the transfer of authentication credentials, such as usernames and passwords, between the client device and the authentication server.
Several versions of PEAP are available, but PEAP-MSCHAPv2 is extensively used because Microsoft popularized it. This version is deemed user-accessible and pragmatic as it predominantly employs passwords for authentication. It is imperative to bear in mind that the security of PEAP-MSCHAPv2 relies heavily on the exact configuration and strict adherence to security protocols.
Uncovering Vulnerabilities of Different PEAP Versions
PEAP includes numerous versions created over time to improve security and offer various authentication choices. The various PEAP versions, along with their associated vulnerabilities, are:
- EAP-MD5
- EAP-LEAP
- PEAP-MsCHAPv2
- EAP-TLS
- EAP-TTLS
- EAP-GTC
EAP-MD5
EAP-MD5, a version of the Protected Extensible Authentication Protocol (PEAP), was initially implemented for secure port-based authentication in wired infrastructures and subsequently adapted for wireless environments.
The current authentication mechanism is unidirectional, allowing the client to transmit its authentication data to the server without verifying its identity. This creates a susceptibility to malicious attacks such as Evil Twin and Man-in-the-Middle.
Additionally, the transmission of the username occurs in an unencrypted format, rendering it vulnerable to social engineering breaches. The MD5 hashing algorithm in EAP-MD5 is deemed weak and encompasses multiple security concerns, thereby rendering it susceptible to unauthorized access.
EAP-LEAP
EAP-LEAP, a Cisco proprietary version of PEAP, has been rendered obsolete due to its susceptibility to security breaches. The system was discovered to have vulnerabilities, leading to the creation of ASLEAP, a tool designed to take advantage of the vulnerabilities in the LEAP authentication mechanism. As a result of identified security weaknesses, the utilization of EAP-LEAP has been discontinued.
PEAP-MSCHAPv2
PEAP-MSCHAPv2, or PEAPv2, is the widely adopted version of PEAP currently in use. MSCHAPv2, the Microsoft Challenge Handshake Authentication Protocol version 2, is the authentication mechanism employed.
The current version boasts enhanced security measures relative to its forerunners and utilizes authentication protocols based on passwords. The technology in question has achieved widespread adoption across diverse operating systems and is frequently leveraged in wireless networks of enterprise-caliber.
EAP-TTLS
EAP-TTLS, also known as Tunneled Transport Layer Security, is a highly secure authentication protocol that amalgamates the robustness of EAP-TLS with the versatility of other authentication techniques.
The system implements a robust two-factor authentication mechanism whereby the user initiates a secure communication channel with the server via TLS and subsequently deploys supplementary authentication protocols like MSCHAPv2 within the channel. The current version boasts strong security measures while maintaining compatibility with various authentication mechanisms.
EAP-GTC
EAP-GTC, also known as Generic Token Card, is a variant of PEAP that offers a comprehensive structure for authentication based on tokens. The system enables the utilization of various tickets, including smart cards or USB tokens, to ensure secure authentication.
The EAP-GTC protocol exhibits high adaptability and can effectively accommodate diverse token variants, making it a fitting choice for scenarios requiring token-centric authentication.
EAP-TLS
EAP-TLS, also known as Transport Layer Security, is a version of PEAP that facilitates bidirectional authentication between the client and server through digital certificates. The implementation of certificates enables mutual authentication between the client and server, thereby ensuring a robust security posture. EAP-TLS is commonly acknowledged as a highly secure authentication technique in PEAP.
The principal advantage in terms of security that EAP-TLS networks offer is the capability to execute server certificate validation. To ensure secure server certificate validation, it is imperative that both the client and server validate their respective identities. This is particularly relevant for devices configured for EAP-TLS authentication, as it mitigates the risk of a spoofed AP being mistaken for the authentic one.
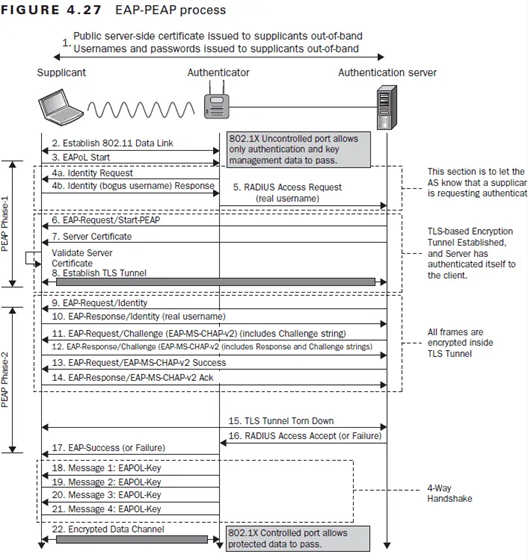
Below are the criteria used to assess the effectiveness of each 802.1X authentication technique. Every authentication method underwent individual evaluation, comprehensively assessing its attributes and effectiveness.
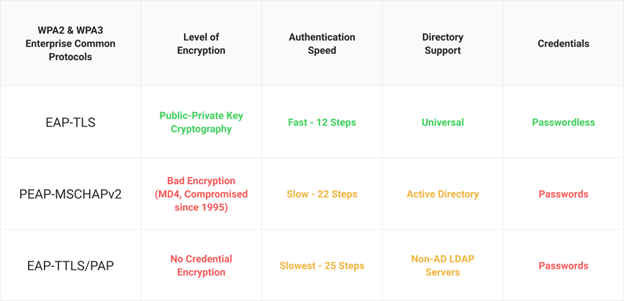
The Vulnerability of PEAP to Man-in-the-Middle (MITM) Attacks
MITM attacks pose a significant threat to the security of PEAP. In this type of cyber assault, a hacker leverages a counterfeit wireless access point (AP) to emulate an authentic network. When unsuspecting users connect to a fraudulent access point, the perpetrator can intercept their data and collect their login credentials, potentially obtaining illegal entry into the network’s assets.
In the next section, we’ll discuss the intricacies of the attack vector, the efficacy of server certificate validation in mitigating the vulnerability, and the perils of Man-in-the-Middle (MITM) attacks in various contexts.
The Role of Server Certificate Validation
Validating server certificates is crucial in mitigating Man-in-the-Middle (MITM) attacks. Proper implementation entails the client device’s validation of the server’s digital certificate during PEAP authentication.
This authentication process ensures the end user communicates with a legitimate access point, not fraud. Due to the lack of server certificate validation, the client device cannot authenticate the access point, rendering it vulnerable to Man-in-the-Middle (MITM) attacks.
Setting Up an MITM Attack
The perpetrator frequently leverages specialized software or tools to construct a fraudulent access point to execute a PEAP MITM assault. The technologies mentioned above allow the malicious actor to emulate the characteristics of a bona fide access point and duplicate the network identifier.
The perpetrator employs techniques such as ARP (Address Resolution Protocol) or DNS (Domain Name System) spoofing to hijack and modify network traffic after configuring the counterfeit access point. The threat actor can acquire authentication credentials and achieve unlawful entry into the network by interposing between the client and the access point.
MITM Attacks at Work or in Public Spaces
Potential PEAP MITM attacks may occur in diverse environments, such as corporate workspaces and communal locations like cafes. A likely threat actor near the target network within a workplace environment can establish a rogue access point, thereby luring unsuspecting employees to connect.
The interception of employee credentials and subsequent unauthorized access to sensitive business resources is a common tactic employed by cyber attackers who exploit users’ trust in well-known network names.
Given the high volume of individuals utilizing public Wi-Fi networks, it is imperative to acknowledge that public domains such as coffee shops present a prime opportunity for malicious actors to execute Man-in-the-Middle (MITM) attacks. Malicious actors can construct fraudulent access points utilizing names that resemble legitimate networks, enticing unsuspecting users to establish connections. Upon a successful relationship, the perpetrator can intercept passwords and potentially breach any co-owned confidential or private information.
The Shift From PEAP-MSCHAPv2 to EAP-TLS
In the current dynamic digital landscape, organizations are increasingly aware of the imperative to enhance the security of their wireless networks. Due to its enhanced security features, EAP-TLS (Extensible Authentication Protocol-Transport Layer Security) is becoming the preferred authentication method for many, leading to a shift from PEAP-MSCHAPv2. The impetus behind this modification is the desire to enhance security measures and optimize the authentication process.
The implementation of EAP-TLS involves the utilization of digital certificates in lieu of the PEAP-MSCHAPv2 protocol, which relies on passwords. This approach enhances the overall security posture and eliminates the vulnerabilities associated with password-based authentication. EAP-TLS enables organizations to establish a dependable and effective authentication framework, enhancing network security and optimizing user experience.
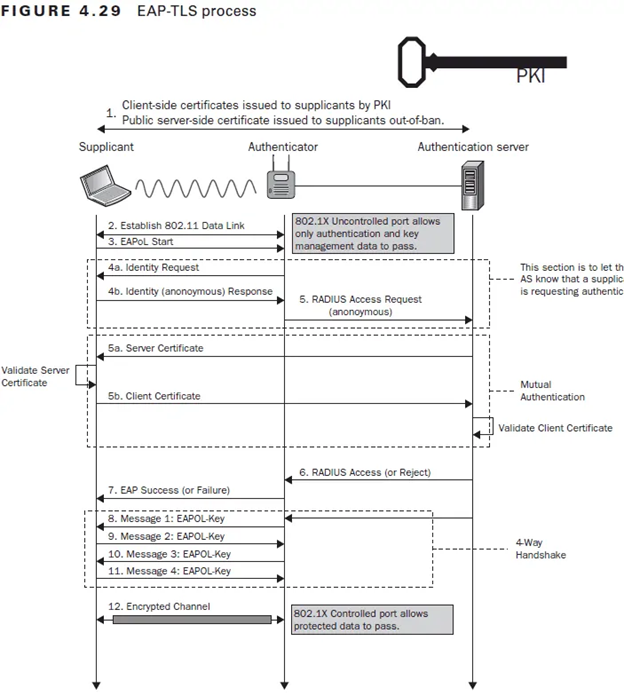
Embrace the Security of EAP-TLS with SecureW2
As we delve into the intricacies of PEAP’s vulnerabilities in 2023, it is evident that organizations and users must opt for more robust alternatives to safeguard their wireless networks. EAP-TLS stands out as a viable solution in the realm of cybersecurity. Using certificates instead of passwords is a superior security measure offered by EAP-TLS. This approach enhances security protocols and effectively eliminates the potential for credential theft.
Implementing EAP-TLS can significantly mitigate the security threats associated with traditional password-based authentication methods. It is highly recommended for administrators to consider this approach. SecureW2 has been a leading innovator in the field of cybersecurity, particularly in the implementation of EAP-TLS and the use of certificates to enhance password-free online security. SecureW2 has demonstrated the efficacy and reliability of EAP-TLS in safeguarding wireless networks through a track record of successful deployments.
JoinNow PKI and JoinNow Connector are cutting-edge SecureW2 solutions that enable a seamless transition to EAP-TLS authentication. The implementation of JoinNow PKI streamlines certificate management, while the integration of JoinNow Connector with pre-existing infrastructure ensures uninterrupted communication. Integrating Cloud RADIUS with these products results in an elevated level of security and a more efficient implementation of EAP-TLS authentication.
Secure your network with SecureW2’s expertise in implementing EAP-TLS. Contact us today for a secure and seamless authentication solution.